As we prepare to attend next week’s FS-ISAC & BITS Summitwe know that the financial services industry is abuzz about massive losses from the ever-evolving attack vectors including DDoS, Malware, Data Breaches, Synthetic Identities, etc. Specifically, the recent $200 million (and counting) in losses tied to a sophisticated card fraud scheme involving thousands of fraudulent applications submitted over several years using synthetic identities. While the massive scale and effectiveness of the attack seems to suggest a novel approach or gap in existing fraud prevention controls, the fact of the matter is that many of the perpetrators could have been detected at account opening, long before they had an opportunity to cause financial losses. Synthetic identities have been a headache for financial institutions for years, but only recently have criminal rings begun to exploit this attack vector at such a large scale.
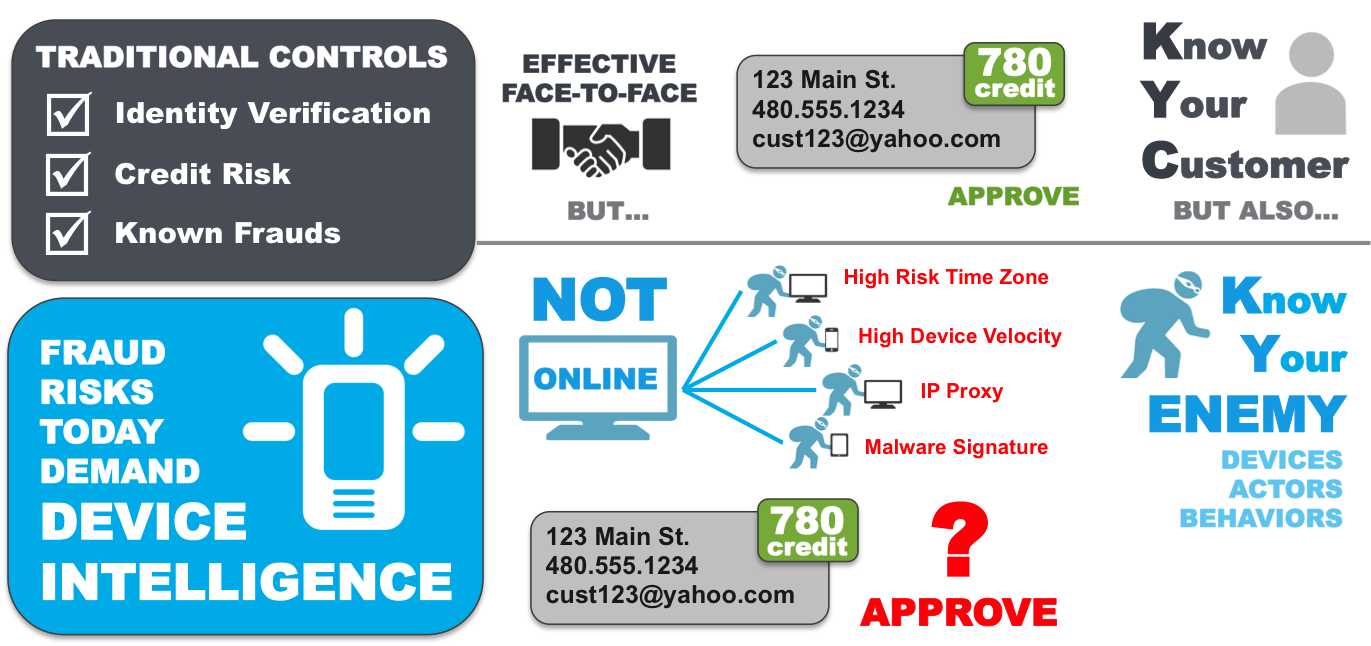
The greatest challenge with synthetic identities is that traditional account opening processes focus on identity verification compliance around the USA PATRIOT Act and FACT Act Red Flags guidance, risk management using credit bureau scores, and fraud detection using known fraudulent data points. A synthetic identity ring simply sidesteps those controls by using new false identities created with data that could be legitimate, have no established credit history, or slightly manipulate elements of data from individuals with excellent credit scores. The goal is to avoid detection by “blending in” with the thousands of credit card, bank account, and loan applications submitted each day where individuals do not have a credit history, where minor typos cause identity verification false positives, or where addresses and other personal data does not align with credit reports. Small business accounts are an even easier target, as third-party data sources to verify their authenticity are sparse even though the financial stakes are higher with large lines of credit, multiple signors, and complex (sometimes international) transactions. Detecting these tactics is nearly impossible in a channel where anonymity is king — and many rings have become experts on gaming the system, especially as institutions continue to migrate the bulk of their originations to the online channel and the account opening process becomes increasingly faceless.
While the solutions described above play a critical role in meeting compliance and risk management objectives, they unfortunately often fall short when it comes to detecting synthetic identities. Identity verification vendors were quick to point the finger at lapses in financial institutions’ internal and third-party behavioral and transactional monitoring solutions when the recent $200 million attack hit the headlines, but these same providers’ failure to deploy device intelligence alongside traditional controls likely led to the fraudulent accounts being opened in the first place.
With synthetic identities, elements of legitimate creditworthy consumers are often paired with other invalid or fictitious applicant dataso fraud investigators cannot rely on simply verifying data against a credit report or public data source. In many cases, the device used to submit an application may be the only common element used to link and identify other seemingly unrelated applications. Several financial institutions have already demonstrated success at leveraging device intelligence along with a powerful risk engine and integrated link analysis tools to pinpoint these complex attacks. In fact, one example alone spanned hundreds of applications and represented millions of dollars in fraud saves at a top bank.
The recent synthetic ring comprising over 7,000 false identities and 25,000 fraudulent cards may be an extreme example of the potential scope of this problem; however, the attack vector will only continue to grow until device intelligence becomes an integrated component of all online account opening decisions across the industry. Even though most institutions are satisfying Red Flags guidance, organizations failing to institute advancedaccount opening controls such as complex device intelligence can expect to see more attacks and will likely struggle with higher monetary losses from accounts that never should have been booked.