Ecommerce / Retail

In this new Telephone Consumer Protection Act (TCPA) era, calling your customers isn’t a thing of the past. It’s still okay to reach out to your clients by phone, whether to offer a new product or collect on an overdue bill. But strict compliance with TCPA rules is critical for any business that contacts customers by phone. Some of the very best ways you can protect yourself from TCPA exposure is to follow four steps when creating your dialing strategy: Customer consent: It’s important to maintain and update your customers’ contact preferences and consent to call them. Simply having a phone number on an application isn’t sufficient. Companies are required to have written permission, such as “I consent to calling my cell phone when there’s a problem …” Remember, permission may only be granted by the party who subscribes to the cellular service or who regularly uses that cell phone number. Landline or wireless?: Your database should also include the phone type for the telephone numbers you have for your customers. The dialing rules differ depending on the phone type, so it’s critical to know the type of phone you are calling or texting. Verify ownership: Ownership of cell phones should especially be validated to ensure the number hasn’t been reassigned and that the person who gave consent still owns the phone. One call can be made to a reassigned number with no liability, assuming you have no knowledge the number has changed. Repeating the action could lead to fines from $500 to $1,500 per infraction. Scrub Your Database: Have practices in place to remove any confirmed reassigned phone numbers from your database. This will help to improve your right-party contact rate and save you from potential TCPA headaches. No one disagrees that calling cell numbers is a risky business, but it can be done if you set the proper workflow in motion. Click here to learn more about Experian solutions that will help to reduce your TCPA compliance risk.
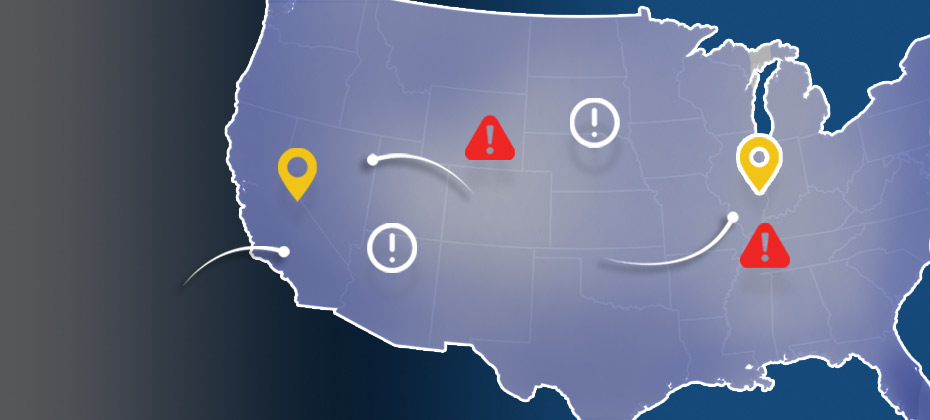
Experian analyzed millions of e-commerce transactions from the first six months of 2016 to identify the latest fraud attack rates across the United States for both shipping and billing locations. As we approach the one-year anniversary of the EMV liability shift, the 2016 e-commerce fraud attack rates look to be at least 15 percent higher than last year’s total. Experian analyzed millions of e-commerce transactions from the first six months of 2016 to identify the latest fraud attack rates across the United States for both shipping and billing locations. Billing fraud rates are associated with the address of the purchaser. Shipping fraud rates are associated with the address where purchased goods are sent. As we approach the one-year anniversary of the EMV liability shift, the 2016 e-commerce fraud attack rates look to be at least 15 percent higher than last year’s total. E-commerce fraud is often an indicator that other fraud activities have already happened, whether a credit card has been stolen, identity fraud has occurred, or personal credentials have been compromised.

