Credit Cornerstone

For most businesses, the customer experience is at the heart of every strategy. Debt collection shouldn’t be different. Here’s why: 21% of visits to...

Sophisticated criminals work hard to create convincing, verifiable personas they can use to commit fraud. Here are the 3 main ways fraudsters manufacture synthetic...

With 81% of Americans having a social media profile, you may wonder if social media insights can be used to assess credit risk. When...

Juniper Research recently recognized Experian as a Fraud Detection and Prevention Market Leader in its Online Payment Fraud Whitepaper. Juniper also shared important market...

Despite rising concerns about identity theft, most Americans aren’t taking basic steps to make it harder for their information to be stolen, according to...

Synthetic identity fraud is on the rise across financial services, ecommerce, public sector, health and utilities markets. The long-term impact of synthetic identity remains...

Our national survey found that consumers struggle to find a credit card that meets their needs. They say there are too many options and...

The collections space has been migrating from traditional mail and outbound calls to electronic payment portals, digital collections and virtual negotiators. Now that collectors...

With 1 in 6 U.S. residents being Hispanic, now is a great time for financial institutions to reflect on their largest growth opportunity. Here...
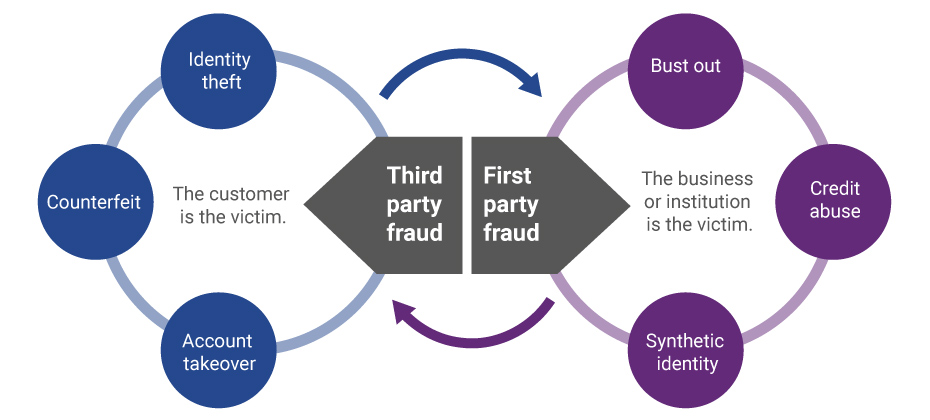
Evolution of first-party fraud to third Third-party and first-party schemes are now interchangeable, and traditional fraud detection practices are less effective in fighting these...
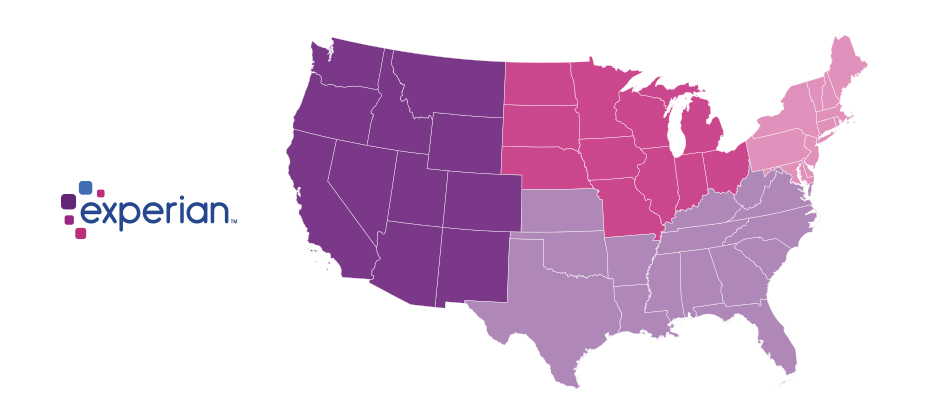
We recently analyzed millions of online transactions from the first half of 2017 to identify fraud attack rates. Here are the top 3 riskiest...

Cybersecurity cannot be successful if siloed. The entire organization must be part of the effort. Take these steps to ensure a more engaged relationship...

There’s a consensus that too many C-suite executives are disengaged with their organization’s cybersecurity efforts. That indifference can seriously hamper an organization’s ability to...

Leadership and Cybersecurity Multiple studies suggest many executives aren’t as engaged as they should be when ensuring their organizations are prepared to mitigate and...

There’s no shortage of headlines alluding to a student loan crisis. But is there a crisis brewing or is this just a headline grab?...
