Public Sector
Public Sector

The U.S. Senate Banking Committee passed a financial regulatory relief bill (S. 2155) in December 2017 aimed at reducing regulatory burdens on community banks, credit unions and smaller regional banks. Committee Chairman Senator Mike Crapo (R-ID), sponsored the bill, which has strong bipartisan support, with 23 cosponsors (11 Republicans and 12 Democrats and an independent). The package is likely to be considered by the full Senate in early 2018. The legislation includes two provisions related to consumer credit reporting. Both were adopted, in part, in reaction to the Equifax data breach. As the bill moves through the legislative process during 2018, it will be important for all participants in the consumer credit ecosystem to be aware of the potential changes in law. One provision deals with fraud alerts and credit freezes for consumers and the other deals with how medical debt is processed for veterans who seek medical treatment outside the VA system. Credit Freezes The bill amends the Fair Credit Reporting Act to provide consumers with the ability to freeze/unfreeze credit files maintained by nationwide credit reporting agencies at no cost, and would extend the time period for initial fraud alerts from 90 days to one year. The credit freeze provisions would also establish a process for parents and guardians to place a freeze on the file of a minor at no cost. The bill would require the nationwide credit reporting agencies to create webpages with information on credit freezes, fraud alerts, active duty alerts and pre-screen opt-outs and these pages would be linked to the FTC’s existing website, www.IdentityTheft.gov. The credit freeze and minor freeze provisions would preempt State laws and create a national standard. Protections for Veterans The bill also incorporates a provision that would prohibit credit bureaus from including debt for health-care related services that the veteran received through the Department of Veterans Affairs’ Choice Program. The provision would cover debt that the veteran incurred in the previous year, as well as any delinquent debt that was fully paid or settled. The legislation would require a consumer reporting agency to delete medical debt if it receives information from either the veteran or the VA that the debt was incurred through the Veteran’s Choice Program. What’s next The bill now awaits consideration before the full Senate. Senate Majority Leader Mitch McConnell has said that the bill is a “candidate for early consideration” in 2018, but the exact timing of floor debate has yet to be scheduled. Once the package passes the Senate, it will need to be reconciled with the regulatory relief package that was passed by the House last spring.

The sheer range of dynamic and emerging fraud tactics can impede agencies from achieving security. These threats must be met with a variety of identity proofing and management tactics. Without monitoring, performance assessments and tuning, a singular and static identity proofing strategy can be exposed by evolving schemes and the use of high-quality compromised identity data. Traditional verification and validation parameters alone are simply too obtuse and can be circumvented easily by those with criminal intent. Static rules based on overly simplistic verification and validation checks can be outsmarted by intelligent fraudsters. Conversely, those same static rules must also have built-in mechanisms to accommodate true-name users who initially may not meet that criteria for identity proofing. Vast and diverse user populations, more arduous — and arguably more difficult to achieve — digital identity guidelines put forth by the National Institute of Standards and Technology, and operational constraints all pose significant challenges for government. But there are ways for government to modernize identity proofing successfully. Modern fraud and identity strategies There are many emerging trends and best practices for modern fraud and identity strategies, including: Applying right-sized fraud and identity proofing solutions. To reduce user friction or service disruption and manage fraud risk appropriately, agencies need to apply fraud mitigation strategies. Such strategies reflect the cost, measured risk and level of confidence, as well as compliance needed, for each interaction. This is called right-sizing the fraud solution. For example, agencies can cater a fraud solution that ensures a seamless experience when a citizen is calling a service center, versus an online interaction, versus a face-to-face one. Maintaining a universal view of the user. Achieved by employing a diverse breadth and depth of data assets and applied analytics, this tactic is the core of modern fraud mitigation and identity management. Knowing the individual user extends beyond a traditional 360-degree view. It means having knowledge of a person’s offline and online behavior, not only with your agency, but also with other agencies with which that user has a relationship. Expanding user view through a blended ecosystem. Increasingly, agencies are participating in a blended ecosystem — working with vendors, peer agencies and partners. There exists a collaborative culture in identity and fraud management that doesn’t exist in more competitive commercial environments. Fraudsters easily share information with one another, so those combatting it need to share information as well. Achieving agility and scale using service-based models. More agencies are adopting service-based models that provide greater agility and response to dynamic fraud threats, diverse population changes, and evolving compliance requirements or guidance. Service-based identity proofing provides government agencies the benefit of regularly updated data assets, analytics and expertise in strategy design. These assets are designed to respond to fraud or identity intelligence observed across various markets and industries, often protecting proactively rather than reactively. Future-proofing fraud solution choices. Technical and operational resources are always in relatively short