Fraud & Identity Management

Experian has been named one of the 10 participants, and only credit bureau, in the initial rollout of the SSA's new eCBSV service.

What do movie actors Adam Sandler and Hugh Grant, jazz singer Michael Bublé, Russian literary giant Leo Tolstoy, and Colonel Sanders, the founder of KFC, have in common? Hint, it’s not a Nobel Prize for Literature, a Golden Globe, a Grammy Award, a trademark goatee, or a “finger-lickin’ good” bucket of chicken. Instead, they were all born on September 9, the most common birth date in the U.S. Baby Boom According to real birth data compiled from 20 years of American births, September is the most popular month to give birth to a child in America – and December, the most popular time to make one. With nine of the top 10 days to give birth falling between September 9 and September 20, one may wonder why the birth month is so common. Here are some theories: Those who get to choose their child’s birthday due to induced and elective births tend to stay away from the hospital during understaffed holiday periods and may plan their birth date around the start of the school year. Several of the most common birth dates in September correspond with average conception periods around the holidays, where couples likely have more time to spend together. Some studies within the scientific community suggest that our bodies may actually be biologically disposed to winter conceptions. While you may not be feeling that special if you were born in September, the actual differences in birth numbers between common and less common birthdays are often within just a few thousand babies. For example, September 10, the fifth most common birthday of the year, has an average birth rate of 12,143 babies. Meanwhile, April 20, the 328th most common birthday, has an average birth rate of 10,714 newborns. Surprisingly, the least common birthdays fall on Christmas Eve, Christmas Day and New Year’s Day, with Thanksgiving and Independence Day also ranking low on the list. Time to Celebrate – but Watch out! Statistically, there’s a pretty good chance that someone reading this article will soon be celebrating their birthday. And while you should be getting ready to party, you should also be on the lookout for fraudsters attempting to ruin your big day. It’s a well-known fact that cybercriminals can use your birth date as a piece of the puzzle to capture your identity and commit identity theft – which becomes a lot easier when it’s being advertised all over social media. It’s also important for employers to safeguard their organization from fraudsters who may use this information to break into corporate accounts. While sharing your birthday with a lot of people could be a good or bad thing depending on how much undivided attention you enjoy – you’re in great company! Not only can you plan a joint party with Michelle Williams, Afrojack, Cam from Modern Family, four people I went to high school with on Facebook and a handful of YouTube stars that I’m too old to know anything about, but there will be more people ringing in your birthday than any other day of the year! And that’s pretty cool.

The fact that the last recession started right as smartphones were introduced to the world gives some perspective into how technology has changed over the past decade. Organizations need to leverage the same technological advancements, such as artificial intelligence and machine learning, to improve their collections strategies. These advanced analytics platforms and technologies can be used to gauge customer preferences, as well as automate the collections process. When faced with higher volumes of delinquent loans, some organizations rapidly hire inexperienced staff. With new analytical advancements, organizations can reduce overhead and maintain compliance through the collections process. Additionally, advanced analytics and technology can help manage customers throughout the customer life cycle. Let’s explore further: Why use advanced analytics in collections? Collections strategies demand diverse approaches, which is where analytics-based strategies and collections models come into play. As each customer and situation differs, machine learning techniques and constraint-based optimization can open doors for your organization. By rethinking collections outreach beyond static classifications (such as the stage of account delinquency) and instead prioritizing accounts most likely to respond to each collections treatment, you can create an improved collections experience. How does collections analytics empower your customers? Customer engagement, carefully considered, perhaps comprises the most critical aspect of a collections program—especially given historical perceptions of the collections process. Experian recently analyzed the impact of traditional collections methods and found that three percent of card portfolios closed their accounts after paying their balances in full. And 75 percent of those closures occurred shortly after the account became current. Under traditional methods, a bank may collect outstanding debt but will probably miss out on long-term customer loyalty and future revenue opportunities. Only effective technology, modeling and analytics can move us from a linear collections approach towards a more customer-focused treatment while controlling costs and meeting other business objectives. Advanced analytics and machine learning represent the most important advances in collections. Furthermore, powerful digital innovations such as better criteria for customer segmentation and more effective contact strategies can transform collections operations, while