In this age of content and increasing financial education available to all, most entities are familiar with credit bureaus, including Experian. They are known for housing enormous amounts of data, delivering credit scores and helping businesses decision on credit. On the consumer side, there are certainly myths about credit scores and the credit report. But myths exist among businesses as well, especially as it pertains to the topic of reporting credit data. How does it work? Who’s responsible? Does reporting matter if you’re a small lender? Let’s tackle three of the most common myths surrounding credit reporting and shine a light on how it really is essential in creating a healthy credit ecosystem. Myth No. 1: Reporting to one bureau is good enough. Well, reporting to one bureau is definitely better than reporting to none, but without reporting to all three bureaus, there could be gaps in a consumer’s profile. Why? When a lender pulls a consumer’s profile to evaluate it for extending additional credit, they ideally would like to see a borrower’s complete credit history. So, if one of their existing trades is not being reported to one bureau, and the lender makes a credit pull from a different bureau to use for evaluation purposes, no knowledge of that trade exists. In cases like these, credit grantors may offer credit to your customer, not knowing the customer already has an obligation to you. This may result in your customer getting over-extended and negatively impacting their ability to pay you. On the other side, in the cases of a thin-file consumer, not having that comprehensive snapshot of all trades could mean they continue to look “thin” to other lenders. The best thing you can do for a consumer is report to all three bureaus, making their profile as robust as it can be, so lenders have the insights they need to make informed credit offers and decisions. Some believe the bureaus are regional, meaning each covers a certain part of the country, but this is false. Each of the bureaus are national and lenders can report to any and all. Myth No. 2: Reporting credit data is hard. Yes, accurate and timely data reporting requires a few steps, but after you get familiar with Metro 2, the industry standard format for consumer data reporting, choose a strategy, and register for e-Oscar, the process is set. The key is to do some testing, and also ensure the data you pass is accurate. Myth No. 3: Reporting credit data is a responsibility for the big institutions –not smaller lenders and companies. For all lenders, credit bureau data is vitally important in making informed risk determinations for consumer and small business loans. Large financial institutions have been contributing to the ecosystem forever. Many smaller regional banks and credit unions have reported consistently as well. But just think how much stronger the consumer credit profile would be if all lenders, utility companies and telecom businesses reported? Then you would get a true, complete view into the credit universe, and consumers benefit by having the most comprehensive profile --- Bottom line is that when comprehensive data on consumer credit histories is readily available, it’s a good thing for consumers and lenders. And the truth is all businesses - big and small - can make this a reality.
Experian conducted a joint-survey that uncovered insights into the topic of conversational commerce and voice assistants. The survey audience constituted nearly 1300 smartphone users of smart voice assistant tools. The survey asked about most requested tasks and general consumer satisfaction with the voice-recognition capabilities of Amazon's Alexa relative to other smart voice assistants such as Siri and Google.

Experian estimates card-to-card consumer balance transfer activity to be between $35 and $40 billion a year, representing a sizeable opportunity for proactive lenders seeking to grow their revolving product line. This opportunity, however, is a threat for reactive lenders that only measure portfolio attrition instead of working to retain current customers. While billions of dollars are transferred every year, this activity represents only a small percentage of the total card population. And given the expense of direct marketing, lenders seeking to capitalize on and protect their portfolio from balance transfer activity must leverage data insights to make more informed decisions. Predicting a consumer’s future propensity to engage in card-to-card balance transfers starts with trended data. A credit score is a snapshot in time, but doesn’t reveal deep insights about a consumer’s past balance transfer activity. Lenders that rely only on current utilization will group large populations of balance revolvers into one bucket – and many of these individuals will have no intention of transferring to another product in the near future. Still, balance transfer activity can be identified and predicted by utilizing trended data. By analyzing the spend and payment data over time to see when one (or multiple) trade’s payment approximately matches another trade’s spend, we have the logic that suggests there has been a card-to-card transfer. What most people don’t realize is that trended data is difficult to work with. With 24 months of history on five fields, a single trade includes 120 data points. That’s 720 data points for a consumer with six trades on file and 72,000,000 for a file with 100,000 records, not to mention the other data fields in the file. It’s easy to see why even the most sophisticated organizations become paralyzed working with trended data. While teams of analysts get buried in the data, projects drag, costs swell, and eventually the world changes as rates climb and fall. By the time the analysis is complete, it must be recalibrated. But there is a solution. Experian has developed powerful predictions tools that combine past balance transfer history, historical transfer amounts, current trades carried and utilized, payments, and spend. Combined, these data fields can help identify consumers who are most likely to transfer a balance in the future. With Experian’s Balance Transfer Index the highest scoring 10 percent of consumers capture nearly 70 percent of total balance transfer dollars. Imagine the impact on ROI of reducing 90 percent of the marketing cost of your next balance transfer campaign and still reaching 70 percent of the balance transfer activity. Balance transfer activity represents a meaningful dollar opportunity for growth, but is concentrated in a small percentage of the population making predictive analytics key to success. Trended data is essential for identifying those opportunities, but financial institutions must assess their capabilities when it comes to managing the massive data attached. The good news is that regardless of financial institution size, solutions now exist to capture the analytics and provide meaningful and actionable insights to lenders of all sizes.

