Ecommerce / Retail

Last week we had the pleasure of joining more than 400 clients at the 35th annual Vision Conference — connecting business leaders to ideas and solutions. Over the next few weeks, we’ll be sharing some insights from our fraud and identity dedicated session track. I had the pleasure of presenting alongside the U.S. Secret Service, and we had a packed session to discuss the Dark Web — what it is, how it’s accessed, how criminals are exploiting it to commit fraud and the human impact of the massive global cybercrime problem. According to McAfee®, cybercrime represents a $500 billion cost to the global economy — and that’s projected to rise to $600 billion this year, outpacing any other form of crime. With the Internet economy generating between $2 trillion and $3 trillion annually, that means cybercrime is extracting roughly 15 to 20 percent of the entire value created by the Internet. This is a massive problem, and it’s not going away. Unfortunately, there are countless tools and services to commit fraud available on the Web, providing attackers with the cloak of anonymity they need to compromise accounts, mimic legitimate users and submit fraudulent transactions. Device intelligence helps unmask these activities. It is a critical component to defend against the threat, and it provides insight into every interaction throughout a typical customer journey (from account setup to login and account maintenance to transactions). Without this visibility into users’ historical behavior and typical population patterns, organizations often have limited options to target attackers and identify anomalous behaviors. This is key to a successful cybercrime detection and mitigation strategy. Another important point in the session regarded recent law enforcement and private industry successes in identifying, tracking, apprehending and prosecuting online attackers. We thankfully have made significant strides in this area, as evidenced by the work of the Secret Service and other law enforcement organizations, but the collaboration must continue — and intensify. As mentioned in a CNBC story published on the same day as our presentation, the Dark Web is an increasingly mainstream source for everything from financial crime to drug trade and human trafficking. Unfortunately, most businesses are in the dark about the growing criminal underground, but Experian can help. With proper fraud expertise and innovative tools to defend against these ever-evolving threats, organizations can uncloak the attackers and safeguard the business.

False declines are often unwarranted and occur due to lack of customer information Have you ever been shopping online, excited to get your hands on the latest tech gadget, only to be hit with the all-too-common disappointment of a credit card decline? Whom did you blame? The merchant? The issuer? The card associations? The answer is probably all of the above. False declines like the situation described above provoke an onslaught of consumer emotions ranging from shock and dismay to frustration and anger. Of course, consumers aren’t the only ones negatively impacted by false declines. Many times card issuers lose their coveted “top of wallet” position and/or retailers lose revenue when customers abandon the purchase altogether. False declines are unpleasant for everyone, yet consumers struggle with this problem every day — and fraud controls are only getting tighter. How does the industry mutually resolve this growing issue? The first step is to understand why it occurs. Most false declines happen when the merchant or issuer mistakenly declines a legitimate transaction due to perceived high risk. This misperception is usually the result of the merchant or issuer not having enough information to verify the authenticity of the cardholder confidently. For example, the consumer may be a first-time customer or the purchase may be a departure from the card holder’s normal pattern of transaction activity. Research shows that lack of a holistic view and no cross-industry transaction visibility result in approximately $40 billion of e-commerce declines annually. Think about this for a minute — $40 billion in preventable lost revenue due to lack of information. Merchants’ customer information is often limited to their first-hand information and experience with consumers. To solve this growing problem, Experian® developed TrustInsight™, a real-time engine to establish trusted online relationships over time among consumers, merchants and issuers. It works by anonymously leveraging transactional information that merchants and financial institutions already have about consumers to create a crowd-sourced TrustScore™. This score allows first-time online customers to get a VIP experience rather than a brand-damaging decline. Another common challenge for merchants is measuring the scope of the false declines problem. Proactively contacting consumers, directly capturing feedback and quickly verifying transaction details to recoup potential lost sales are best practices, but merchants are often in the dark as to how many good customers are being turned away. The solution — often involving substantial operational expense — is to hold higher-risk orders for manual review rather than outright declining them. With average industry review rates nearing 30 percent of all online orders (according to the latest CyberSource Annual Fraud Benchmark Report: A Balancing Act), this growing level of review is not sustainable. This is where industry collaboration via TrustInsight™ offers such compelling value. TrustInsight can reduce the review population significantly by leveraging consumers’ transactions across the network to establish trust between individuals and their devices to automate more approvals. Thankfully, the industry is taking note. There is a groundswell of focus on the issue of false declines and their impact on good customers. Traditional, operations-heavy approaches are no longer sufficient. A trust-based industry-consortium approach is essential to enhance visibility, recognize consumers and their devices holistically, and ensure that consumers are impacted only when a real threat is present.
Adam Fingersh, senior vice president and general manager of Experian’s fraud and identity business, shared several fraud prevention strategies that businesses and consumers can use to manage risk and increase security while using Internet-enabled products, also known as the Internet of Things (IoT).