improving performance and raising customer service standards at a lower cost. Empowering consumers in a digital, safe and consumer-centric environment affects the complete collections agenda—beginning with prevention and management of bad debt and extending through internal and external account resolution. When should I get started? It’s never too early to assess and modernize technology within collections—as well as customer engagement strategies—to produce an efficient, innovative game plan. Smarter decisions lead to higher recovery rates, automation and self-service tools reduce costs and a more comprehensive customer view enhances relationships. An investment today can minimize the negative impacts of the delinquency challenges posed by a potential recession. Collections transformation has already begun, with organizations assembling data and developing algorithms to improve their existing collections processes. In advance of the next recession, two options present themselves: to scramble in a reactive manner or approach collections proactively. Which do you choose? Get started

Digital channels undoubtedly create convenient experiences for consumers. We have the luxury of applying for loans or creating investment accounts from the comfort of home. However, the same opportunities are available to fraudsters. Fraudsters continue to find creative and innovative ways to expose vulnerabilities across all types of businesses. They prey on inexperienced or low-bandwidth teams that have not invested in the appropriate fraud tools in the past. Despite the imminent fraud risk involved, both consumers and businesses continue to embrace digital channels. With 90 percent of consumers worldwide conducting personal banking online, how do we protect these digital platforms with finite resources? A leading digital financial services company was forced to address this question when they experienced a large-scale fraud attack. But they weren’t in this fight alone. Download the full case study to see how our risk analyst used FraudNet to prevent millions of dollars in fraudulent funding. Client: A leading digital financial services company that operates with zero in-person branches with more than 7,000 employees Challenge/Objective: In October 2018, fraudsters deployed a large-scale, scripted attack against a North American financial services company. The fraud team was extremely understaffed. The fraud team was unable to detect and respond to the attack quickly. The fraudulent account opening activities eventually blended into account takeovers. Resolution: Our risk analyst worked quickly to analyze the geolocation, velocity and device rules firing within FraudNet for Account Opening. By having these rules in place, FraudNet was able to flag and outsort thousands of suspicious applications. Despite being a small team, the fraud investigators were able to work efficiently within the FraudNet workbench and review the true, high-risk applications. Results: Thanks to our risk analyst’s quick remediation and the FraudNet proprietary device rules: 23,800 fraudulent applications were outsorted for review. An estimated $35.7 million in fraudulent funding was prevented. However, the fight against fraud is ongoing. Our risk analyst continues to work closely with the fraud team to develop an effective strategy to prepare against future attacks.

If you’ve seen an uptick in photos of friends and celebrities looking older with wrinkles on your social media feeds, you’re not alone. A new free photo editor has taken the internet by a storm, featuring an AI-powered image-altering application that allows users to see their “future self.” All you have to do is upload a single photo (or few) from your camera roll to be enhanced. While this may seem like harmless fun, the app is now making headlines over increased privacy concerns about what occurs behind the scenes once users submit their selfies. Red flags were raised when multiple alleged negative implications were connected to the app – including the app’s ownership and the potential risk that the app downloaded a user’s entire photo album onto their database. In fact, the privacy concerns also prompted Democratic Party officials to implore federal agencies, including the FBI, “to look into the potential national security and privacy risks the phone app poses to the United States.” Since then, the app’s creators have addressed these concerns, stating most of the photo processing occurs in the cloud and most photos are deleted within 48 hours. Additionally, the only photos uploaded are ones that have been personally submitted by the user. Regardless, a database of user-submitted photos could be seen as a goldmine to fraudsters. In a time where personal and biometric data (including facial recognition) are some of the key ways to validate security, it’s important for consumers to be aware of how and where they’re sharing their data, whether it’s for an age-progression photo app, or their financial accounts. Consumers, businesses, financial institutions – everyone – should exhibit caution and take measures to ensure personal information remains secure and is not being used for nefarious reasons. While consumers may be aware that businesses are collecting data, companies should take steps to form digital trust with transparency. This could be achieved by: Educating consumers on how their data is being used Effectively communicating privacy policies and service terms more concisely Helping consumers feel in control of their information To learn more about research that indicates a shift to advanced authentication methods (including biometrics), fraud trends and how to combat them, download our e-book. Download Now