New industry report highlights the convergence of business growth and fraud prevention strategies Experian has published its first annual global fraud report covering the convergence of growth strategies and fraud prevention. The report, Global Business Trends: Protecting Growth Ambitions Against Rising Fraud Threats, is designed as a guide for senior executives and fraud prevention professionals, offering new insights on how the alignment of strategies for business growth and fraud prevention can help a business grow revenues while managing risks in an increasingly virtual world. The report identifies five trends that businesses should assess and take action on to mitigate fraud and improve the customer experience in today's fast-paced, consumer-centric environment: Applying right-sized fraud solutions to reduce unnecessary customer disruption: It's time to move on from a one-size-fits-all approach that creates more customer friction than necessary. Instead, companies should apply fraud solutions that reflect the value and level of confidence needed for each transaction. This means right-sizing your fraud solutions to align with true fraud rates and commercial strategy. Having a universal view of the consumer is the core of modern fraud mitigation and marketing: Achieving a universal profile of consumer behavior — beyond the traditional 360-degree view — requires access to a combination of identity data, device intelligence, online behavior, biometrics, historical transactions and more, for consumer interactions not only with you, but across other businesses and industries as well. Companies that translate this knowledge and use it to identify consumers can distinguish a fraudster from a real customer more easily, building trust along the way. Expanding your view through a blended ecosystem: In addition to using your own first-party data sources, companies need to participate in a blended ecosystem, working across businesses and even industries. Fraudsters have access to more data than ever before, including data traditionally used to verify identities, and they use that data to create an entire digital profile. Therefore, you can no longer get to the digital interaction data you need by managing the process in a siloed manner. Achieving an expansive view of the universal consumer requires multiple data sources working together. Achieving agility and scale using service-based models: Today, more and more companies are choosing subscription-based systems rather than building in-house or implementing on-premise solutions. Continuous upgrades and the access to new risk logic that come with subscription models provide more agility and faster response to emerging threats, no matter how fast your volume grows or what products, channels or geographies you pursue. Future-proofing fraud solution choices: Companies need access to a wide variety of traditional and emerging technologies and information sources to fill in knowledge gaps and blind spots where fraudsters try to hide. The ability to modify strategies quickly and catch fraud faster while improving the customer experience is a critical aspect of fraud prevention moving forward. Bringing together these key trends, the report provides business leaders with the insight they need to fight fraud using the same consumer-focused approach currently being used to attract new customers and grow revenue. "There is a persistent mindset that fraud loss is just the cost of doing business," said Steve Platt, global EVP, Fraud and Identity, Experian. "But as fraudsters evolve, those losses are climbing, and the status quo is no longer effective or acceptable. We all need to be as forward-looking in fighting fraud as we are in business operations and marketing, and a real understanding of consumers is critical for success. We're talking about the convergence of business growth and fraud prevention, and we're pleased to provide the first report in the marketplace covering this topic." Download the full report here. The report also features an interactive Fraud Prevention Benchmark tool that companies can use to explore how these trends impact their business and how the performance of their approach measures up against industry practices. The report is relevant to functions spanning the enterprise, including C-suite executives such as chief marketing officers (CMOs), chief risk