supply compared to demand. Agencies need the ability to “code once” in order to expand and evolve their fraud strategies with ease. Future-proofing solutions must also be combined with an ever-changing set of identity proofing requirements and best practices, powered by a robust and innovative marketplace of service providers. The future of identity proofing in the public sector is more than just verifying individual identities. New standards in digital identity proofing are a responsive result of mass data compromise and failures in legacy techniques. Achieving compliant and confident identity assurance requires a layered approach, flexibly designed and orchestrated to accommodate diverse identity assertions, evidence, and contextual invocation of technologies and data assets. Government must now use risk-based approaches and mitigation strategies to identity threats quickly and determine the type of fraud before damage is done. Download our recent report in which we discuss the primary challenges of identity proofing in the public sector and what modernization of identity proofing looks like.

The data to create synthetic identities is available. And the marketplace to exchange and monetize that data is expanding rapidly. The fact that hundreds of millions of names, addresses, dates of birth, and Social Security numbers (SSNs) have been breached in the last year alone, provides an easy path for criminals to surgically target new combinations of data. Armed with an understanding of the actual associations of these personally identifiable information (PII) elements, fraudsters can better navigate the path to perpetrate identity theft, identity manipulation, or synthetic identity fraud schemes on a grand scale. Using information such as birth dates and addresses in combination with Social Security numbers, criminals can target new combinations of data to yield better results with lower risk of detection. Some examples of this would be: identity theft, existing account takeovers, or the deconstruction and reconstruction of those PII elements to better create effective synthetic identities. Experian has continued to evolve and innovate against fraud risks and attacks with an understanding of attack rates, vectors, and the shifting landscape in data availability and security. In doing so, we’ve historically operated under the assumption that all PII is already compromised in some way or is easily done so. Because of this, we employ a layered approach, providing a more holistic view of an identity and the devices that are used over time by that identity. Relying solely on PII to validate and verify an identity is simply unwise and ineffective in this era of data compromise. We strive to continuously cultivate the broadest and most in-depth set of traditional, innovative and alternative data assets available. To do this, we must enable the integration of diverse identity attributes and intelligence to balance risk, while maintaining a positive customer experience. It’s been quite some time since the use of basic PII verification alone has been predictive of identity risk or confidence. Instead, validation and verification is founded in the ongoing definition and association of identities, the devices commonly used by those individuals, and the historical trends in their behavior. Download our newest White Paper, Synthetic Identities: Getting real with customers, for an in-depth Experian perspective on this increasingly significant fraud risk.

Earlier this week, Javelin Strategy & Research announced its inaugural edition of the 2017 Identity Proofing Platform Awards. We were honored to see CrossCore as the leader – taking the award for the best overall identity proofing platform. According to the report, “Experian’s identity proofing platform is a strong performer in every category of Javelin’s FIT model. It is functional. It is innovative. And, most important, it is tailored toward the advisory’s expectations. The comprehensive nature of CrossCore makes it the market-leading solution for identity proofing.” It’s harder than ever to confidently identify your customers in today’s digital economy. You have lots of vendor solutions to choose from in the identity proofing space. And, now Javelin has made it much easier for you to select the partner that is right for your needs. Javelin’s newly minted Identity Proofing Platform Scorecard assesses current capabilities in the market to help you make that decision. And they have done a lot of the heavy lifting, looking across 23 vendors and scoring them based on three categories of their FIT model – functional, innovative, and tailored. Protecting customers is a priority for you – and for us. Here at Experian, we have a range of capabilities to help businesses manage identity proofing, and our CrossCore platform brings them all together. We launched CrossCore last year, with the goal of making the industry’s fraud and identity solutions work better for everyone. CrossCore delivers a future-proof way to modify strategies quickly, catch fraud faster, improve compliance and enhance the customer experience. We’re proud of the work we’ve done so far, integrating our products as well as adding more than 10 partners to the program. We’re pleased to see so many of our partners included in Javelin’s report. We’re working closely with our clients to pull in more partner capabilities, and further enhance our own platform to create a layered approach that supports a risk-based, adaptable strategy. As highlighted in the Javelin report, a reliance on traditional identity verification approaches are no longer sufficient or appropriate for digital channels. With CrossCore, our clients can choose the capabilities they want, when they want them, to dial in the right confidence level for each and every transaction. This is because CrossCore supports a layered approach to managing risk, allowing companies to connect multiple disparate services through a common access point. We are committed to making it easier for you to protect consumers against fraud. CrossCore is helping us all do just that.

