Latest Posts

By: Mike Horrocks I am at the Risk Management Association’s annual conference in DC and I feel like I am back to where my banking career began. One of the key topics here is how important the Risk Rating Grade is and what impact that right or wrong Risk Rating Grade can have on the bank. It is amazing to me how a risk rating is often a shot in the dark at some institutions or can even vary on the training of one risk manager to another. For example, you could have a commercial credit with fantastic debt service coverage and have it tied to a terrible piece of collateral and that risk rating grade will range anywhere from prime type credit (cash flow is king and the loan will never default – so why concern ourselves with collateral) to low, subprime (do we really want that kind of collateral dragging us down or in our OREO portfolio?), to anywhere in between. Banks need to define the attributes of a risk rating grade and consistently apply that grade. The failure of doing that will lead to having that poor risk rating grade impact ALLL calculations (with either an over allocation or not enough) and then that will roll into the loan pricing (making you more costly or not enough to match for the risk). The other thing I hear consistently is that we don’t have the right solutions or resources to complete a project like this. Fortunately there is help. A bank should never feel like they should try to do this alone. I recall how it was an all hands on deck when I first started out to make sure we were getting the right loan grading and loan pricing in place at the first super-regional bank I worked at – and that was without all the compliance pressure of today. So take a pause and look at your loan grading approach – is it passing or failing your needs? If it is not passing, take some time to read up on the topic, perhaps find a tutor (or business partner you can trust) and form a study group of your best bankers. This is one grade that needs to be at the top of the class. Looking forward to more from RMA 2014!

The ubiquity of mobile devices provides financial services marketers with an effective way to distribute targeted, customized messages that appeal to a single shopper — a marketing segment of one.

By: Joel Pruis I have just completed the first of two presentations on Model Risk Governance at the RMA Annual Conference. The focus of the presentation was the compliance with the Model Risk Governance guidance at the smaller asset sized financial institutions. The big theme across all of the attendees at the first session was the need for resources to execute on the Model Risk Governance. Such resources are scarce at the smaller asset sized institutions forcing the need and use for external vendors to assist in the development and ongoing validation of any models in use. With that said, the one area that cannot be outsourced is the model risk governance responsibility of the financial institution. While resources are few, we have to look for existing roles within the organization to support the model risk governance such as: - Internal Audit - reviewing process, inputs, consistency - Loan Review - accuracy, consistency, thresholds, etc. - Compliance - Data usage, pricing consistency, etc. Start gathering your governance team at your organization and begin the effort around model risk governance! Discover how an Experian business consultant can help with your Model Risk Governance strategies and processes. Also, if you are interested in gaining deeper insight on regulations affecting financial institutions and how to prepare your business, download Experian’s Compliance as a Differentiator perspective paper.
Experian hosted the Future of Fraud event this week in New York City where Ori Eisen and Frank Abagnale hosted clients and prospects highlighting the need for innovative fraud solutions to stay ahead the consistent threat of online fraud. After, Ori and Frank appeared on Bloomberg TV, interviewed by Trish Regan discussing how retailers can handle fraud prevention. Ori and Frank highlighted how using data is good, especially when combined with analytics as a requirement for businesses working to try and prevent fraud now and in the future. "Data is good. The only way that you deal with a lot of this cyber(crime) is through data analytics. You have to know who I am dealing with. I have to know it is you and authenticate that it is you that wants to make this transaction." Frank Abagnale on BloombergTV Charles Chung recently detailed how utilizing the data for good can protect the customer experience while providing businesses a panoramic view to ensure data security and compliance to mitigate fraud risk. Ultimately, this view helps businesses build greater consumer confidence and create a more positive customer experience which is the first, and most important, prong in the fraud balance. Learn more on how Experian is using big data.