officers (CROs) and chief data officers (CDOs). The report focuses on business processes where fraud infiltrates, including new account opening, account access, money movement transactions, and emerging trends combating fraud, such as advanced fraud analytics. In each area, the report details how multiple business functions can apply responses to create business growth. Steve Platt added: "We hear from our clients that they are most successful when CMOs along with CDOs and CROs all work together to understand the customer and develop fraud management solutions that create a better overall experience." Experian was recently cited in Forrester's 2016 Vendor Landscape: Mobile Fraud Management Solutions1 report and listed as having nine out of a possible 10 capabilities needed to combat mobile fraud. Experian was also identified as one of three leading players in the fraud detection and prevention space in a new study from Juniper Research.2 Experian applied best practices to create a global report on providing fraud management solutions that allow companies to maximize profitability while providing secure, hassle-free customer interactions. Learn more about Experian’s Fraud and Identity business. 1Vendor Landscape: Mobile Fraud Management Solutions, Forrester Research, Inc., June 2016. 2Online Payment Fraud: Key Vertical Strategies & Management 2016–2020, Juniper Research, June 2016.

All customers are not created equally – at least when it comes to one’s ability to pay. Incomes differ, financial circumstances vary and economic challenges surface. Lost job. Totaled car. Unplanned medical bills. Life happens. Research conducted by a recent Bankrate study revealed just 38 percent of Americans said they could cover an unexpected emergency room visit or a $500 car repair with available cash in a checking or savings account. It’s a scary situation for individuals, and also a source of stress for the lender expecting payment. So what are the natural moments for a lender to assess “ability to pay?” Moment No. 1: When prepping for a prescreen campaign and at origination. Many lenders leverage an income estimation model, designed to give an indication of the customer’s capacity to take on additional debt by providing an estimation of their annual income. Within the model, multiple attributes are used to calculate the income, including: Number of accounts Account balances Utilization Average number of months since trade opened Combined, all of these insights determine a customer’s current obligations, as well as an estimation of their current income, to see if they can realistically take on more credit. The right models and criteria on the front-end – whether used when a consumer applies for new credit or when a lender is executing a prescreen campaign to acquire new customers – minimizes the risk for default. It’s a no-brainer. Moment No. 2: When a customer is already on your books. As the Bankrate study mentioned, sudden life events can send some customers’ lives into a financial tailspin. On the other hand, financial circumstances can change for the better too. Aggressively paying down a HELOC, doubling down on a mortgage, or wiping out a bankcard balance could signal an opportunity to extend more credit, while the reverse could be the first signs of payment stress. Attaching triggers to accounts can give lenders indications on what to do with either scenario, helping to grow a portfolio and protect it. Moment No. 3: When an account goes south. While a lender hates to think any of its accounts will plummet into collections, sometimes, it’s inevitable. Even prime customers fall behind, and suddenly financial institutions are faced with looking at collections strategies. Where should they place their bets? You can’t treat all delinquent customer equally and work the accounts the same way. Collection resources can be wasted on customers who are difficult or impossible to recover, so it’s best to turn to predictive analytics and a collections scoring strategy to prioritize efforts. Again, who has the greatest ability to pay? Then place your manpower on those individuals where you can recover the most dollars. --- Assessing one’s ability to pay is a cornerstone to the financial services business. The quest is to find the sweet spot with a combination of application data, behavioral data and credit risk scoring analytics.

