
In this article…
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Phasellus at nisl nunc. Sed et nunc a erat vestibulum faucibus. Sed fermentum placerat mi aliquet vulputate. In hac habitasse platea dictumst. Maecenas ante dolor, venenatis vitae neque pulvinar, gravida gravida quam. Phasellus tempor rhoncus ante, ac viverra justo scelerisque at. Sed sollicitudin elit vitae est lobortis luctus. Mauris vel ex at metus cursus vestibulum lobortis cursus quam. Donec egestas cursus ex quis molestie. Mauris vel porttitor sapien. Curabitur tempor velit nulla, in tempor enim lacinia vitae. Sed cursus nunc nec auctor aliquam. Morbi fermentum, nisl nec pulvinar dapibus, lectus justo commodo lectus, eu interdum dolor metus et risus. Vivamus bibendum dolor tellus, ut efficitur nibh porttitor nec.
Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Maecenas facilisis pellentesque urna, et porta risus ornare id. Morbi augue sem, finibus quis turpis vitae, lobortis malesuada erat. Nullam vehicula rutrum urna et rutrum. Mauris convallis ac quam eget ornare. Nunc pellentesque risus dapibus nibh auctor tempor. Nulla neque tortor, feugiat in aliquet eget, tempus eget justo. Praesent vehicula aliquet tellus, ac bibendum tortor ullamcorper sit amet. Pellentesque tempus lacus eget aliquet euismod. Nam quis sapien metus. Nam eu interdum orci. Sed consequat, lectus quis interdum placerat, purus leo venenatis mi, ut ullamcorper dui lorem sit amet nunc. Donec semper suscipit quam eu blandit. Sed quis maximus metus. Nullam efficitur efficitur viverra. Curabitur egestas eu arcu in cursus.
H1
H2
H3
H4
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Vestibulum dapibus ullamcorper ex, sed congue massa. Duis at fringilla nisi. Aenean eu nibh vitae quam auctor ultrices. Donec consequat mattis viverra. Morbi sed egestas ante. Vivamus ornare nulla sapien. Integer mollis semper egestas. Cras vehicula erat eu ligula commodo vestibulum. Fusce at pulvinar urna, ut iaculis eros. Pellentesque volutpat leo non dui aliquet, sagittis auctor tellus accumsan. Curabitur nibh mauris, placerat sed pulvinar in, ullamcorper non nunc. Praesent id imperdiet lorem.
H5
Curabitur id purus est. Fusce porttitor tortor ut ante volutpat egestas. Quisque imperdiet lobortis justo, ac vulputate eros imperdiet ut. Phasellus erat urna, pulvinar id turpis sit amet, aliquet dictum metus. Fusce et dapibus ipsum, at lacinia purus. Vestibulum euismod lectus quis ex porta, eget elementum elit fermentum. Sed semper convallis urna, at ultrices nibh euismod eu. Cras ultrices sem quis arcu fermentum viverra. Nullam hendrerit venenatis orci, id dictum leo elementum et. Sed mattis facilisis lectus ac laoreet. Nam a turpis mattis, egestas augue eu, faucibus ex. Integer pulvinar ut risus id auctor. Sed in mauris convallis, interdum mi non, sodales lorem. Praesent dignissim libero ligula, eu mattis nibh convallis a. Nunc pulvinar venenatis leo, ac rhoncus eros euismod sed. Quisque vulputate faucibus elit, vitae varius arcu congue et.
Ut convallis cursus dictum. In hac habitasse platea dictumst. Ut eleifend eget erat vitae tempor. Nam tempus pulvinar dui, ac auctor augue pharetra nec. Sed magna augue, interdum a gravida ac, lacinia quis erat. Pellentesque fermentum in enim at tempor. Proin suscipit, odio ut lobortis semper, est dolor maximus elit, ac fringilla lorem ex eu mauris.
- Phasellus vitae elit et dui fermentum ornare. Vestibulum non odio nec nulla accumsan feugiat nec eu nibh. Cras tincidunt sem sed lacinia mollis. Vivamus augue justo, placerat vel euismod vitae, feugiat at sapien. Maecenas sed blandit dolor. Maecenas vel mauris arcu. Morbi id ligula congue, feugiat nisl nec, vulputate purus. Nunc nec aliquet tortor. Maecenas interdum lectus a hendrerit tristique. Ut sit amet feugiat velit.
- Test
- Yes

As part of its guidance, the Office of the Comptroller of the Currency recommends that lenders perform regular validations of their credit score models in order to assess model performance.
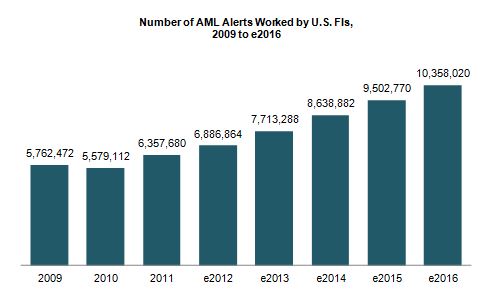
Julie Conroy – Research Director, Aite Group Finding patterns indicative of money laundering and other financial crimes is akin to searching for a needle in a haystack. With the increasing pressure on banks’ anti-money laundering (AML) and fraud teams, many with this responsibility increasingly feel like they’re searching for those needles while a combine is bearing down on them at full speed. These pressures include: Regulatory scrutiny: The high-profile—and expensive—U.S. enforcement actions that took place during the last couple of years underscore the extent to which regulators are scrutinizing FIs and penalizing those who don’t pass muster. Payment volumes and types increasing: As the U.S. economy is gradually easing its way into a recovery, payment volumes are increasing. Not only are volumes rebounding to pre-recession levels, but there have also been a number of new financial products and payment formats introduced over the last few years, which further increases the workload for the teams who have to screen these payments for money-laundering, sanctions, and global anti-corruption-related exceptions. Constrained budgets: All of this is taking place during a time in which top line revenue growth is constrained and financial institutions are under pressure to reduce expenses and optimize efficiency. Illicit activity on the rise: Criminal activity continues to increase at a rapid pace. The array of activity that financial institutions’ AML units are responsible for detecting has also experienced a significant increase in scope over the last decade, when the USA PATRIOT Act expanded the mandate from pure money laundering to also encompass terrorist financing. financial institutions have had to transition from activity primarily focused on account-level monitoring to item-level monitoring, increasing by orders of magnitude the volumes of alerts they must work (Figure 1) Figure 1: U.S. FIs Are Swimming in Alerts Source: Aite Group interviews with eight of the top 30 FIs by asset size, March to April 2013 There are technologies in market that can help. AML vendors continue to refine their analytic and matching capabilities in an effort to help financial insitutions reduce false positives while not adversely affecting detection rates. Hosted solutions are increasingly available, reducing total cost of ownership and making software upgrades easier. And many institutions are working on internal efficiency efforts, reducing vendors, streamlining processes, and eliminating the number of redundant efforts. How are institutions handling the increasing pressure cooker that is AML compliance? Aite Group wants to know your thoughts. We are conducting a survey of financial insitution executives to understand your pain points and proposed solutions. Please take 20 minutes to share your thoughts, and in return, we’ll share a complimentary copy of the resulting report. This data can be used to compare your efforts to those of your peers as well as to glean new ideas and best practices. All responses will be kept confidential and no institutions names will be mentioned anywhere in the report. You can access the survey here: SURVEY

A breach notification letter is important for firms to let consumers know that their information may have been compromised.