James W. Paulsen, Chief Investment Strategist for Wells Capital Management, kicked off the second day of Experian’s Vision 2016, sharing his perspective on the state of the economy and what the future holds for consumers and businesses alike. Paulsen joked this has been “the most successful, disappointing recovery we’ve ever had.” While media and lenders project fear for a coming recession, Paulsen stated it is important to note we are in the 8th year of recovery in the U.S., the third longest in U.S. history, with all signs pointing to this recovery extending for years to come. Based on his indicators – leverage, restored household strength, housing, capital spending and better global growth – there is still capacity to grow. He places recession risk at 20 to 25 percent – and only quotes those numbers due the length of the recovery thus far. “What is the fascination with crisis policies when there is no crisis,” asks Paulsen. “I think we have a good chance of being in the longest recovery in U.S. history.” Other noteworthy topics of the day: Fraud prevention Fraud prevention continues to be a hot topic at this year’s conference. Whether it’s looking at current fraud challenges, such as call-center fraud, or looking to future-proof an organization’s fraud prevention techniques, the need for flexible and innovative strategies is clear. With fraudsters being quick, and regularly ahead of the technology fighting them, the need to easily implement new tools is fundamental for you to protect your businesses and customers. More on Regulatory The Military Lending Act has been enhanced over the past year to strengthen protections for military consumers, and lenders must be ready to meet updated regulations by fall 2016. With 1.46 million active personnel in the U.S., all lenders are working to update processes and documentation associated with how they serve this audience. Alternative Data What is it? How can it be used? And most importantly, can this data predict a consumer’s credit worthiness? Experian is an advocate for getting more entities to report different types of credit data including utility payments, mobile phone data, rental payments and cable payments. Additionally, alternative data can be sourced from prepaid data, liquid assets, full file public records, DDA data, bill payment, check cashing, education data, payroll data and subscription data. Collectively, lenders desire to assess someone’s stability, ability to pay and willingness to repay. If alternative data can answer those questions, it should be considered in order to score more of the U.S. population. Financial Health The Center for Financial Services Innovation revealed insights into the state of American’s financial health. According to a study they conducted, 57 percent of Americans are not financially healthy, which equates to about 138 million people. As they continue to place more metrics around defining financial health, the center has landed on four components: how people plan, spend, save and borrow. And if you think income is a primary factor, think again. One-third of Americans making more than $60k a year are not healthy, while one-third making less than $60k a year are healthy. --- Final Vision 2016 breakouts, as well as a keynote from entertainer Jay Leno, will be delivered on Wednesday.

It’s impossible to capture all of the insights and learnings of 36 breakout sessions and several keynote addresses in one post, but let’s summarize a few of the highlights from the first day of Vision 2016. 1. Who better to speak about the state of our country, specifically some of the threats we are facing than Leon Panetta, former Secretary of Defense and Director of the CIA. While we are at a critical crossroads in the United States, there is room for optimism and his hope that we can be an America in Renaissance. 2. Alex Lintner, Experian President of Consumer Information Services, conveyed how the consumer world has evolved, in large part due to technology: 67 percent of consumers made purchases across multiple channels in the last six months. More than 88M U.S. consumers use their smartphone to do some form of banking. 68 percent of Millennials believe within five years the way we access money will be totally different. 3. Peter Renton of Lend Academy spoke on the future of Online Marketplace Lending, revealing: Banks are recognizing that this industry provides them with a great opportunity and many are partnering with Online Marketplace Lenders to enter the space. Millennials are not the largest consumers in this space today, but they will be in the future. Sustained growth will be key for this industry. The largest platforms have everything they need in place to endure – even through an economic downturn.In other words, Online Marketplace Lenders are here to stay. 4. Tom King, Experian’s Chief Information Security Officer, addressed the crowds on how the world of information security is growing increasingly complex. There are 1.9 million records compromised every day, and sadly that number is expected to rise. What can businesses do? “We need to make it easier to make the bad guys go somewhere else,” says King. 5. Look at how the housing market has changed from just a few years ago: Inventory continues to be extraordinarily lean. Why? New home building continues to run at recession levels. And, 8.5 percent of homeowners are still underwater on their mortgage, preventing them from placing it on the market. In the world of single-family home originations, 2016 projections show that there will be more purchases, less refinancing and less volume. We may see further growth in HELOC’s. With a dwindling number of mortgages benefiting from refinancing, and with rising interest rates, a HELOC may potentially be the cheapest and easiest way to tap equity. 6. As organizations balance business needs with increasing fraud threats, the important thing to remember is that the customer experience will trump everything else. Top fraud threats in 2015 included: Card Not Present (CNP) First Party Fraud/Synthetic ID Application Fraud Mobile Payment/Deposit Fraud Cross-Channel FraudSo what do the experts believe is essential to fraud prevention in the future? Big Data with smart analytics. 7. The need for Identity Relationship Management can be seen by the dichotomy of “99 percent of companies think having a clear picture of their customers is important for their business; yet only 24 percent actually think they achieve this ideal.” Connecting identities throughout the customer lifecycle is critical to bridging this gap. 8. New technologies continue to bring new challenges to fraud prevention. We’ve seen that post-EMV fraud is moving “upstream” as fraudsters: Apply for new credit cards using stolen ID’s. Provision stolen cards into mobile wallet. Gain access to accounts to make purchases.Then, fraudsters are open to use these new cards everywhere. 9. Several speakers addressed the ever-changing regulatory environment. The Telephone Consumer Protection Act (TCPA) litigation is up 30 percent since the last year. Regulators are increasingly taking notice of Online Marketplace Lenders. It’s critical to consider regulatory requirements when building risk models and implementing business policies. 10. Hispanics and Millennials are a force to be reckoned with, so pay attention: Millennials will be 81 million strong by 2036, and Hispanics are projected to be 133 million strong by 2050. Significant factors for home purchase likelihood for both groups include VantageScore® credit score, age, student debt, credit card debt, auto loans, income, marital status and housing prices. More great insights from Vision coming your way tomorrow!