His car, more than 10 years old and not worth salvaging, was in the shop again. Time to invest in something new – or at least “new-ish.” He headed to a local dealership, selected a practical model and applied for financing. “We can’t give you a loan,” said the manager. “Your income is not high enough, but perhaps if you bring in a co-signer ...” Denied. Her college degree hung on the wall of her childhood bedroom. In the months since she celebrated graduation with family and friends, she landed a job, but not one providing enough income to cover rent, a car payment and her hefty student loan payments. “I didn’t realize my payments would be so high,” said the woman. “I don’t know how I’ll ever climb out from under this debt and start my life.” Stalled. His attempt at applying for a bankcard, much needed to begin the journey of establishing credit in the country, was met with failure. “We can’t find any credit history on you,” says the lender. “Try again in the future.” Invisible. These stories are all too common in America. A lack of financial education, coupled with a few poor choices, can derail an individual’s financial trajectory. More light has certainly been shone on the topic of financial education and the importance of making smart credit decisions from a young age, but there is no nationwide financial education program offered in schools, and many parents feel ill-equipped to handle the task. Consider a few of these numbers: 71 percent of college grads recently surveyed by Experian said they did not learn about credit and debt management in college, giving their schools an average grade of “C” when it comes to preparing them to manage credit and debt after college The latest "State of Credit" revealed the average debt per consumer is $29,093 39 percent of newlyweds say credit scores is a source of stress in their marriage Money management is tough, and we expect people to just figure it out. But clearly, that’s not working. So we need to think about the world of credit differently. As Experian says, we need to treat it as a skill. We need to practice and learn and adjust. As you get better at credit, it opens doors, creates opportunities, and enables people to live the lives they wish to live. Suddenly, you can get the car loan, move out, have access to credit cards, and manage it all responsibly. In other words, you claim financial health. On the other hand, if you don’t work at this skill, a lack of financial health ensues. Unruly amounts of debt, irregular income and sporadic savings create stress, resentment and pain. Increasingly, more financial institutions are boosting efforts to educate about credit. Schools are exploring curriculum to talk finances and inject real-life money management scenarios into everyday lessons. Millennials are seeking transparency around credit transactions. The more financially healthy consumers we have in this country, building credit skills, means overall economies will grow. So yes, financial health matters. It matters to individuals, to lending institutions, to retailers and to communities big and small. Building those credit skills is essential. Your health depends on it.

Is the speed of fraud threatening your business? Like many other fraud and compliance teams, your teams may be struggling to keep up with new business dynamics. The following trends are changing the way consumers do business with you: 35 percent year-over-year growth in mobile commerce More than $27 billion forecasted value of mobile payment transactions in 2016 45 percent of smartphone owners using a mobile device to make a purchase every month More than 1 billion mobile phone owners will use their devices for banking purposes by the end of 2015 In an attempt to stay ahead of fraud, systems have become more complex, more expensive and even more difficult to manage, leading to more friction for your customers. How extensive is this impact? 30 percent of online customers are interrupted to catch one fraudulent attempt One in 10 new applicants may be an imposter using breached data $40 billion of legitimate customer sales are declined annually because of tight rules, processes, etc. This rapid growth only reinforces the need for aggressive fraud prevention strategies and adoption of new technologies to prepare for the latest emerging cybersecurity threats. Businesses must continue their efforts to protect all parties’ interests. Fraudsters have what they need to be flexible and quick. So why shouldn’t businesses? Introducing CrossCore™, the first smart plug-and-play platform for fraud and identity services. CrossCore uses a single access point to integrate technology from different providers to address different dangers. When all your fraud and identity solutions work together through a single application program interface, you reduce friction and false positives — meaning more growth for your business. View our recent infographic on global fraud trends