Everyone loves a story. Correction, everyone loves a GOOD story. A customer journey map is a fantastic tool to help you understand your customer’s story from their perspective. Perspective being the operative word. This is not your perspective on what YOU think your customer wants. This is your CUSTOMER’S perspective based on actual customer feedback – and you need to understand where they are from those initial prospecting and acquisition phases all the way through collections (if needed). Communication channels have expanded from letters and phone calls to landlines, SMS, chat, chat bots, voicemail drops, email, social media and virtual negotiation. When you create a customer journey map, you will understand what channel makes sense for your customer, what messages will resonate, and when your customer expects to hear from you. While it may sound daunting, journey mapping is not a complicated process. The first step is to simply look at each opportunity where the customer interacts with your organization. A best practice is to include every department that interacts with the customer in some way, shape or form. When looking at those touchpoints, it is important to drill down into behavior history (why is the customer interacting), sociodemographic data (what do you know about this customer), and customer contact patterns (Is the customer calling in? Emailing? Tweeting?). Then, look at your customer’s experience with each interaction. Again, from the customer’s viewpoint: Was it easy to get in touch with you? Was the issue resolved or must the customer call back? Was the customer able to direct the communication channel or did you impose the method? Did you offer self-serve options to the right population? Did you deliver an email to someone who wanted an email? Do you know who prefers to self-serve and who prefers conversation with an agent, not an IVR? Once these two points are defined: when the customer interacts and the customer experience with each interaction, the next step is simply refining your process. Once you have established your baseline (right channel, right message, right time for each customer), you need to continually reassess your decisions. Having a system in place that allows you to track and measure the success of your communication campaigns and refine the method based on real-time feedback is essential. A system that imports attribute – both risk and demographic – and tracks communication preferences and campaign success will make for a seamless deployment of an omnichannel strategy. Once deployed, your customer’s experience with your company will be transformed and they will move from a satisfied customer to one that is a fan and an advocate of your brand.
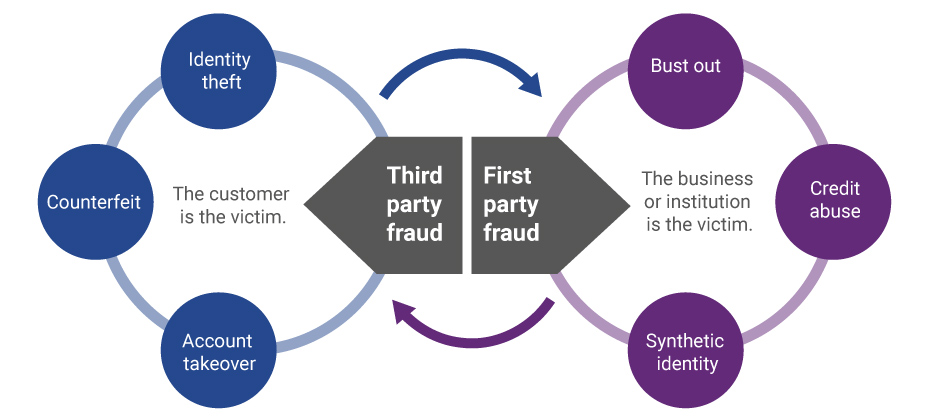
Evolution of first-party fraud to third Third-party and first-party schemes are now interchangeable, and traditional fraud detection practices are less effective in fighting these evolving fraud types. Fighting this shifting problem is a challenge, but it isn’t impossible. To start, incorporate new and more robust data into your identity verification program and provide consistent fraud classification and tagging. Learn more>

Millennials have long been the hot topic over the course of the past few years with researchers, brands and businesses all seeking to understand this large group of people. As they buy homes, start families and try to conquest their hefty student loan burdens, all will be watching. Still, there is a new crew coming of age. Enter Gen Z. It is estimated that they make up ¼ of the U.S. population, and by 2020 they will account for 40% of all consumers. Understanding them will be critical to companies wanting to succeed in the next decade and beyond. The oldest members of this next cohort are between the ages of 18 and 20, and the youngest are still in elementary school. But ultimately, they will be larger than the mystical Millennials, and that means more bodies, more buying power, more to learn. Experian recently took a first look at the oldest members of this generation, seeking to gain insights into how they are beginning to use credit. In regards to credit scores, the eldest Gen Z members sported a VantageScore® credit score of 631 in 2016. By comparison, younger Millennials were at 626 and older Millennials were at 638. Given their young age, Gen Z debt levels are low with an average debt-to-income at just 5.7%. Their tradelines largely consist of bankcards, auto and student loans. Their average income is at $33.8k. Surprisingly, there was a very small group of Gen Z already on file with a mortgage, but this figure was less than .5%. Auto loans were also small, but likely to grow. Of those Gen Z members who have a credit