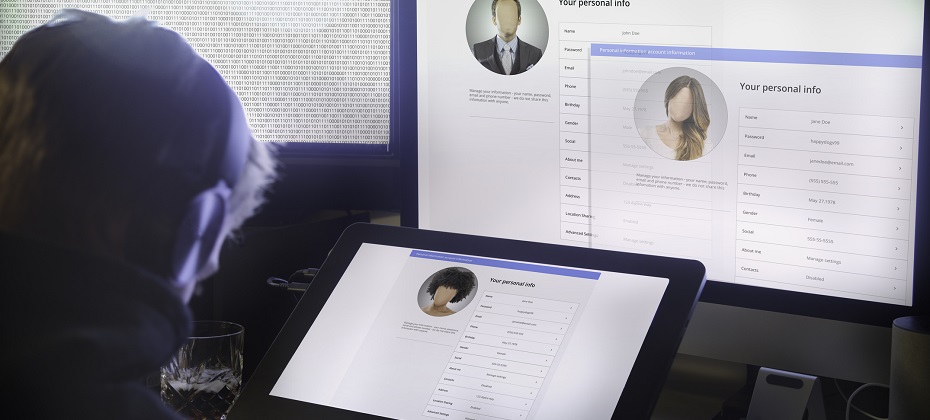
Friend or foe? Sophisticated criminals put a great deal of effort into creating convincing, verifiable personas (AKA synthetic identities). Once the fictional customer has embedded itself in your business, everything from the acquisition of financial instruments to healthcare benefits, utility services, and tax filings and refunds become vulnerable to synthetic identity fraud. Information attached to synthetic IDs can run several levels deep and be so complete that it includes public record data, credit information, documentary evidence and social media profiles that may even contain photo sets and historical details intended to deceive—all complicating your efforts to identify these fake customers before you do business with them. See real-world examples of how synthetic identity fraud is souring various markets – from auto and healthcare to financial services and public sector – in our tip sheet, Four common synthetic scenarios. Stopping synthetic ID fraud — at the door and thereafter. There are efforts underway in the market to collectively improve your ability to identify, shut down and prevent synthetic identities from entering your portfolio. This overall trend is great news for the future, but there are also near-term solutions you can apply to protect your business starting now. While it’s important to identify synthetic identities when they knock on your door, it’s just as important to conduct regular portfolio checkups to prevent negative impacts to your collections efforts. Every circumstance has its own unique parameters, but the overarching steps necessary to mitigate fraud from synthetic IDs remain the same: Identify current and near-term exposure using targeted segmentation analysis. Apply technology that alerts you when identity data doesn’t add up. Differentiate fraudulent identities from those simply based on bad data. Review front- and back-end screening procedures until they satisfy best practices. Achieve a “single view of the customer” for all account holders across access channels—online, mobile, call center and face-to-face. The right tools for the job. In addition to the steps mentioned above, stopping these fake customers from entering and then stealing from your organization isn’t easy—but with the right tools and strategies, it is possible. Here are a few of our top recommendations: Forensics Isolate and segment identities based on signals received during early account pathing, from both individuals and their device. For example, even sophisticated fraud networks can’t mimic natural per-device user interaction because these organizations work with hundreds or thousands of synthetic identities using just a few devices. It’s highly unlikely that multiple geographically separate account holders would share the same physical device. High-risk fraud scores Not all synthetic identity fraud manifests the same way. Using sophisticated logic and unique combinations of data, a high-risk fraud score looks at a consumer’s credit behavior and credit relationships over time to uncover previously undetectable risk. These scores are especially successful in detecting identities that are products of synthetic identity farms. And by targeting a specific data set and relationships, you can maintain a frictionless customer experience and reduce false positives. Analytics Use a solution that develops models of bad applicant behavior, then compares and scores your portfolio against these models. There isn’t a single rule for detecting fraudulent identities, but you can develop an informed set of rules and targeted models with the right service partner. Cross-referencing models designed to isolate high-risk identity theft cases, first-party or true-name fraud schemes, and synthetic identities can be accomplished in a decisioning strategy or via a custom model that incorporates the aggregate scores and attributes holistically. Synthetic identity detection rules These specialized rules consist of numerous conditions that evaluate a broad selection of consumer behaviors. When they occur in specific combinations, these behaviors indicate synthetic identity fraud. This broad-based approach provides a comprehensive evaluation of an identity to more effectively determine if it’s fabricated. It also helps reduce the incidence of inaccurately associating a real identity with a fictitious one, providing a better customer experience. Work streams Address synthetic identities confidently by applying analytics to work streams throughout the customer life cycle: Credit risk assessment Know Your Customer/Customer Identification Program checks Risk-based identity proofing and authentication Existing account management Manual reviews, investigations and charge-offs/collections activities Learn more about these tools and others that can help you mitigate synthetic identities in our white paper, Synthetic identities: getting real with customers. If your organization is like most, detecting SIDs hasn't been your top priority. So, there's no time to waste in preventing them from entering your portfolio. Criminals are highly motivated to innovate their approaches as rapidly as possible, and it’s important to implement a solution that addresses the continued rise of synthetic IDs from multiple engagement points. With the right set of analytics and decisioning tools, you can reduce exposure to fraud and losses stemming from synthetic identity attacks from the beginning and across the customer life cycle. We can help you detect and mitigate these fake customers before they become delinquent. Learn more