What you give, you get. At least that is what popular philosophers claim. And if you think about it, this statement is also applicable to the world of data accuracy. As organizations of all sizes increasingly rely on data to interact with customers and create insights to drive strategy, it’s no secret bad data can quickly lead a company or financial institution down the wrong path, even landing them into regulatory troubles. A recent Experian Data Quality study found: Seventy-five percent of organizations believe inaccurate data is undermining their ability to provide an excellent customer experience. Sixty-five percent of organizations wait until there are specific issues with their data before they address and fix them. Fifty-six percent of organizations believe mistakes can be attributed to human error. For years, organizations have wanted good data simply for operational efficiencies and cost savings, but now a shift has taken place where businesses are using data for nearly every aspect of their organization. The majority of sales decisions are expected to be driven by customer data by 2020, with companies determined to turn data into actionable insight to find new customers, increase customer retention, better understand their needs, and increase the value of each customer. Additionally, the Fair Credit Reporting Act (FCRA) requires those contributing data to provide accurate and complete information to the credit reporting agencies. If they fail to meet accuracy obligations when reporting negative account histories to credit reporting companies, the result could be bureau action and fines. Organizations still deal with a high degree of inaccurate data because there are a number of challenges to maintaining it. Some of them are external forces, but many are internal challenges – most notably a reliance on reactive data management strategies. The biggest problem organizations face around data management today actually comes from within. Businesses get in their own way by refusing to create a culture around data and not prioritizing the proper funding and staffing for data management. Many businesses know they need to improve their data quality, but often have a hard time defining why an investment is needed in the current structure. Solutions exist to get in front of data accuracy challenges. DataArc 360 Powered by Experian Pandora, for example, is designed to check the consumer credit information provided by data furnishers prior to submission to credit bureaus. This allows data suppliers to take more of a proactive approach to ensuring the accuracy of information, that may result in fewer credit disputes and a more positive interaction between consumers and their credit. Creating a clear governance plan, and centralizing data management policies and policies can also clean up internal challenges and improve accuracy standards. The importance of data cannot be neglected, but again, the data has to be clean for it to matter. What you give is what you’ll get.

Experian cited in Mobile Fraud Management Solutions report from Forrester as having the most capabilities and one of the highest estimated revenues in total fraud management

Part four in our series on Insights from Vision 2016 fraud and identity track It was a true honor to present alongside Experian fraud consultant Chris Danese and Barbara Simcox of Turnkey Risk Solutions in the synthetic and first-party fraud session at Vision 2016. Chris and Barbara, two individuals who have been fighting fraud for more than 25 years, kicked off the session with their definition of first-party versus third-party fraud trends and shared an actual case study of a first-party fraud scheme. The combination of the qualitative case study overlaid with quantitative data mining and link analysis debunked many myths surrounding the identification of first-party fraud and emphasized best practices for confidently differentiating first-party, first-pay-default and synthetic fraud schemes. Following these two passionate fraud fighters was a bit intimidating, but I was excited to discuss the different attributes included in first-party fraud models and how they can be impacted by the types of data going into the specific model. There were two big “takeaways” from this session for me and many others in the room. First, it is essential to use the correct analytical tools to find and manage true first-party fraud risk successfully. Using a credit score to identify true fraud risk categorically underperforms. BustOut ScoreSM or other fraud risk scores have a much higher ability to assess true fraud risk. Second is the need to for a uniform first-party fraud bust-out definition so information can be better shared. By the end of the session, I was struck by how much diversity there is among institutions and their approach to combating fraud. From capturing losses to working cases, the approaches were as unique as the individuals in attendance This session was both educational and inspirational. I am optimistic about the future and look forward to seeing how our clients continue to fight first-party fraud.