file, an estimated 12% have an auto trade. This is just the beginning, and as they age, their credit files will thicken, and more insights will be gained around how they are managing credit, debt and savings. While they are young today, some studies say they already receive about $17 a week in allowance, equating to about $44 billion annually in purchase power in the U.S. Factor in their influence on parental or household purchases and the number could be closer to $200 billion! For all brands, financial services companies included, it is obvious they will need to engage with this generation in not just a digital manner, but a mobile manner. They are being raised in an era of instant, always-on access. They expect a quick, seamless and customized mobile experience. Retailers have 8 seconds or less — err on the side of less — to capture their attention. In general, marketers and lenders should consider the following suggestions: Message with authenticity Maintain a long-term vision Connect them with something bigger Provide education for financial literacy and of course Keep up with technological advances. Learn more by accessing our recorded webinar, A First Look at Gen Z and Credit.

Mitigating synthetic identities Synthetic identity fraud is an epidemic that does more than negatively affect portfolio performance. It can hurt your reputation as a trusted organization. Here is our suggested 4-pronged approach that will help you mitigate this type of fraud: Identify how much you could lose or are losing today to synthetic fraud. Review and analyze your identity screening operational processes and procedures. Incorporate data, analytics and cutting-edge tools to enable fraud detection through consumer authentication. Analyze your portfolio data quality as reported to credit reporting agencies. Reduce synthetic identity fraud losses through a multi-layer methodology design that combats both the rise in synthetic identity creation and use in fraud schemes. Mitigating synthetic identity fraud>

On June 7, the Consumer Financial Protection Bureau (CFPB) released a new study that found that the ways “credit invisible” consumers establish credit history can differ greatly based on their economic background. The CFPB estimated in its May 2015 study "Data Point: Credit Invisibles" that more than 45 million American consumers are credit invisible, meaning they either have a thin credit file that cannot be scored or no credit history at all. The new study reviewed de-identified credit records on more than one million consumers who became credit visible. It found that consumers in lower-income areas are 240 percent more likely to become credit visible due to negative information, such as a debt in collection. The CFPB noted consumers in higher-income areas become credit visible in a more positive way, with 30 percent more likely to become credit visible by using a credit card and 100 percent more likely to become credit visible by being added as a co-borrower or authorized user on someone else’s account. The study also found that the percentage of consumers transitioning to credit visibility due to student loans more than doubled in the last 10 years. CFPB’s research highlights the need for alternative credit data The new study demonstrates the importance of moving forward with inclusion of new sources of high-quality financial data — like on-time payment data from rent, utility and telecommunications providers — into a consumer’s credit file. Experian recently outlined our beliefs on the issue in comments responding to the CFPB’s Request for Information on Alternative Data. As a brand, we have a long history of using alternative credit data to help lenders make better lending decisions. Extensive research has shown that there is an immense opportunity to facilitate greater access to fair and affordable credit for underserved consumers through the inclusion of on-time telecommunications, utility and rental data in credit files. While these consumers may not have a traditional credit history, many make on-time payments for telephone, rent, cable, power or mobile services. However, this data is not typically being used to enhance traditional credit files held by the nationwide consumer reporting agencies, nor is it being used in most third-party or custom credit scoring models. Further, new advances in financial technology and data analytics through account aggregation platforms are also integral to the credit granting process and can be applied in a manner to broaden access to credit. Experian is currently using account aggregation software to obtain consumer financial account information for authentication and income verification to speed credit decisions, but we are looking to