Four Experian employees reflect on financial lessons and challenges learned during their time served in the military. Pedro Martinez, based at Camp Lejeune in North Carolina, was earning a monthly salary of just $680 as a Private First Class for the Marine Corps. in 1988. Winter was nearing, and since he was living off base, he needed a heater. “I was able to purchase one with ‘easy credit’ for $15 per month, for 18 months,” said Martinez, now living in Costa Rica. “I ended up paying a lot more than driving to Kmart and getting one there if I had the money. But for the purchase I was able to make at the time, I had to finance it, and I remember the interest rate was almost 40 percent.” Fast forward decades later, and Martinez recalls those same “easy credits” and payday loans surround local bases. Advance paycheck services offering rates of 30 percent and beyond for brief, 15-day cycles abound. While military base consumer advisors can encourage personnel to steer clear, more formal protections have been lacking. Until now. “The Military Lending Act is definitely a great measure to assure a fair consumer treatment, regulate high-interest rates, and safeguard families from going bankrupt,” said Martinez. No one can tell the stories of military life better than those who have lived it. They understand the training, sacrifices, day-to-day grind as well as the experiences of managing life on base and far from home. Financial education is lacking among all consumer groups in the country, and it is easy for a few credit mishaps to take individuals to a place where they soon find themselves struggling to get out of debt and obtain affordable credit. “I witnessed countless friends in the military finance furniture, receive cash advances and take out loans on their cars, which ultimately hurt them financially,” said Marshall Abercrombie, who served five years as a Navy Corpsman with the Marines. “Unfortunately, there are more title loans, cash advance and furniture leasing companies found within military towns compared to legitimate financial institutions. So, when you combine word-of-mouth, inexperience and easy access you end up with necessary legislature like the Military Lending Act.” Abercrombie, who currently resides in the southeast, claims his first “solo” experience with a financial institution saved him from falling down a bad path. “I can remember gripping my diploma thinking ‘now what am I going to do with all this money I’m about to start making?’” said Abercrombie. “Fortunate for me I was immediately greeted by a very eager representative of Armed Forces Bank. Despite being only 19 years old, looking back it’s apparent how much opportunity someone like me represented to a bank given I now had a government job that required I set up auto-deposit for future paychecks.” Especially for those military members sent overseas, opportunities and challenges can be unique. Michael Kilander, now a Southern California resident, was deployed overseas in Germany in the early 90s with his wife and ran into trouble with a large U.S. bank. “We had a credit card that we fell a month behind in paying,” says Kilander. “We had the money each time but did not receive the statement/ bill until a week after the due date. The military mail system took a great deal of time, particularly if you lived off base in the local Germany economy, as we did. We asked if the bank could mail the bill a little earlier, but they refused and were uninterested in the challenges of the APO system. Consequently we had to keep track of the amount spend on the card and estimate the likely charges and pay before we received the bill. We switched cards a few months later.” Raymond Reed, who enlisted with the Navy out of high school, was luckily advised by his parents to join a military credit union. “I did not realize I needed credit, and assumed credit was only offered to those with savings,” said Reed. “During my Navy tour, I joined a military credit union and since I did not have standard expenses, other than car insurance, which was covered by my paychecks. At the end of my tour, I saved and paid cash for my motorcycle, as I was accustomed to since I had a nice savings established.” The stories of stresses and opportunities surrounding military and credit are diverse and widespread, but the positive news is updated regulations will add increased protections. Learn more about the Servicemembers Civil Relief Act and now enhanced Military Lending Act to understand the varying protections, as well as discover how financial institutions can comply and best support military credit consumers and their families.

