At A Glance
It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.Paragraph Block- is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
New Text!


Heading 2
Heading 3
Heading 4
Heading 5
- This is a list
- Item 1
- Item 2
- Sub list
- Sub list 2
- Sub list 3
- More list
- More list 2
- More list 3
- More more
- More more
This is the pull quote block Lorem Ipsumis simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s,
ExperianThis is the citation

This is the pull quote block Lorem Ipsumis simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s,
ExperianThis is the citation
| Table element | Table element | Table element |
| my table | my table | my table |
| Table element | Table element | Table element |

Media Text Block
of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum
My Small H5 Title

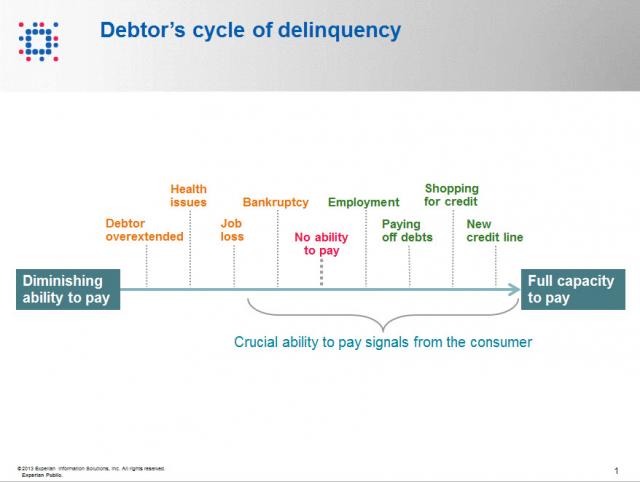
Contact information such as phone numbers and addresses are fundamental to being able to reach a debtor, but knowing when to reach out to the debtor is also a crucial factor impacting success or failure in getting payment. As referenced in the chart below, when a consumer enters the debtor life cycle, they often avoid talking with you about the debt because they do not have the ability to pay. When the debtor begins to recover financially, you want to be sure you are among the first to reach out to them so you can be the first to be paid. According to Don Taylor, President of Automated Collection Services, they have seen a lift of more than 12% of consumers with trigger hits entering repayment, and this on an aged portfolio that has already been actively worked by debt collection staff. Monitoring for a few key changes on the credit profiles of debtors provides the passive monitoring that is needed to tell you the optimal time to reach back to the consumer for payment. Experian compiled several recent collection studies and found that a debtor paying off an account that was previously past due provided a 710% increase in the average payment. Positive improvement on a consumers’ credit profile is one of those vital indicators that the consumer is beginning to recover financially and could have the will—and ability—to pay bad debts. The collection industry is not like the big warehouse stores—quantity and value do not always work hand in hand for the debt collection industry. Targeting the high value credit events that are proven to increase collection amounts is the key to value, and Experian has the expertise, analytics and data to help you collect in the most effective manner. Be sure to check out our other debt collection blog posts to learn how to recover debt more quickly and efficiently.

By: Joel Pruis What is it we as bankers are trying to accomplish? If you have been in the industry for 20+ years, this question may sound ridiculous! We do what we do! We are bankers! What do you mean define what are we trying to do? But that is the question, what is it we are trying to do? I am going to propose we boil it down to the basic/fundamental element – Banks aggregate money from various sources and redeploy these funds to earn a return for the shareholders. Ultimately, our objective is to generate an appropriate return for the shareholders Getting back to the movie Moneyball, Billy Beane and Peter Brand define the objective of the Oakland A’s for the season in terms of projecting the number of wins that are needed to assure, with all probability, that the team makes the playoffs (this would be similar to the objective of banking to generate an appropriate return for the shareholders). But Peter Brand quickly moves into very specific targets that are required for the A’s to make it to the playoffs, namely win 99 regular season games. In order to win 99 regular season games, the A’s offense will need to score 814 runs in the season and defensively only allow 645 runs. Plain and simple. Very objective, very measurable and it is all based upon data, data, data. Let’s break this down. Based upon their conference, the teams in their conference along with the overall schedule, Peter Brand projects that 99 wins are necessary to land a spot in the playoffs. No gut check, no darts or crystal ball but rather historical data that when analyzed provides the benchmark of 99 wins to statistically assure the Oakland A’s that they will make the playoffs. So let’s apply this to banking. Our objective is to generate the appropriate return for our shareholders or the old Return on Equity. So, for example, if our targeted return on equity is 20% (making the playoffs) we need to make sure we generate enough net income (99 wins) through producing the necessary gross yield on assets (814 runs generated by the Oakland A’s offense) less the expected charge offs (645 runs allowed by the Oakland A’s defense). For a quick dive into details, our data would provide for a margin of error on the variable to provide for statistical assurance of achieving the objective (Return on Equity). In the movie there is no guaranty that the 814 runs will win the conference but at the same time there is no guaranty that the Oakland A’s opponents will score 645 runs. Never in the movie does the coach, Billy Beane or Peter Brand tell the team, “You only have to score X number of runs this game, don’t score anymore.” Or even crazier, “You are not letting the other team score enough runs, they need to score 645!” No, the strategy is still to generate as many runs as possible while minimizing the number of runs scored by the opposition. Rather it is the review of the total amount of earning assets of the financial institution and the overall credit quality that we must understand and control to determine our ability to generate the net yield on assets required to generate the return on equity that is required. If we assume too much risk in the portfolio in order to generate the required yield it would be similar to having a poor pitching staff projected to allow 10 runs a game requiring the team to produce 11 runs a game in order to win. It just is not realistic. So basically we need to assess at the high level, are we appropriately structured to allow for the generation of enough profit to provide the appropriate return on equity. At this point, we do not need to complicate it any further than that. Now let’s take a look at the constraints. We know we have them in banking, let’s take a look at probably the single biggest constraint imposed on Billy Beane and the Oakland A’s. In the movie, before Billy Beane is even aware of the Moneyball concept, his is given his constraint by the owner. Beane asks for more money to ‘buy players’ and is flat out rejected by the owner. The owner, in fact, cuts Beane off by asking, “is there anything else I can do for you?”. Net result is that the Oakland A’s have $38 million dollars for payroll vs. the New York Yankees at $120 million. Seriously it does not seem fair. How can you attract the needed talent when you cannot pay the type of salary needed to get the necessary players to win a championship? Let’s rephrases this for banking… How can a bank be expected to deploy its assets when such a high rate of return is required? Boiling it down to a specific example, “How can I originate a commercial loan at this rate of interest when the competition is ½ to 1% lower than our rates?” Up next – Why will 99 games get us to the playoffs? How do we assess the environment?

A recent study comparing financial differences between men and women found that, overall, women are better at managing money and debt. Differences between the two populations include:
In this article…
typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.


