At A Glance
aag optionalthis is heading!

kjdaskldj
some company name herekdljsaldkjlska
Docker is an open-source project to easily create lightweight, portable, self-sufficient containers from any application. The same container that a developer builds and tests on a laptop can run at scale, in production, on VMs, bare metal, OpenStack clusters, public clouds and more.
Docker is an open-source project to easily create lightweight, portable, self-sufficient containers from any application. The same container that a developer builds and tests on a laptop can run at scale, in production, on VMs, bare metal, OpenStack clusters, public clouds and more.


thisis a contet t for medai text block!
Paragraph Block- is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.


Heading 2
Heading 3
Heading 4
Heading 5
- This is a list
- Item 1
- Item 2
- Sub list
- Sub list 2
- Sub list 3
- More list
- More list 2
- More list 3
- More more
- More more
This is the pull quote block Lorem Ipsumis simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s,
ExperianThis is the citation

This is the pull quote block Lorem Ipsumis simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s,
ExperianThis is the citation
| Table element | Table element | Table element |
| my table | my table | my table |
| Table element | Table element | Table element |

Media Text Block
of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum
My Small H5 Title


 When a criminal steals your account number and security code, they often are planning to use that account to make purchases. Your credit report is not consulted for purchase transactions.
So, in such cases, you should consider contacting your card issuer and request a new account number. At minimum, you should check your account online to see if there has been any activity which you do not recognize.
If the criminal’s goal is to open new accounts in your name, then it is likely that one of your three credit reports would be accessed by the potential lender. In that case, you may want to consider adding an alert to your reports.
Fraud alerts are special statements consumers can have added to their credit report if they have reason to believe they may be a fraud victim or know that they have been victimized.
When a criminal steals your account number and security code, they often are planning to use that account to make purchases. Your credit report is not consulted for purchase transactions.
So, in such cases, you should consider contacting your card issuer and request a new account number. At minimum, you should check your account online to see if there has been any activity which you do not recognize.
If the criminal’s goal is to open new accounts in your name, then it is likely that one of your three credit reports would be accessed by the potential lender. In that case, you may want to consider adding an alert to your reports.
Fraud alerts are special statements consumers can have added to their credit report if they have reason to believe they may be a fraud victim or know that they have been victimized.

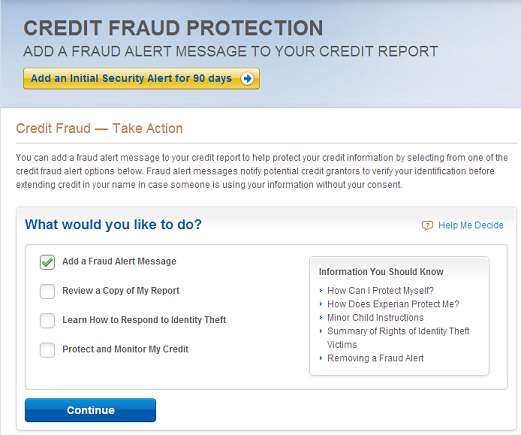 News of the Target stores security breach has caused many people to ask what they can do to protect themselves from misuse of their stolen identification information.
The system of fraud alerts that has been in place for decades in the credit reporting systems was designed specifically to help people who are identity theft victims, or have reason to believe they may be, to stop credit fraud resulting from that identity theft.
In the Target incident and similar data breaches, neither a temporary security alert nor a fraud victim statement on your credit report will stop the thief from using your credit card account.
But the alerts may help protect affected consumers from new credit fraud if the identity thief attempts to open new credit accounts using their stolen information.
These services are available at no charge to anyone who is a victim of identity theft, or who has reason to believe they may be a victim:
News of the Target stores security breach has caused many people to ask what they can do to protect themselves from misuse of their stolen identification information.
The system of fraud alerts that has been in place for decades in the credit reporting systems was designed specifically to help people who are identity theft victims, or have reason to believe they may be, to stop credit fraud resulting from that identity theft.
In the Target incident and similar data breaches, neither a temporary security alert nor a fraud victim statement on your credit report will stop the thief from using your credit card account.
But the alerts may help protect affected consumers from new credit fraud if the identity thief attempts to open new credit accounts using their stolen information.
These services are available at no charge to anyone who is a victim of identity theft, or who has reason to believe they may be a victim:

 As Senior Vice President of Government Affairs and Public Policy at Experian, I had the opportunity to testify today before the Senate Committee on Commerce, Science and Transportation. As always, we continue to welcome the Committee’s interest in the marketing data industry.
In the spirit of cooperation, our goal is to help the Committee understand the role our data services play in the economy and in the lives of consumers.
Specifically, here are some key points we have shared to help inform the Committee’s work and interest in better understanding the marketplace:
Experian believes responsible information sharing enhances economic productivity in the United States and provides many benefits to consumers. Economists have stated the manner in which US companies collect and share consumer information among affiliated entities and third parties is the key ingredient to our nation’s productivity, innovation and ability to compete in the global marketplace.
As Senior Vice President of Government Affairs and Public Policy at Experian, I had the opportunity to testify today before the Senate Committee on Commerce, Science and Transportation. As always, we continue to welcome the Committee’s interest in the marketing data industry.
In the spirit of cooperation, our goal is to help the Committee understand the role our data services play in the economy and in the lives of consumers.
Specifically, here are some key points we have shared to help inform the Committee’s work and interest in better understanding the marketplace:
Experian believes responsible information sharing enhances economic productivity in the United States and provides many benefits to consumers. Economists have stated the manner in which US companies collect and share consumer information among affiliated entities and third parties is the key ingredient to our nation’s productivity, innovation and ability to compete in the global marketplace.
In this article…
typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.