Television had its Twilight Zone, the Emmy-winning anthology series featuring tales rich in fantasy, morality and irony. Today's economy has its own Twilight Zone. It lies between the legitimate economy with its weekly paychecks, W2 forms and 401(K) plans, and the underground economy with its unreported, all-cash transactions. Call them "The Unbanked." Call them "The Credit Invisibles." Whatever label you choose, these men and women -- who number in the millions - want access to credit, but can’t be easily accessed with traditional credit models, and they lack a smooth on-ramp to grow in the credit universe. How a Worker Becomes "Credit Invisible" America's "credit invisibles" tend to be minimum- or low-wage workers. They exist in virtually every industry, although they tend to be concentrated in agriculture, food service, construction and manufacturing. Some work full-time for a single employer, while others work part-time or on a gig-by-gig basis. The FDIC estimates some 10 million Americans currently fit the definition of unbanked, while an additional 28.4 million are underbanked. Instead of traditional banks, this population tends to use the services of private check-cashing services and payday lenders for their financial services, which is not always advantageous for the consumer with these services’ sizeable expenses and transaction fees. The Payroll Card Alternative Recognizing the perils inherent in the current system, a number of companies have developed solutions to help those individuals who cannot and will not establish traditional checking and savings accounts. SOLE® Financial, a financial services company headquartered in Portland, Ore, offers the SOLE Visa® Payroll Card, allowing employees to enjoy the benefits associated with direct deposit checking accounts without the costs and restrictions traditional banks often impose. "From a payroll standpoint, paycards function just like bank accounts,” explained Taylor Ellsworth, content marketing manager for SOLE Financial. “The transfer happens on the exact same timeline as the paychecks that employers deposit to traditional bank accounts.” Additionally, any bill from a vendor that accepts electronic payments - either online or with a card number over the phone - can accept payments from the SOLE paycard. "For bills like rent, which sometimes can only be paid with a check or money order, cardholders can log in and use the bill pay option for $1 per bill to have a check issued to their landlord -- or any other recipient -- from their account,” said Ellsworth. Helping Credit Invisibles Build Personal Credit Files Another way companies are helping credit invisibles become visible is by considering non-retail payments, such as payments to utility companies, as part of a personal payment history. Traditionally payments to gas, electric, telephone, cable and other household service providers are generally not being reported unless the consumer is severely delinquent and thus on-time payment history is not included in credit scores. Experian recently investigated how including payments to energy utilities could affect men and women with "thin-file" credit portfolios. The subprime and nonprime consumers in the study received the greatest positive score impact, with 95 percent of subprime consumers and 75 percent of nonprime consumers experiencing a positive score change. A resounding 82 percent of subprime consumers in the study received a positive score impact of 11 points or more. The average VantageScore® credit score change for all participants was an increase of 28 points. Experian concluded, "positive energy-utility reporting presents an opportunity for energy companies to play a key role in helping their consumers build credit history. The ability for many of these consumers to become credit-scoreable, build a more robust credit file and potentially migrate to a better risk segment simply by paying their energy bills on time each month is powerful and represents an opportunity for positive change that should be not overlooked." Conclusion With income inequality growing, there is an increasing pressure to find ways to improve the prospects of the tens of millions of Americans who live on the farthest edges of the American economy. New technologies and ways of looking at credit can offer the unbanked and the under-banked ways to improve their economic situation and move closer to the mainstream. By bringing these millions into the light, those who issue and evaluate credit will create millions of new customers who can, in turn, add new energy to the American economy.

This article first appeared in Baseline Magazine Since it is possible for cyber-criminals to create a synthetic person, businesses must be able to differentiate between synthetic and true-party identities. Children often make up imaginary friends and have a way of making them come to life. They may come over to play, go on vacation with you and have sleepover parties. As a parent, you know they don’t really exist, but you play along anyway. Think of synthetic identities like imaginary friends. Unfortunately, some criminals create imaginary identities for nefarious reasons, so the innocence associated with imaginary friends is quickly lost. Fraudsters combine and manipulate real consumer data with fictitious demographic information to create a “new” or “synthetic” individual. Once the synthetic person is “born,” fraudsters create a financial life and social history that mirrors true-party behaviors. The similarities in financial activities make it difficult to detect good from bad and real from synthetic. There really is no difference in the world of automated transaction processing between you and a synthetic identity. Often the synthetic “person” is viewed as a thin or shallow file consumer— perhaps a millennial. I have a hard time remembering all of my own passwords, so how do organized “synthetic schemes” keep all the information usable and together across hundreds of accounts? Our data scientists have found that information is often shared from identity to identity and account to account. For instance, perhaps synthetic criminals are using the same or similar passwords or email addresses across products and accounts in your portfolio. Or, perhaps physical address and phone records have cross-functional similarities. The algorithms and sciences are much more complex, but this simplifies how we are able to link data, analytics, strategies and scores. Identifying the Business Impact of Synthetic-Identity Fraud Most industry professionals look at synthetic-identity fraud as a relatively new fraud threat. The real risk runs much deeper in an organization than just operational expense and fraud loss dollars. Does your fraud strategy include looking at all types of risk, compliance reporting, and how processes affect the customer experience? To identify the overall impact synthetic identities can have on your institution, you should start asking: Are you truly complying with "Know Your Customer" (KYC) regulations when a synthetic account exists in your active portfolio? Does your written "Customer Identification Program" (CIP) include or exclude synthetic identities? Should you be reporting this suspicious activity to the compliance officer (or department) and submitting a suspicious activity report (SAR)? Should you charge off synthetic accounts as credit or fraud losses? Which department should be the owner of suspected synthetic accounts: Credit Risk, Collections or Fraud? Do you have run any anti-money laundering (AML) risk when participating in money movements and transfers? Depending on your answers to the above questions, you may be incurring potential risks in the policies and procedures of synthetic identity treatment, operational readiness and training practices. Since it is possible to create a synthetic person, businesses must be able to differentiate between synthetic and true-party identities, just as parents need to differentiate between their child's real and imaginary friends.

