At A Glance
It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.Paragraph Block- is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
New Text!


Heading 2
Heading 3
Heading 4
Heading 5
- This is a list
- Item 1
- Item 2
- Sub list
- Sub list 2
- Sub list 3
- More list
- More list 2
- More list 3
- More more
- More more
This is the pull quote block Lorem Ipsumis simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s,
ExperianThis is the citation

This is the pull quote block Lorem Ipsumis simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s,
ExperianThis is the citation
| Table element | Table element | Table element |
| my table | my table | my table |
| Table element | Table element | Table element |

Media Text Block
of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum
My Small H5 Title

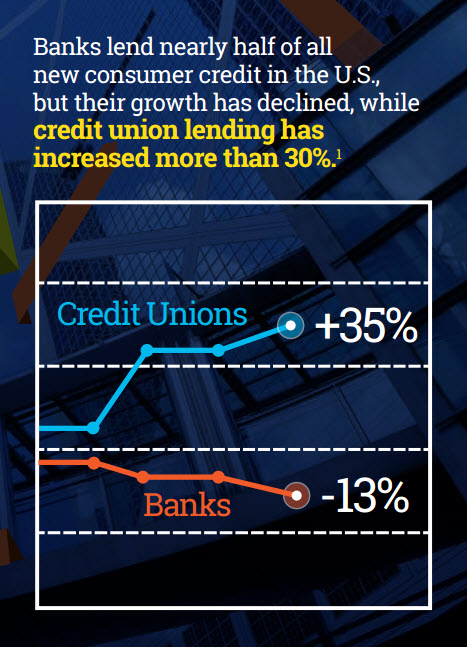
Are you sure you are making the best consumer credit decisions? Given the constantly evolving market conditions, it is a challenge to keep informed. In order to confidently grow and manage the bottom line, organizations need to avoid these four basic risks of making credit decisions with limited trend visibility. Competitive Risk – With limited visibility to industry trends, organizations cannot understand their position relative to peers. Product Risk – Organizations without access to the latest consumer behaviors cannot identify and capitalize on emerging trends. Market Risk – Decisions suffer when made without considering market trends in the context of the economy. Resource Risk – Extracting useful insights from vast market data requires abundant resources and comprehensive expertise. Get more information on the business risks of navigating credit decisions with limited trend visibility.

A recent study conducted by the Ponemon Institute found that a data breach is among the top three occurrences that affect brand reputation, along with poor customer service and an environmental incident.

Universe expansion is key to any lender’s growth strategy. Sophisticated, advanced risk models, such as the VantageScore®3.0 model, allow lenders to score up to 35 million more consumers than other risk models.
In this article…
typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.