You can do everything you can to prepare for the unexpected. But similar to how any first-time parent feels… you might need some help. Call in the grandparents! Experian has extensive expertise and has been around for a long time in the industry, but unlike your traditional grandparents, Experian continuously innovates, researches trends, and validates best practices in fraud and identity verification. That’s why we explored two prominent fraud reports, Javelin’s 2019 Identity Fraud Study: Fraudsters Seek New Targets and Victims Bear the Brunt and Experian’s 2019 Global Identity and Fraud Report — Consumer trust: Building meaningful relationships online, to help you identify and respond to new trends surrounding fraud. What we found – and what you need to know – is there are trends, technology and tactics that can help and hinder your fraud-prevention efforts. Consider the many digital channels available today. A full 91 percent of consumers transacted online in 2018. This presents a great opportunity for businesses to serve and develop relationships with customers. It also presents a great opportunity for fraudsters as well – as almost half of consumers have experienced a fraudulent online event. Since the threat of fraud is not impacting customers’ willingness to transact online, businesses are held responsible for adapting and evolving to not only protect their customers, but to secure their bottom line. This becomes increasingly important as fraudsters continue to target and expose vulnerabilities across inexperienced lines of businesses. Or, how about passwords. Research has shown that both businesses and consumers have greater confidence in biometrics, but neither is ready to stop using passwords. The continued reliance on traditional authentication methods is a delicate balance between security, trust and convenience. Passwords provide both authentication and consumer confidence in the online experience. It also adds friction to the user experience – and sometimes aggravation when passwords are forgotten. Advanced methods, like physical and behavioral biometrics and device intelligence, are gaining user confidence by both businesses and consumers. But a completely frictionless authentication experience can leave consumers doubting the safeness of their transaction. As you respond and adapt to our ever-evolving world, we encourage you to build and strengthen a trusted relationship with your customers through transparency. Consumers know that businesses are collection data about them. When a business is transparent about the use of that data, digital trust and consumer confidence soars. Through a stronger relationship, customers are more willing to accept friction and need fewer signs of security. Learn more about these and other trends, technology and tactics that can help and hinder your authentication efforts in our new E-book, Upcoming fraud trends and how to combat them.

Day 2 at this year’s Vision conference was fueled with new technology and inspiration. The morning session opened with Robert Boxberger, Experian President, Decision Analytics, and also featured two live demos, one on Experian’s solution for the upcoming CECL compliance deadline and the second for mobile credit, including two use cases on instant issuance and lead generation, which has resulted in a 28% conversion rate of hot leads for one of Experian’s marquee clients. Keynote Speaker: Aimée Mullins "Get comfortable with the uncomfortable" was just one of the mantras shared on Tuesday morning by Aimée Mullins, an actor, Olympian, TEDTalk speaker, and one of the youngest honorees to be inducted into the National Women’s Hall of Fame, among many other accomplishments. “It is our uniqueness that’s our greatest asset that we can leverage for our greatest strength,” said Mullins during her keynote centered on achieving the “impossible.” As a bi-lateral amputee (or “double BK” also known as double below-the-knee amputee, as she referenced), Mullins had doctors and experts tell her and her parents what she would not be able to do. Instead, she encouraged Tuesday’s audience to never stop thinking like a child, to use their curiosity to find new ways where you want to go, and to practice curiosity like a sport to keep from getting comfortable, and therefore static. “It made my not knowing what I can do so much more powerful than an expert's presumption of what he thought I could do,” she said. Session Highlights – Day 2 Consumer Trust What engenders trust as consumers? And what does it take to build online trust? With 51% of new account fraud victims personally knowing the perpetrator and 3.4 billion total losses from fraudulent account openings (Javelin Feb 2019), there are five key components to building trust: digital adoption, transparency, fraud management, recognition and authentication. Today’s consumers want to use the digital channel, have both security and ease of access, be recognized, know how their personal information is being used, and engage and trust with biometrics. Artificial Intelligence – Chat Bots and Beyond According to Gartner, “'Conversational AI-first' will supersede ‘cloud-first,’ ‘mobile first’ as the most important high-level imperative for the next 10 years.” As evidenced by Google Duplex’s realistic conversations with humans, including the use of “uh” and “um,” conversational AI is positioned to redefine the next generation of human interface, aimed at achieving better customer satisfaction and elevate the customer relationship. Marketing Analytics The marketing analytics landscape is changing. Today’s marketing problems – including