Device emulators — wolves in sheep’s clothing Despite all the fraud prevention systems and resources in the public and private sectors, online fraud continues to grow at an alarming rate, offering a low-risk, high-reward proposition for fraudsters. Unfortunately, the Web houses a number of easily accessible tools that criminals can use to perpetrate fraud and avoid detection. The device emulator is one of these tools. Simply put, a device emulator is one device that pretends to be another. What began as innovative technology to enable easy site testing for Web developers quickly evolved into a universally available tool that attackers can exploit to wreak havoc across all industry verticals. While it’s not new technology, there has been a significant increase in its use by criminals to deceive simple device identification and automated risk-management solutions to carry out fraudulent activities. Suspected device emulation (or spoofing) traffic historically has been difficult to identify because fraud solutions rely heavily on reputation databases or negative lists. Detecting and defeating these criminals in sheep’s clothing is possible, however. Leveraging Experian’s collective fraud intelligence and data modeling expertise, our fraud research team has isolated several device attributes that can identify the presence of an emulator being used to submit multiple transactions. Thanks to these latest FraudNet rule sets, financial institutions, ecommerce merchants, airlines, insurers and government entities alike now can uncloak and protect against many of these cybercriminals. Unfortunately, device emulators are just one of many tools available to criminals on the Dark Web. Join me at Vision 2016, where U.S. Secret Service and I will share more tales from the Dark Web. We will explore the scale of the global cybercrime problem, walk through the anatomy of a typical hack, explain how hackers exploit browser plug-ins, and describe how enhanced device intelligence and visibility across all channels can stop fraudsters in their tracks. Listen to Mike Gross as he shares a short overview of his Vision 2016 breakout session in this short video. Don’t miss this innovative Vision 2016 session! See you there.

April is Financial Literacy Month, a special window of time dedicated to educating Americans about money management. But as stats and studies reveal, it might be wise to spend every month shining some attention on financial education, an area so many struggle to understand. Obviously no one wants to talk money day in and day out. It can be complicated, make us feel bad and serve as a source of stress. But as the saying goes, information is power. Over the years, Experian has worked to understand the country’s state of credit. Which states sport higher scores? Which states struggle? How do people pay down their debts? And what are the triggers for when accounts trail into collections? In the consumer space especially, we’ve surveyed individuals about how they feel about their own credit as it pertains to a number of different variables and life stages. Home Buying: 34% of future home buyers say their credit might hurt their ability to purchase a home 45% of future home buyers delayed a purchase to improve their credit to get better interest rates Holiday Shopping: 10% of consumers and 18% of millennials say holiday shopping has negatively affected their credit score Newlywed Life: 60% believe it is important for their future spouse to have a good credit score 39% say their spouse’s credit score or their credit score has been a source of stress in their marriage 35% of newlyweds believe they are “very knowledgeable” regarding credit scores and reports And let’s not forget Millennials: 71% of millennials believe they are knowledgeable when it comes to credit, yet: millennials overestimate their credit score by 29 points 32% do not know their credit score 61% check their credit report less than every 3 months 57% feel like the odds are stacked against them when it comes to finances and 59% feel like they are “going it alone” when it comes to finances The message is clear. Finances are simply a part of life, but can obviously serve as a source of stress. Establishing and growing credit often starts at a young age, and runs through every major life event. Historically, high school is where the bulk of financial literacy programs have targeted their efforts. But even older adults, who have arguably learned something about personal finances by managing their own, could stand a refresher on topics ranging from refinancing to retirement to reverse mortgages. Over the next month, Experian will touch on several timely financial education topics, including highlighting the top credit questions asked, the future of financial education in the social media space, investing in retirement, ways to teach your kids about money, and how to find a legit credit counselor. But Experian explores financial education topics weekly too, committed to providing consistent resources to both businesses and consumers via weekly tweet chats, blog posts and live discussions on periscope. There is always an opportunity to learn more about finances. Throughout the year, different issues pop up, and milestone moments mean we need to brush up on the latest ways to spend and save. It’s nice so many financial institutions make a special point to highlight financial education in April, but hopefully consumers and lenders alike continue to dedicate time to this important topic every month. Managing money is a lifelong task, so tips and insights are always welcome. Right? Check out the wealth of resources and pass it on. For a complete picture of consumer credit trends from Experian's database of over 230 million consumers, purchase the Experian Market Intelligence Brief.