expand this technology to increase the collection and utilization of alternative data for improving credit decisions by lenders. Policymakers should act to help credit invisible consumers While Experian continues to work with telecommunications and utility companies to facilitate the furnishing of on-time credit data to the nationwide consumer reporting agencies, regulatory barriers continue to exist that deter utility and telecommunications companies from furnishing on-time payment data to credit bureaus. To help address this issue, Congress is currently considering bipartisan legislation (H.R. 435, The Credit Access and Inclusion Act of 2017) that would amend the FCRA to clarify that utility and telecommunication companies can report positive credit data, such as on-time payments, to the nation' s credit reporting bureaus. The legislation has bipartisan support in Congress and Experian encourages lawmakers to move forward with this important initiative that could benefit tens of millions of American consumers. In addition, Experian believes policymakers should more clearly define the term alternative data. In public policy debates, the term "alternative data" is a broad term, often lumping data sources that can or have been proven to meet regulatory standards for accuracy and fairness required by both the Fair Credit Reporting Act and the Equal Credit Opportunity Act with data sources that cannot or have not been proven to meet these standards. In our comment letter, Experian encourages policymakers to clearly differentiate between different types of alternative data and focus the consumer and commercial credit industry on public policy recommendations that will increase the use of those sources of data that have or can be shown to meet legal and societal standards for accuracy, validity, predictability and fairness. More info on Alternative Credit Data More Info on Alternative Financial Services

The final day of Vision 2017 brought a seasoned group of speakers to discuss a wide range of topics. In just a few short hours, attendees dove into a first look at Gen Z and their use of credit, ecommerce fraud, the latest in retail, the state of small business and leadership. Move over Millennials – Gen Z is coming of credit age Experian Analytics leaders Kelley Motley and Natasha Madan gave audience members an exclusive look at how the first wave of Gen Z is handling and managing credit. Granted most of this generation is still under the age of 18, so the analysis focused on those between the ages of 18 to 20. Yes, Millennials are still the dominant generation in the credit world today, standing strong at 61 million individuals. But it’s important to note Gen Z is sized at 86 million, so as they age, they’ll be the largest generation yet. A few stats to note about those Gen Z individuals managing credit today: Their average debt is $12,679, compared to younger Millennials (21 to 27) who have $65,473 in debt and older Millennials (28 to 34) who sport $121,460. Given their young age, most of Gen Z is considered thin-file (less than 5 tradelines) Average Gen Z income is $33,000, and average debt-to-income is low at 5.7%. New bankcard balances are averaging around $1,574. As they age, acquire mortgages and vehicles, their debt and tradelines will grow. In the meantime, the speakers provided audience members a few tips. Message with authenticity. Think long-term with this group. Maintain their technological expectations. Build trust and provide financial education. State of business credit and more on the economy Moody’s Cris deRitis reiterated the U.S. economy is looking good. He quoted unemployment at 4.5%, stating “full employment is here.” Since the recession, he said we’ve added 15 million jobs, noting we lost 8 million during the recession. The great news is that the U.S. continues to add about 200,000 jobs a month, and that job growth is broad-based. Small business loans are up 10% year-to-date vs. last year. While there has been a tremendous amount of buzz around small business, he adds that most job creation has come from mid0size business (50 to 499 employees). The case for layered fraud systems Experian speaker John Sarreal shared a case study that revealed by layering on fraud products and orchestrating collaboration, a business can go from a string 75% fraud detection rate to almost 90%. Additionally, he commented that Experian is working to leverage dark web data to mine for breached identity data. More connections for financial services companies to make with mobile and social Facebook speaker Olivia Basu reinforced the need for all companies to be thinking about mobile. “Mobile is not about to happen,” she said. “Mobile is now. Mobile is everything. You look