Part 3 in our series on Insights from the Vision 2016 fraud and identity track Our Vision 2016 fraud track session titled “Deployment Made Easy — solving new fraud problems by Adapting Legacy Solutions” offered insights into the future of analytics and the mechanisms for delivering them. The session included two case studies, the first of which highlighted a recently completed project in which an Experian client struggling with rising application fraud losses had to find a way to deploy advanced analytics without any IT resources. To assist the customer, data passing through an existing customer interface was reformatted and redirected to our Precise ID® platform. Upon arrival in Precise ID, a custom-built fraud scoring model was invoked. The results were then translated back into the format used by the legacy interface so that they could be ingested by the customer’s systems. This case study illustrates the key value proposition of Experian’s new CrossCoreTM fraud and identity platform. CrossCore features a similar “translation layer” for inquiries coming into Experian’s fraud and identity tools that will allow customers to define fraud-screening workflows that call a variety of services. The IT burden for connecting the inquiry to various Experian and non-Experian services will fall on Experian — sparing the customer from the challenge of financing and prioritizing IT resources. Similarly, the output from CrossCore will provide a ready-to-consume response that integrates directly with our customers’ host systems. The audience showed keen interest in the “here and now” illustration of what CrossCore will enable. Our second case study was provided by Eric Heikkila at Amazon Web Services™ and focused on the future of analytics. For an audience accustomed to the constraints of developing advanced analytics in a rigid data-structure, Amazon’s description of a “data lake” was a fascinating picture of what’s possible. The data lake offers the simultaneous ability to accommodate existing structured customer data along with new unstructured data in an infinitely scalable data set. Equally important is the data lake’s ability to accommodate an unlimited array of data mining and analytical tools. Amazon’s message was clear and simple — the fraud industry’s trepidation around the use of big data is misplaced. The fear of making the wrong choice of data storage and analytical tools is unnecessary. To illustrate this point, Eric shared an Amazon Web Services case study that used FINRA (Financial Industry Regulatory Authority). FINRA is responsible for overseeing U.S. securities markets to ensure that rules are followed and integrity is maintained. Amid a bewildering set of ever-changing regulations and peak volumes of 35 trillion per day — yes, trillion — Amazon’s data lake supports both the scale and analytical demands of a complex industry. As the delivery and access to fraud products is made easy by CrossCore, the data and analytics will expand through the use of services like Amazon’s data lake. As the participants will agree, the future of fraud technology is closer than you think!

Part 2 in our series on Insights from the Vision 2016 fraud and identity track With the growing number of data breach incidents taking place the stolen data from those attacks is being used to carry out social engineering attacks used to commit call center fraud. A recent study stated that global call center fraud has increased more than 45% in the last three years as fraudsters use social engineering to steal data and turn profits. The same report found that criminals might make up to 5 calls to a center, pretending to be the victim, before completing a fraudulent transaction. The importance of strong call center authentication procedures is greater than ever. At the 35th annual Vision Conference, Bobbie Paul from Experian’s Global Consulting Practice, Stefan Schubert from JPMorgan Chase and I led a session about call center authentication. After introductions and a discussion about existing call center identity authentication techniques, Stefan took the podium and provided an excellent overview of how his company approaches call center authentication. He made an interesting point — despite introducing friction into his process, he was not of the opinion that knowledge-based authentication (KBA) was going away any time soon because of how deeply it is embedded into their processes and its applicability to most consumers. He also called out the importance of reviewing KBA configurations regularly to adjust which questions are being asked and the positive implication to deterring fraudsters. Bobbie followed Stefan to discuss emerging call center authentication technologies, including a new take on an old tool — document imaging. She also discussed the notion of phone printing, which does not specifically evaluate the voice on the phone, but looks at the characteristics of the call itself, including the type of phone being used and the environment from which the call is being made. One of the highlights of the session was the interaction with the audience — including a demonstration of how, with a little distraction, it was easy to walk away with an audience member’s phone, how a fraudster could access and compromise a phone and how a gummy bear could be used to defeat fingerprint biometrics. What I, and many others, took away from this is that even with newer fraud detection tools available, incorporating tried-and-true methods like KBA is still an important step into a holistic fraud detection strategy.