Identity management traditionally has been made up of creating rigid verification processes that are applied to any access scenario. But the market is evolving and requiring an enhanced Identity Relationship Management strategy and framework. Simply knowing who a person is at one point in time is not enough. The need exists to identify risks associated with the entire identity profile, including devices, and the context in which consumers interact with businesses, as well as to manage those risks throughout the consumer journey. The reasoning for this evolution in identity management is threefold: size and scope, flexible credentialing and adaptable verification. First, deploying a heavy identity and credentialing process across all access scenarios is unnecessarily costly for an organization. While stringent verification is necessary to protect highly sensitive information, it may not be cost-effective to protect less-valuable data with the same means. A user shouldn’t have to go through an extensive and, in some cases, invasive form of identity verification just to access basic information. Second, high-friction verification processes can impede users from accessing services. Consumers do not want to consistently answer multiple, intrusive questions in order to access basic information. Similarly, asking for personal information that already may have been compromised elsewhere limits the effectiveness of the process and the perceived strength in the protection. Finally, an inflexible verification process for all users will detract from a successful customer relationship. It is imperative to evolve your security interactions as confidence and routines are built. Otherwise, you risk severing trust and making your organization appear detached from consumer needs and preferences. This can be used across all types of organizations — from government agencies and online retailers to financial institutions. Identity Relationship Management has three unique functions delivered across the Customer Life Cycle: Identity proofing Authentication Identity management Join me at Vision 2016 for a deeper analysis of Identity Relationship Management and how clients can benefit from these new capabilities to manage risk throughout the Customer Life Cycle. I look forward to seeing you there!

It’s the “Battle of the Sexes” credit edition. Who sports higher scores, less debt and more on-time payments? According to Experian’s latest analysis, women take the credit title. Thank you very much. The report analyzed multiple categories including credit scores, average debt, number of open credit cards, utilization ratios, mortgage amounts and mortgage delinquencies of men and women in the United States. Results revealed: Women’s average credit score of 675 compared to men’s score of 670 Women have 3.7 percent less average debt than men Women have 23.5 percent more open credit cards Women and men have the same revolving utilization ratio of 29.9 percent Women’s average mortgage loan amount is 7.9 percent less than men’s Women have a lower incidence of late mortgage payments by 8.1 percent “There were several gaps between men and women in this study, including the five-point credit score lead that the women hold,” said Michele Raneri, Experian’s Vice President of Analytics and New Business Development. “Even with more credit cards, women have fewer overall debts and are managing to pay those debts on time.” The report also takes a look at the vehicle preferences of men and women and how those choices play into their overall credit and financial health. Below are the top-line results: Women were more likely to purchase a more functional, utilitarian vehicle, while men tended to lean toward sports cars and trucks The top three vehicle segments men purchased in 2015 were mid-size pickup trucks, large pickup trucks and standard specialty cars. In fact, they were 1.37 times more likely to purchase a mid-sized pickup truck than the general population The top three vehicle segments for women were small crossover-utility vehicles, mid-size sports-utility vehicles and compact crossover-utility vehicles. Women were 1.40 times more likely to purchase the small crossover-utility vehicle than the general population Experian conducted a similar study, comparing men and women on various credit attributes in 2013. At that time, women also scored higher than men in the credit score category - holding steady with a 675 VantageScore® credit score compared to the men’s 674 VantageScore® credit score, but the gap has widened, with the men’s score further lowering to 670. While men’s scores have dropped since 2013, the overall financial health for both sexes is strong. Most notably, the mortgage 60-plus delinquency rate has dropped significantly. In the 2013 pull, men were tracking at 5.7 percent and women were 5.3 percent. Today, those numbers have dropped to .86 percent for men and .79 percent for women. What a difference a few years has made in regards to the recovering housing market. Time will tell if the country’s state of credit will continue to trend higher, as indicated in the 2015 annual report, or if the buzz of potential recession and an election year will reverse the positive trend. As for now, the women once again claim bragging rights as it pertains to credit. Analysis methodology The analysis is based on a statistically relevant, sampling of depersonalized data of Experian’s consumer credit database from December 2015. Gender information was obtained from Experian Marketing Services.