at the first half of 2017 and we’re seeing 40% of all purchases are happening on mobile devices.” Her challenge to financial services companies is to make marketing personal again, and of course leverage the right channels. Experian Sr. Director of Credit Marketing Scott Gordon commented on Experian’s ability to reach consumers accurately – whether that be through direct or digital delivery channels. A great deal of focus has been around person-based marketing vs. leveraging the cookie. -- The Vision conference was capped off with a keynote speech from legendary quarterback and Super Bowl MVP Tom Brady. He chatted about the details of this past season, and specifically the comeback Super Bowl win in February 2017. He additionally talked about leadership and what that means to creating a winning team and organization. -- Multiple keynote speeches, 65 breakout sessions, and hours of networking designed to help all attendees ready themselves for growing profits and customers, step up to digital, regulatory and fraud challenges, and capture the latest data insights. Learn more about Experian’s annual Vision conference.

In just a few short hours, Vision attendees immersed themselves into the depths of the economy, risk models, specialty finance data, credit invisibles, student loan data, online marketplace lending and more. The morning kicked off with one of the most respected and trusted macroeconomists in the U.S., Diane Swonk. With a rap sheet filled with advising central banks and multinational companies, Swonk treated a packed house to a look back on what has transpired in the U.S. economy since the Great Recession, as well as launching into current state and speculating on the months ahead. She described the past decade not as “lost, but rather lagging.” She went onto to say this past year was transitional, and while markets slowed slightly during the months leading up the U.S. presidential election, good things are happening: We’ve finally broken out of the 2% wage rut Recruiting on college campuses has picked up The labor force is growing Debt-to-income levels have returned to where they were prerecession and Investment is coming back. “I believe we’ll see growth over 2% this year,” said Swonk. Still, change is underway. She commented on how the way U.S. consumer spending is changing, and of course we’re seeing a restructuring in the retail space. While JC Penney announces store closings, you simultaneously see Amazon moving from “click to brick,” dabbling in the opening of some actual storefronts. Globally, she said the economy is the strongest it has been in eight years. She closed by noting there is a great deal of political change and unrest in the world today, but says, “Never underestimate our abilities when we tap our human capital.” -- More than 100 attendees filled a room to hear about the current trends and the future of online lending with featured guests from Oliver Wyman, Marlette Funding and Lending USA. While speakers commented on the “hiccup” in the space last year with some layoffs and mergers, volume has continued to double every year for the past several years with roughly $40 billion in cumulative originations today. Panelists discussed the use of alternative data to decision, channel bias, the importance of partnerships and how the market will see fewer and fewer players offering just one product specialty. “It is expensive to acquire customers, so you don’t just want to have one product to sell, but rather a range,” said Sharat Shankar of Lending USA. -- The numbers in the student lending universe are astounding. In a session focused on the U.S. student loan market, new Experian data reveals there is $1.49 billion in total student loan outstandings. In fact, total outstandings have grown 21% over the past four years, while the number of trades have only grown 4%. Costs are skyrocketing. The average balance per trade has grown 17% over the past four years. “We don’t ration education in this country,” said Joe DePaulo of College Ave. Student Loans. “We give everyone access to liquidity when it comes to federal student loans – and it’s not like that in other countries.” While DePaulo notes the access is great, offering many students the opportunity to obtain higher education, he says the problem is with disclosures. Guardians are often the individuals filling out the FAFSA, but the students inherit the loans. Students, he says, rarely understand how much their monthly payment will ultimately be after graduation. For every $10,000 in student loans, he says that will generally equate to a $100 monthly payment. -- Tomorrow, Vision attendees will be treated to more breakout sessions and a concluding keynote with legendary quarterback Tom Brady.