the always limited budget and need to produce greater ROI – require tactical strategies to target the right consumers. Enter Experian’s AscendTM marketing platform. Leveraging this tool, including its neural networks that were demonstrated Monday morning, helps gain new insights into consumer behavior. Fraud in the Digital Wild West A panel discussion featuring representatives from Merchant Risk Council, USAA and Alliance Data compared fighting fraud to herding cats. Challenges discussed included the ongoing struggle to find balance between limiting friction during the authentication process, while also protecting customers, as well as fraudsters’ tendencies to tap into victims’ emotions and curiosity (think phishing schemes). As one of the panelists offered as a piece of advice, “Fraudsters share best practices, so should we.” Visibility for the Invisibles People are more than the sum of their parts. The traditional credit score may show a consumer’s reputation, but layering trended and alternative data sets adds their character. Not only can trended data and alternative credit data – including leveraging education attributes – make invisible consumers visible, they can also reveal that a consumer with a presumably superlative credit score is actually a “credit zombie.” These data sets enable the opportunity to create first chances, drive second chances and re-evaluate risk, while also driving a strong growth strategy. CECL After reviewing the basics of CECL and the upcoming deadlines (ranging from Q1 2020 to Q1 2022), a review of CECL compliance challenges and potential product changes preceded a modeling techniques case study and a list of key impacts to businesses. Those impacts include: product profitability, loss forecasting methodology, data management and processes and capital ratios. Experian’s CECL forecasting solution leverages Experian’s extensive historical data and Ascend Analytical Sandbox. Using a best practice modeling pipeline to improve efficiency and reduce operational risks, the solution combines advanced machine learning, traditional model techniques and modeling experience to improve performance and reduce risk of overfitting. Keynote Speaker: Kobe Bryant Kobe Bryant closed out the day with stories from his highly-decorated 20-year career with the Los Angeles Lakers, some tips on trash talk and lessons in leadership. “I had to figure out how to be undeniable,” Bryant said, on competing for minutes at the start of his career. In addition to his basketball legacy, including wining five NBA championships, being named an NBA MVP, a two-time NBA Finals MVP and winning two Olympic gold medals, Bryant also launched the Kobe and Vanessa Bryant Family Foundation, hosts the Kobe Academy and has formed Kobe Inc. He’s a storyteller, an Oscar winner, and his name has become synonymous with standing for uncompromising excellence. How to be successful? “Make sure you have the right people on the team,” Bryant said. “Passionate. Borderline obsessive.” One of his key takeaways from his basketball career that translates to his leadership on and off the court happened when his pre-game and game time thinking shifted from internal to external. “You have to put yourself 2nd, 3rd, 4th…you have to put the team first,” Bryant said. For more coverage, follow #ExperianVision on Twitter or check the Experian Insights LinkedIn page.

Experian’s 38th annual Vision Conference kicks off on Sunday, May 5 in San Antonio, Texas. The sold-out thought leadership conference, is known for driving discussions on the industry’s hard-hitting topics as well as introducing the latest and greatest in technology, innovation and data science. “For 38 years, Experian’s Vision Conference has connected business leaders to new ideas and solutions through cutting edge data and insights. Our goal is to power opportunities for you to target new markets, grow existing customer bases, improve response rates, reduce fraud and increase profits by using our data, analytics and technology. The intimate setting of the conference allows for unique networking opportunities with the industry’s most sought-after thought leaders,” said Klaudette Christensen, Experian’s Chief Operations Officer. A few spotlight sessions include: Several sessions about machine learning and artificial intelligence, highlighting opportunities related to best practices, underwriting and fraud detection A deep dive into the modern mortgage, leveraging insights on home equity and how to leverage data and analytics to redefine the process as it’s known today Sessions on credit delinquency, collections and the Great Recession Marketing analytics and the latest releases from Experian’s Ascend Platform Sessions on advanced analytics and integrated decisioning as they relate to commercial and consumer insights The event, which runs through Tuesday evening, continues its tradition of featuring several noteworthy keynote speakers. On Monday, Gary D. Cohn, American business leader, philanthropist and former Director of the U.S. National Economic Council, will kick off the event. On Tuesday, Aimée Mullins will take the stage discussing what is “possible” by drawing from her experiences as a record-breaking Olympic athlete, model and actress. The closing keynote will feature five-time NBA Champion and two-time Olympic Gold Medalist, Kobe Bryant. The event will also include a Tech Showcase, featuring hands-on demos for attendees to experience. Stay tuned for additional highlights and insights on our social media platforms throughout the course of the conference. Follow Experian Insights on Twitter and LinkedIn and check out #ExperianVision.