Proven identity and device authentication to minimize identity tax return fraud Identity fraud places an enormous burden on its victims and presents a challenge to businesses, organizations and government agencies, including the IRS and all state revenue authorities. Tax return fraud occurs when an attacker uses a consumer’s stolen Social Security number and other personal information to file a tax return, often claiming a significant refund. The IRS is challenged by innovative fraudsters continually trying to outsmart its current risk strategies around prevention, detection, recovery and victim assistance. And with the ever-increasing number of identity data compromised and tax return fraud victims, it’s necessary to question whether tax preparation companies are doing all they can to keep personally identifiable information (PII) secure and screen for fraud before forms are submitted. “ID theft isn’t just credit card fraud,” said Rod Griffin, Director of Public Education for Experian. A recent Experian online survey indicated that nearly 76 percent of consumers are familiar with ID theft and tax fraud — up significantly from the past two years. And 28 percent of those surveyed have been a victim or know a victim of tax fraud. To protect all parties’ interests, tax preparation agencies are challenged by today’s savvy fraudsters who have reaped the benefits of recent breaches. In order to protect consumers, organizations need to apply comprehensive, data-driven intelligence to help thwart identity fraud and the use of stolen identity data via fraudulent returns. The key to securing transactions, reducing friction and providing a consistently satisfying customer experience, online and offline, is authenticating consumers in a clear and frictionless environment. As a result, it’s necessary to have reliable customer intelligence based on both high-quality contextual identity and device attributes alongside other authentication performance data. Comprehensive customer intelligence means having a holistic, bound-together view of devices and identities that equips companies and agencies with the tools to balance cost and risk without increasing transactional friction. Businesses and agencies must not rely on a singular point of customer intelligence gathering and decisioning, but must move to more complex device identification and out-of-wallet verification procedures. Effective solutions typically involve a layered approach with several of the following: Identity transaction link analysis and risk attribute derivation Device intelligence and risk assessment Credit and noncredit data and risk attributes Multifactor authentication, using one-time passcodes via SMS messaging Identity risk scores Dynamic knowledge-based authentication questions Traditional PII validation and verification Biometrics and remote document verification Out-of-band alerts, communications and confirmations Contextual account, transaction and channel purview Additionally, government agencies must adhere to recognized standards, such as those prescribed by the National Institute of Standards and Technology to establish compliance. The persistent threat of tax fraud highlights the urgent need for businesses and agencies to continue educating consumers and more importantly, to improve the strategic effectiveness of their current solutions processes. Learn more about Experian Fraud and Identity Solutions, including government-specific treatments, and how the most effective fraud prevention and identity authentication strategy leverages multiple detection capabilities to highlight attackers while enabling a seamless, positive experience for legitimate consumers.
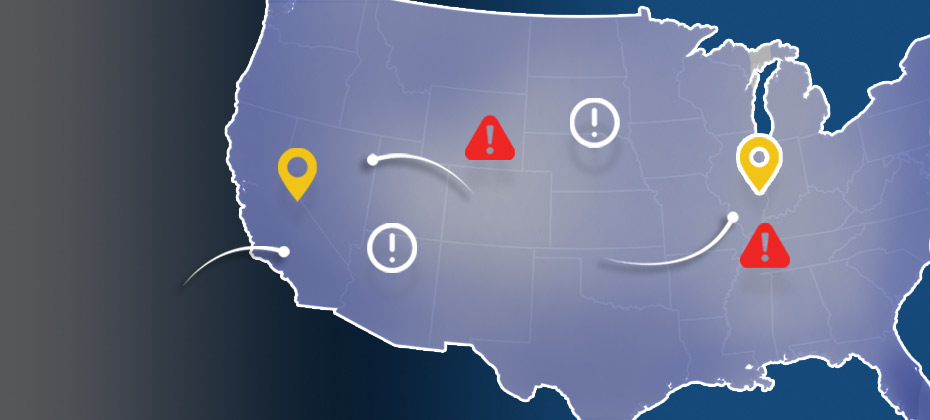
2015 data shows where billing and shipping e-commerce fraud attacks occur in the United States Experian e-commerce fraud attacks and rankings now available Does knowing where fraud takes place matter? With more than 13 million fraud victims in 2015,[1] assessing where fraud occurs is an important layer of verification when performing real-time risk assessments for e-commerce. Experian® analyzed millions of e-commerce transactions from 2015 data to identify fraud-attack rates across the United States for both shipping and billing locations. View the Experian map to see 2015 e-commerce attack rates for all states and download the top 100 ZIP CodeTMrankings. “Fraud follows the path of least resistance. With more shipping and billing options available to create a better customer experience, criminals attempt to exploit any added convenience,” said Adam Fingersh, Experian general manager and senior vice president of Fraud & Identity Solutions. “E-commerce fraud is not confined to larger cities since fraudsters can ship items anywhere. With the switch to chip enabled credit card transactions, and possible growth of card-not-present fraud, our fraud solutions help online businesses monitor their riskiest locations to prevent losses both in dollars and reputation in the near term.” For ease of interpretation, billing states are associated with fraud victims (the address of the purchaser) and shipping states are associated with fraudsters (the address where purchased goods are sent). According to the 2015 e-commerce attack rate data: Florida is the overall riskiest state for billing fraud, followed by Delaware; Washington, D.C.; Oregon and California. Delaware is the overall riskiest state for shipping fraud, followed by Oregon, Florida, California and Nevada. Eudora, Kan., has the overall riskiest billing ZIP Code (66025). The next two