Industry’s first smart plug-and-play fraud platform allows companies to connect their own solutions, Experian products and third-party vendors in one place to better protect their customers from fraud threats Experian unveiled the fraud and identity industry’s first open platform designed to catch fraud faster, improve compliance and enhance the customer experience. Experian’s CrossCore™ gives companies an easier way to connect any new or existing tools and systems in one place, whether they are Experian, internal or third-party partner solutions. This “plug-and-play” capability allows companies to rapidly adapt to changing conditions and risks. “Our clients have expressed frustration over the lack of a truly holistic industry solution that delivers the level of confidence and control they need without requiring a massive multiyear project to replace everything they have,” said Steve Platt, global executive vice president, Fraud and Identity, Experian. “New fraud threats, updates to regulatory requirements and customer expectations for a hassle-free experience are making it challenging for fraud and compliance teams to keep up. CrossCore will give them the flexibility they need to balance customer protection with customer experience.” The CrossCore open platform enables organizations to manage services through a common access point that supports a layered approach to managing risks across providers. CrossCore includes powerful workflow and strategy design capabilities that allow fraud and compliance teams to create and adapt strategies based on evolving threats and business needs. This helps them to respond more quickly and reduces the burden on IT. Fraud and compliance teams must constantly respond to new fraud threats and changing regulatory requirements by implementing new tools on top of existing solutions. “A layered approach is imperative, because fraudsters can break through each layer individually, but they will face greater barriers with each additional layer imposed,” said Avivah Litan, vice president and distinguished analyst, Security and Privacy, of Gartner.[1] Over time, as layers have been added and fortified, systems have become increasingly complex, expensive to integrate and difficult to manage, often increasing customer friction. A key feature of the CrossCore fraud platform is the ease of integration with third-party partner solutions. At launch, CrossCore will support fraud and identity services provided by third-party partners, including Acxiom® (Identity Solutions), TeleSign and many others already integrated with Experian solutions, with more being added to the platform. Previously, integrating third-party solutions required tremendous time and effort, which often challenged in-house teams to execute in a timely, efficient manner. Through CrossCore, the responsibility of integrating additional tools and systems moves away from those teams to the platform itself, enabling clients to select best-in-class solutions from multiple providers without creating a strain on resources. Al Pascual, senior vice president, research director and head of fraud & security for Javelin, said, “There are so many great niche solutions to work with, and new ones come out almost every day. To really have a world-class approach, the client has to put all those little things together, because there never will be one vendor who does it all. The market challenge is about how to make it faster and easier to bring things together to enable a more dynamic and fluid approach to managing risk.” CrossCore features Common access through a flexible API connects disparate systems to improve risk controls while reducing integration cost and complexity An open approach enables clients to connect and optimize a portfolio of best-in-class solutions across Experian, third-party services and existing systems Powerful strategy design and workflow decisioning functions enable fraud and compliance teams to apply services in any combination to get the level of confidence required A modern Software as a Service (SaaS) architecture provides scalability and the ability to make strategy changes dynamically with no down time Experian, which offers fraud and identity services in more than 44 countries, developed CrossCore to address the widespread market need consistently expressed by its clients for a faster, easier way to get more out of their existing systems and add new tools to improve their customers’ experience while minimizing risk. Companies can begin accessing CrossCore immediately, with the ability to turn on Experian services through a single integration, connect their own fraud and identity capabilities with a common API and turn on new services as they are added. The initial release includes key Experian products: FraudNet for Account Opening; Hunter®, for application fraud detection; Prove-ID, for international identity verification; and Precise ID®, for U.S. identity verification, including knowledge-based authentication. (KBA). Third-party fraud and identity service providers can engage with CrossCore to connect their services. “Now, companies can implement a new approach to managing fraud and identity services — one that will give them greater control over their risk exposure and enable them to provide a safer and more enjoyable experience for their customers,” added Platt. Learn more about CrossCore at https://www.experian.com/crosscore [1]Gartner, Identity Proofing Revisited as Data Confidentiality Dies, Avivah Litan, Dec. 12, 2013; last reviewed on April 28, 2015