For most businesses, building the best online experience for consumers requires a balance between security and convenience. But the challenge has always been finding a happy medium between the two – offering enough security that won’t get in the way of convenience and vice versa. In the past, it was always believed that one would always come at the expense of the other. But technology and innovation is changing how businesses approach security and is allowing them to give the maximum potential of both. Consumers want security AND convenience Consumers consider security and convenience as the foundation of their online experience. Findings from our 2019 Global Identity and Fraud Report revealed approximately 74 percent of consumers ranked security as the most important part of their online experience, followed by convenience. In other words, they expect businesses to provide them with both. We see this with how consumers are typically using the same security information each time they open a new digital account – out of convenience. But if one account is compromised, the consumer becomes vulnerable to possible fraudulent activity. With today’s technology, businesses can give consumers an easier and more secure way to access their digital accounts. Creating the optimal online experience More security usually meant creating more passwords, answering more security questions, completing CAPTCHA tests, etc. While consumers are willing to work through these friction-inducing methods to complete a transaction or access an account, it’s not always the most convenient process. Advanced data and technology has opened doors for new authentication methods, such as physical and behavioral biometrics, digital tokenization, device intelligence and machine learning, to maximize the potential for businesses to provide the best online experience possible. In fact, consumers have expressed greater confidence in businesses that implement these advanced security methods. Rates of consumer confidence in passwords was only 44 percent, compared to a 74 percent rate of consumer confidence in physical biometrics. Consumers are willing to embrace the latest security technology because it provides the security and convenience they want from businesses. While traditional forms of security were sufficient, advanced authentication methods have proven to be more reliable forms of security that consumers trust and can improve their online experience. The optimal online experience is a balance between security and convenience. Innovative technologies and data are helping businesses protect people’s identities and provide consumers with an improved online experience.

Be warned. I’m a Philadelphia sports fan, and even after 13 months, I still relish in the only Super Bowl victory I’ve ever known as a fan. Having spent more than two decades in fraud prevention, I find that Super Bowl LII is coalescing in my mind with fraud prevention and lessons in defense more and more. Let me explain: It’s fourth-down-and-goal from the one-yard line. With less than a minute on the clock in the first half, the Eagles lead, 15 to 12. The easy option is to kick the field goal, take the three points and come back with a six-point advantage. Instead of sending out the kicking squad, the Eagles offense stays on the field to go for a touchdown. Broadcaster Cris Collingsworth memorably says, “Are they really going to go for this? You have to take the three!” On the other side are the New England Patriots, winners of two of the last three Super Bowls. Love them or hate them, the Patriots under coach Bill Belichick are more likely than any team in league history to prevent the Eagles from scoring at this moment. After the offense sets up, quarterback Nick Foles walks away from his position in the backfield to shout instructions to his offensive line. The Patriots are licking their chops. The play starts, and the ball is snapped — not to Foles as everyone expects, but to running back Corey Clement. Clement takes two steps to his left and tosses the ball the tight end Trey Burton, who’s running in the opposite direction. Meanwhile, Foles pauses as if he’s not part of the play, then trots lazily toward the end zone. Burton lobs a pass over pursuing defenders into Foles’ outstretched hands. This is the “Philly Special” — touchdown! Let me break this down: A third-string rookie running back takes the snap, makes a perfect toss — on the run — to an undrafted tight end. The tight end, who hasn’t thrown a pass in a game since college, then throws a touchdown pass to a backup quarterback who hasn’t caught a ball in any athletic event since he played basketball in high school. A play that has never been run by the Eagles, led by a coach who was criticized as the worst in pro football just a year before, is perfectly executed under the biggest spotlight against the most dominant team in NFL history. So what does this have to do with fraud? There’s currently an outbreak of breach-fueled credential stuffing. In the past couple of months, billions of usernames and passwords stolen in various high-profile data breaches have been compiled and made available to criminals in data sets described as “Collections 1 through 5.” Criminals acquire credentials in large numbers and attack websites by attempting to login with each set — effectively “stuffing” the server with login requests. Based on consumer propensity to reuse login credentials, the criminals succeed and get access to a customer account between 1 in 1,000 and 1 in 50 attempts. Using readily available tools, basic information like IP address and browser version are easy enough to alter/conceal making the attack harder to detect. Credential stuffing is like the Philly Special: Credential stuffing doesn’t require a group of elite all-stars. Like the Eagles’ players with relatively little experience executing their roles in the Philly Special, criminals with some computer skills, some initiative and the guts to try credential stuffing can score. The best-prepared defense isn’t always enough. The Patriots surely did their homework. They set up their defense to stop what they expected the Eagles to do based on extensive research. They knew the threats posed by every Eagle on the field. They knew what the Eagles’ coaches had done in similar circumstances throughout their careers. The defense wasn’t guessing. They were as prepared as they could have been. It’s the second point that worries me when I think of credential stuffing. Consumers reuse online credentials with alarming frequency, so a stolen set of credentials is likely to work across multiple organizations, possibly even yours. On top of that, traditional device recognition like cookies can’t identify and stop today’s sophisticated fraudsters. The best-prepared organizations feel great about their ability to stop the threats they’re aware of. Once they’ve seen a scheme, they make investments, improve their defenses, and position their players to recognize a risk and stop it. Sometimes past expertise won’t stop the play you can’t see coming.