riskiest ZIPTM codes are located in Miami, Fla. (33178) and Boston, Mass. (02210). South El Monte, Calif., has the overall riskiest shipping ZIP Code (91733). The next four riskiest shipping ZIP codes are all located in Miami. Overall, five of the top 10 riskiest shipping ZIP codes are located in Miami. Defiance, Ohio, has the least risky shipping ZIP Code (43512). The majority of U.S. states are at or below the average attack rate threshold for both shipping and billing fraud, with only seven states — Florida, Oregon, Delaware, California, New York, Georgia and Nevada — and Puerto Rico ranking higher than average. This indicates that attackers are targeting consumers equally in the higher-risk states while leveraging addresses from both higher- and lower-risk states to ship and receive fraudulent merchandise. Many of the higher-risk states are located near a large port-of-entry city, including Miami; Portland, Ore.; and Washington, D.C., perhaps allowing criminals to move stolen goods more effectively. All three cities are ranked among the riskiest cities for both measures of fraud attacks. Neighboring proximity to higher-risk states does not appear to correlate to any additional risk — Pennsylvania and Rhode Island are ranked as two of the lower-risk states for both shipping and billing fraud. Other lower-risk states include Wyoming, South Dakota and West Virginia. Experian analyzed millions of e-commerce transactions to calculate the e-commerce attack rates using “bad transactions” in relation to the total number of transactions for the 2015 calendar year. View the Experian map to see 2015 e-commerce attack rates for all states and download the top 100 ZIP Code rankings. [1]According to the February 2016 Javelin study 2016 Identity Fraud: Fraud Hits an Inflection Point.

Loyalty fraud and the customer experience Criminals continue to amaze me. Not surprise me, but amaze me with their ingenuity. I previously wrote about fraudsters’ primary targets being those where they easily can convert credentials to cash. Since then, a large U.S. retailer’s rewards program was attacked – bilking money from the business and causing consumers confusion and extra work. This attack was a new spin on loyalty fraud. It is yet another example of the impact of not “thinking like a fraudster” when developing a program and process, which a fraudster can exploit. As it embarks on new projects, every organization should consider how it can be exploited by criminals. Too often, the focus is on the customer experience (CX) alone, and many organizations will tolerate fraud losses to improve the CX. In fact, some organization build fraud losses into their budgets and price products accordingly — effectively passing the cost of fraud onto the consumers. Let’s look into how this type of loyalty fraud works. The criminal obtains your login credentials (either through breach, malware, phishing, brute force, etc.) and uses the existing customer profile to purchase goods using the payment method on file for the account. In this type of attack, the motivation isn’t to receive physical goods; instead, it’s to accumulate rewards points — which can then be used or sold. The points (or any other form of digital currency) are instant — on demand, if you will — and much easier to fence. Once the points are credited to the account, the criminal cashes them out either by selling them online to unsuspecting buyers or by walking into a store, purchasing goods and walking right out after paying with the digital currency. A quick check of some underground forums validates the theory that fraudsters are selling retailer points online for a reduced rate — up to 70 percent off. Please don’t be tempted to buy these! The money you spend will no doubt end up doing harm, one way or another. Now, back to the customer experience. Does having lax controls really represent a good customer experience? Is building fraud losses into the cost of your products fair to your customers? The people whose accounts have been hacked most likely are some of your best customers. They now have to deal with returning merchandise they didn’t purchase, making calls to rectify the situation, having their personally identifiable information further compromised and having to pay for the loss. All in all, not a great customer experience. All businesses have a fiduciary responsibility to protect customer data with which they have been entrusted — even if the consumer is a victim of malware, phishing or password reuse. What are you doing to protect your customers? Simple authentication technologies, while nice for the CX, easily can fail if the criminal has access to the login credentials. And fraud is not a single event. There are patterns and surveillance activities that can help to detect fraud at every phase of your loyalty program — from new account opening to account logins and updates to transactions that involve the purchase of goods or the movement of currency. As fraudsters continue to evolve and look for the least-protected targets, loyalty programs have come to the forefront of the battleground. Take the time to understand your vulnerability and how you can be attacked. Then take the necessary steps to protect your most profitable customers — your loyalty program members. If you want to learn more, join us MRC Vegas 16 for our session “Loyalty Fraud; It’s Brand Protection, Not Just Loss Prevention” and hear our industry experts discuss loyalty fraud, why it’s lucrative, and what organizations can do to protect their brand from this grey-area type of fraud.