So many insights and learnings to report after the first full day of 2017 Vision sessions. From the musings shared by tech engineer and pioneer Steve Wozniak, to a panel of technology thought leaders, to countless breakout sessions on a wide array of business topics … here’s a look at our top 10 from the day. A mortgage process for the digital age. At last. In his opening remarks, Experian President of Credit Services Alex Lintner asked the audience to imagine a world when applying for a mortgage simply required a few clicks or swipes. Instead of being sent home to collect a hundred pieces of paper to verify employment, income and assets, a consumer could click on a link and provide a few credentials to verify everything digitally. Finally, lenders can make this a reality, and soon it will be the only way consumers expect to go through the mortgage process. The global and U.S. economies are stable. In fact, they are strong. As Experian Vice President of Analytics Michele Raneri notes, “the fundamentals and technicals look really solid across the countries.” While many were worried a year ago that Brexit would turn the economy upside down, it appears everything is good. Consumer confidence is high. The Dow Jones Index is high. The U.S. unemployment rate is at 4.7%. Home prices are up year-over-year. While there has been a great deal of change in the world – politically and beyond – the economy is holding strong. The rise of the micropreneur. This term is not officially in the dictionary … but it will be. What is it? A micropreneur is a business with 0 to 4 employees bringing in no more than $200k in annual revenue. But the real story is that numbers show microbusiness are improving on many fronts when it comes to contribution to the economy and overall performance compared to other small businesses. Keep an eye on these budding business people. Fraud is running fierce. Synthetic identity losses are estimated in the hundreds of millions annually, with 50% year-over year growth. Criminals are now trying to use credit cleaners to get tradelines removed from used Synthetic IDs. Oh, and it is essential for businesses to ready themselves for “Dark Web” threats. Experts advise to harden your defenses (and play offense) to keep pace with the criminal underground. As soon as you think you’ve protected everything, the criminals will find a gap. The cloud is cool and so are APIs. A panel of thought leaders took to the main stage to discuss the latest trends in tech. Experian Global CIO Barry Libenson said, “The cloud has changed the way we deliver services to our customers and clients, making it seamless and elastic.” Combine that with API, and the goal is to ultimately make all Experian data available to its customers. Experian President of Decision Analytics Steve Platt added, “We are enabling you to tap into what you need, when you need it.” No need to “rip and replace” all your tech. Expect more regulation – and less. A panel of regulatory experts addressed the fast-changing regulatory environment. With the new Trump administration settling in, and calls for change to Dodd-Frank and the Consumer Financial Protection Bureau (CFPB), it’s too soon to tell what will unfold in 2017. CFPB Director Richard Cordray may be making a run for governor of Ohio, so he could be transitioning out sooner than the scheduled close of his July 2018 term. The auto market continues to cruise. Experian’s auto expert, Malinda Zabritski, revealed the latest and greatest stats pertaining to the auto market. A few numbers to blow your mind … U.S. passenger cars and light trucks surpassed 17 million units for the second consecutive year Most new vehicle buyers in the U.S. are 45 years of age or older Crossover and sport utility vehicles remain popular, accounting for 40% of the market in 2016 – this is also driving up finance payments since these vehicles are more expensive. There are signs the auto market is beginning to soften, but interest rates are still low, and leasing is hot. Defining alternative data. As more in the industry discuss the need for alternative data to decision, it often gets labeled as something radical. But in reality, alternative data should be simple. Experian Sr. Director of Government Affairs Liz Oesterle defined it as “getting more financial data in the system that is predicted, validated and can be disputed.” #DeathtoPasswords – could it be a reality? It’s no secret we live in a digital world where we are increasingly relying on apps and websites to manage our lives, but let’s throw out some numbers to quantify the shift. In 2013, the average U.S. consumer had 26 online accounts. By 2015, that number increased to 118 online accounts. By 2020, the average person will have 207 online accounts. When you think about this number, and the passwords associated with these accounts, it is clear a change needs to be made to managing our lives online. Experian Vice President David Britton addressed his session, introducing the concept of creating an “ultimate consumer identity profile,” where multi-source data will be brought together to identify someone. It’s coming, and all of us managing dozens of passwords can’t wait. “The Woz.” I guess you needed to be there, but let’s just say he was honest, opinionated and notes that while he loves tech, he loves it even more when it enables us to live in the “human world.” Too much wonderful content to share, but more to come tomorrow …