Although half of businesses globally report an increase in fraud management over the past 12 months, many still experience fraud losses and attacks. To help address these challenges, Experian held its first-ever Fintech Fraud & Identity Meetup on February 5 in San Francisco, Calif. The half-day event was aimed at offering insights on the main business drivers of fraud, market trends, challenges and technology advancements that impact identity management and fraud risk strategy operations. “We understand the digital landscape is changing – inevitably, with technology enhancements come increased fraud risk for businesses operating in the online space,” said Jon Bailey, Experian’s Vice President of Fintech. “Our focus today is on fraud and identity, and providing our fintech customers with the tools and insights needed to grow and thrive.” The meetup was attended by number of large fintech companies with services spanning across a broad spectrum of fintech offerings. To kick off the event, Tony Hadley, Experian’s Senior Vice President of Government & Regulatory Affairs, provided an update on the latest regulatory news and trends impacting data and the fintech space. Next followed a fraud and identity expert panel, which engaged seasoned professionals in an in-depth discussion around two main themes 1) fraud trends and risk mitigation; and 2) customer experience, convenience, and trust. Expert panelists included: David Britton, Experian’s Vice President of Industry Solutions; Travis Jarae, One World Identity’s Founder & CEO; George Kurtyka, Joust’s Co-Founder & COO; and Filip Verley, Airbnb’s Product Manager. “The pace of fraud is so fast, by the time companies implement solutions, the shelf-life may already be old,” Britton said. “That is the crux – how to stay ahead. The goal is to future-proof your fraud strategy and capabilities.” At the close of the expert panel, Kathleen Peters, Experian’s Senior Vice President Head of Fraud and Identity, demoed Experian’s CrossCore™ solution – the first smart, open, plug-and-play platform for fraud and identity services. Peters began by stating, “Fraud is constant. Over 60% of businesses report an increase in fraud-related losses over the past year, with the US leading the greatest level of concern. The best way to mitigate risk is to create a layered approach; that’s why Experian invented CrossCore.” With the sophistication of fraudsters, it’s no surprise that many businesses are not confident with the effectiveness of their fraud strategy. Learn more about how you can stay one step ahead of fraudsters and position yourself for success in the ever-changing fraud landscape; download Experian’s 2019 Global Identity and Fraud Report here. For an inside look at Experian’s Fintech Fraud & Identity Meetup, watch our video below.

How can fintech companies ensure they’re one step ahead of fraudsters? Kathleen Peters discusses how fintechs can prepare for success in fraud prevention.

2019 is here — with new technology, new regulations and new opportunities on the docket. What does that mean for the financial services space? Here are the five trends you should keep your eye on and how these affect your credit universe. 1. Credit access is at an all-time high With 121 million Americans categorized as credit-challenged (subprime scores and a thin or nonexistent credit file) and 45 million considered credit-invisible (no credit history), the credit access many consumers take for granted has appeared elusive to others. Until now. The recent launch of Experian BoostTM empowers consumers to improve their credit instantly using payment history from their utility and phone bills, giving them more control over their credit scores and making them more visible to lenders and financial institutions. This means more opportunities for more people. Coupled with alternative credit data, which includes alternative financial services data, rental payments, and full-file public records, lenders and financial institutions can see a whole new universe. In 2019, inclusion is key when it comes to universe expansion goals. Both alternative credit and consumer-permissioned data will continue to be an important part of the conversation. 2. Machine learning for the masses The financial services industry has long been notorious for being founded on arguably antiquated systems and steeped in compliance and regulations. But the industry’s recent speed of disruption, including drastic changes fueled by technology and innovation, may suggest a changing of the guard. Digital transformation is an industry hot topic, but defining what that is — and navigating legacy systems — can be challenging. Successfully integrating innovation is the convergence at the center of the Venn diagram of strategy, technology and operations. The key, according to Deloitte, is getting “a better handle on data to extract the greatest value from technology investments.” How do you get the most value? Risk managers need big data, machine learning and artificial intelligence strategies to deliver market insights and risk evaluation. Between the difficulty of leveraging data sets and significant investment in time and money, it’s impossible for many to justify. To combat this challenge, the availability and access to an analytical sandbox (which contains depersonalized consumer data and comparative industry intel) is crucial to better serve clients and act on opportunities in lenders’ credit universe and beyond. “Making information analysis easily accessible also creates distinct competitive advantages,” said Vijay Mehta, Chief Innovation Officer for Experian’s Consumer Information Services, in a recent article for BAI Banking Strategies. “Identifying shifts in markets, changes in regulations or unexpected demand allows for quick course corrections. Tightening the analytic life cycle permits organizations to reach new markets and quickly respond to competitor moves.” This year is about meaningful metrics for action, not just data visualization. 