Good job, check. Shared interests, check. Chemistry, check. He seems like a perfect 10. Both of you enjoy your first date and while getting ready for the second, you dare to imagine that turning into another and another, and possibly happily ever after. Then one decidedly unromantic question comes to mind: What is his credit score? Reviewing a potential partner’s credit score and report is important to many singles who are looking for lasting love. According to Bankrate.com, 42 percent of Millennials said that knowing someone’s credit score would affect their desire to date them, slightly more than 40 percent of Gen Xers and 41 percent of Baby Boomers. They may be on to something. Research shows that knowing someone’s credit history and sense of financial responsibility could save people time – and potential heartache. A UCLA study about money and love shows a very strong link between high credit scores and long-lasting relationships. People with drastically different credit scores may experience more financial stress down the road, placing a burden on a relationship. An Experian report reveals 60 percent of people believe it’s important for their future spouse to have a good credit score, and 25 percent of people from the UCLA study were willing to leave a partner with poor credit before marriage so they aren’t held back. While that three-digit number doesn't tell a person’s whole financial story, it can reveal financial habits that could impact your life. Banks are wary of making loans to borrowers with tarnished scores, typically 660 and below. A low score could quash dreams of buying a home, and result in steep interest rates, up to 29 percent, for credit cards, car financing and other unsecured loans. A mid-range credit score can also hurt an application for an apartment and drive up the cost of mobile phone plans and auto insurance. Eight states have passed laws limiting employers’ ability to use credit checks when assessing job candidates, yet 13 percent of employers surveyed by the Society of Human Resource Management performed credit checks on all job applicants. Talking spending styles and revealing credit scores sooner rather than later in a relationship isn’t necessarily comfortable. But it may help you decide whether you have compatible financial outlooks and practices.

Experian shares five trends and twists coming over the next 12 months, that could push new boundaries and in many cases improve the customer experience as it pertains to the world of credit and finance.
Which part of the country has bragging rights when it comes to sporting the best consumer credit scores? Drum roll please … Honors go to the Midwest. In fact, eight of the 10 cities with the highest consumer credit scores heralded from Minnesota and Wisconsin. Mankato, Minn., earned the highest ranking with an average credit score of 708 and Greenwood, Miss., placed last with an average credit score of 622. Even better news is that the nation’s average credit score is up four points; 669 to 673 from last year and is only six points away from the 2007 average of 679, which is a promising sign as the economy continues to rebound. Experian’s annual study ranks American cities by credit score and reveals which cities are the best and worst at managing their credit, along with a glimpse at how the nation and each generation is faring. “All credit indicators suggest consumers are not as ‘credit stressed’ — credit card balances and average debt are up while utilization rates remained consistent at 30 percent,” said Michele Raneri, vice president of analytics and new business development at Experian. As for the generational victors, the Silents have an average 730, Boomers come in with 700, Gen X with 655 and Gen Y with 634. We’re also starting to see Gen Z emerge for the first time in the credit ranks with an average score of 631. Couple this news with other favorable economic indicators and it appears the country is humming along in a positive direction. The stock market reached record highs post-election. Bankcard originations and balances continue to grow, dominated by the prime borrower. And the housing market is healthy with boomerang borrowers re-emerging. An estimated 2.5 million Americans will see a foreclosure fall of their credit report between June 2016 and June 2017, creating a new pool of potential buyers with improved credit profiles. More than 12 percent who foreclosed back in the Great Recession have already boomeranged to become homeowners again, while 29 percent who experienced a short sale during that same time have also recently taken on a mortgage. “We are seeing the positive effects of economic recovery with the rise in income and low unemployment reflected in how Americans are managing their credit,” said Raneri. Which means all is good in the world of credit. Of course there is always room for improvement, but this year’s 7th annual state of credit reveals there is much to be thankful for in 2016.