3. How to fit into the digital-first ecosystem With so many things available on demand, the need for instant gratification continues to skyrocket. It’s no secret that the financial services industry needs to compete for attention across consumers’ multiple screens and hours of screen time. What’s in the queue for 2019? Personalization, digitalization and monetization. Consumers’ top banking priorities include customized solutions, omnichannel experience improvement and enhancing the mobile channel (as in, can we “Amazonize” everything?). Financial services leaders’ priorities include some of the same things, such as enhancing the mobile channel and delivering options to customize consumer solutions (BAI Banking Strategies). From geolocation targeting to microinteractions in the user experience journey to leveraging new strategies and consumer data to send personalized credit offers, there’s no shortage of need for consumer hyper-relevance. 33 percent of consumers who abandon business relationships do so because personalization is lacking, according to Accenture data for The Financial Brand. This expectation spans all channels, emphasizing the need for a seamless experience across all devices. 4. Keeping fraudsters out Many IT professionals regard biometric authentication as the most secure authentication method currently available. We see this technology on our personal devices, and many companies have implemented it as well. Biometric hacking is among the predicted threats for 2019, according to Experian’s Data Breach Industry Forecast, released last month. “Sensors can be manipulated and spoofed or deteriorate with too much use. ... Expect hackers to take advantage of not only the flaws found in biometric authentication hardware and devices, but also the collection and storage of data,” according to the report. 5. Regulatory changes and continued trends Under the Trump Administration, the regulatory front has been relatively quiet. But according to the Wall Street Journal, as Democrats gain control of the House of Representatives, lawmakers may be setting their sights on the financial services industry — specifically on legislation in response to the credit data breach in 2017. The Democratic Party leadership has indicated that the House Financial Services Committee will be focused on protecting consumers and investors, preserving sector stability, and encouraging responsible innovation in financial technology, according to Deloitte. In other news, the focus on improving accuracy in data reporting, transparency for consumers in credit scoring and other automated decisions can be expected to continue. Consumer compliance, and specifically the fair and responsible treatment of consumers, will remain a top priority. For all your needs in 2019 and beyond, Experian has you covered. Learn more

It’s the holiday season — time for jingle bells, lighting candles, shopping sprees and credit card fraud. But we’re prepared. Our risk analyst team constantly monitors our FraudNet solution performance to identify anomalies our clients experience as millions of transactions occur this month. At its core, FraudNet analyzes incoming events to determine the risk level and to allow legitimate events to process without causing frustrating friction for legitimate customers. That ensures our clients can recognize good customers across digital devices and channels while reducing fraud attacks and the need for internal manual reviews. But what happens when things don’t go as planned? Here’s a recent example. One of our banking clients noticed an abnormally high investigation queue after a routine risk engine tuning. Our risk analyst team looked further into the attacks to determine the cause and assess whether it was a tuning issue or a true fraud attack. After an initial analysis, the team learned that the events shared many of the same characteristics: Came from the same geo location that has been seen in previous attacks on clients Showed suspicious device and browser characteristics that were recognized by Experian’s device identification technology Identified suspicious patterns that have been observed in other recent attacks on banks The conclusion was that it wasn’t a mistake. FraudNet had correctly identified these transactions as suspicious. Experian® then worked with our client and recommended a strategy to ensure this attack was appropriately managed. This example highlights the power of device identification technology as a mechanism to detect emerging fraud threats, as well as link analysis tools and the expertise of a highly trained fraud analyst to uncover suspicious events that might otherwise go unnoticed. In addition to proprietary device intelligence capabilities, our clients take advantage of a suite of capabilities that can further enhance a seamless authentication experience for legitimate customers while increasing fraud detection for bad actors. Using advanced analytics, we can detect patterns and anomalies that may indicate a fraudulent identity is being used. Additionally, through our CrossCore® platform businesses can leverage advanced innovation, such as physical and behavioral biometrics (facial recognition, how a person holds a phone, mouse movements, data entry style), email verification (email tenure, reported fraud on email identities), document verification (autofill, liveliness detection) and digital behavior risk indicators (transaction behavior, transaction velocity), to further advance their existing risk mitigation strategies and efficacy. With expanding partnerships and capabilities offered via Experian’s CrossCore platform, in conjunction with consultative industry expertise, businesses can be more confident during the authentication process to ensure a superb, frictionless customer experience without compromising security.