More than 10 years ago I spoke about a trend at the time towards an underutilization of the information being managed by companies. I referred to this trend as “data skepticism.” Companies weren’t investing the time and resources needed to harvest the most valuable asset they had – data. Today the volume and variety of data is only increasing as is the necessity to successfully analyze any relevant information to unlock its significant value. Big data can mean big opportunities for businesses and consumers. Businesses get a deeper understanding of their customers’ attitudes and preferences to make every interaction with them more relevant, secure and profitable. Consumers receive greater value through more personalized services from retailers, banks and other businesses. Recently Experian North American CEO Craig Boundy wrote about that value stating, “Data is Good… Analytics Make it Great.” The good we do with big data today in handling threats posed by fraudsters is the result of a risk-based approach that prevents fraud by combining data and analytics. Within Experian Decision Analytics our data decisioning capabilities unlock that value to ultimately provide better products and services for consumers. The same expertise, accurate and broad-reaching data assets, targeted analytics, knowledge-based authentication, and predictive decisioning policies used by our clients for risk-based decisioning has been used by Experian to become a global leader in fraud and identity solutions. The industrialization of fraud continues to grow with an estimated 10,000 fraud rings in the U.S. alone and more than 2 billion unique records exposed as a result of data breaches in 2014. Experian continues to bring together new fraud platforms to help the industry better manage fraud risk. Our 41st Parameter technology has been able to detect over 90% of all fraud attacks against our clients and reduce their operational costs to fight fraud. Combining data and analytics assets can detect fraud, but more importantly, it can also detect the good customers so legitimate transactions are not blocked. Gartner reported that by 2020, 40% of enterprises will be storing information from security events to analyze and uncover unusual patterns. Big data uncovers remarkable insights to take action for the future of our fraud prevention efforts but also can mitigate the financial losses associated with a breach. In the end we need more data, not less, to keep up with fraudsters. Experian is hosting Future of Fraud and Identity events in New York and San Francisco discussing current fraud trends and how to prevent cyber-attacks aimed at helping the industry. The past skepticism no longer holds true as companies are realizing that data combined with advanced analytics can give them the insight they need to prevent fraud in the future. Learn more on how Experian is conquering the world of big data.
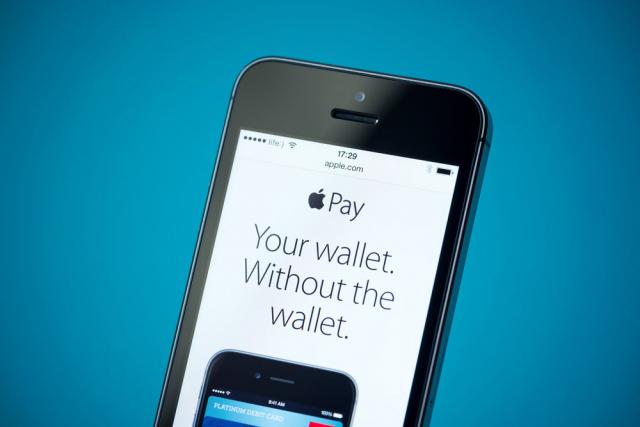
If rumors hold true, Apple Pay will launch in a week. Five of my last six posts had covered Apple’s likely and actual strategy in payments & commerce, and the rich tapestry of control, convenience, user experience, security and applied cryptography that constitutes as the backdrop. What follows is a summation of my views – with a couple of observations from having seen the Apple Pay payment experience up close. About three years ago – I published a similar commentary on Google Wallet that for kicks, you can find here. I hope what follows is a balanced perspective, as I try to cut through some FUD, provide some commentary on the payment experience, and offer up some predictions that are worth the price you pay to read my blog. Source: Bloomua / Shutterstock.com First the criticism. Apple Pay doesn’t go far enough: Fair. But you seem to misunderstand Apple’s intentions here. Apple did not set out to make a mobile wallet. Apple Pay sits within Passbook – which in itself is a wrapper of rewards and loyalty cards issued by third parties. Similarly – Apple Pay is a wrapper of payments cards issued by third parties. Even the branding disappears once you provision your cards – when you are at the point-of-sale and your iPhone6 is in proximity to the reader (or enters the magnetic field created by the reader) – the screen turns on and your default payment card is displayed. One does not need to launch an app or fiddle around with Apple Pay. And for that matter, it’s even more limited than you think. Apple’s choice to leave the Passbook driven Apple Pay experience as threadbare as possible seems an intentional choice to force consumers to interact more with their bank apps vs Passbook for all and any rich interaction. Infact the transaction detail displayed on the back of the payment card you use is limited – but you can launch the bank app to view and do a lot more. Similarly – the bank app can prompt a transaction alert that the consumer can select to view more detail as well. Counter to what has been publicized – Apple can – if they choose to – view transaction detail including consumer info, but only retains anonymized info on their servers. The contrast is apparent with Google – where (during early Google Wallet days) issuers dangled the same anonymized transaction info to appease Google – in return for participation in the wallet. If your tap don’t work – will you blame Apple? Some claim that any transaction failures – such as a non-working reader – will cause consumers to blame Apple. This does not hold water simply because – Apple does not get in between the consumer, his chosen card and the merchant during payment. It provides the framework to trigger and communicate a payment credential – and then quietly gets out of the way. This is where Google stumbled – by wanting to become the perennial fly on the wall. And so if for whatever reason the transaction fails, the consumer sees no Apple branding for them to direct their blame. (I draw a contrast later on below with Samsung and LoopPay) Apple Pay is not secure: Laughable and pure FUD. This article references an UBS note talking how Apple Pay is insecure compared to – a pure cloud based solution such as the yet-to-be-launched MCX. This is due to a total misunderstanding of not just Apple Pay – but the hardware/software platform it sits within (and I am not just talking about the benefits of a TouchID, Network Tokenization, Issuer Cryptogram, Secure Element based approach) including, the full weight of security measures that has been baked in to iOS and the underlying hardware that comes together to offer the best container for payments. And against all that backdrop of applied cryptography, Apple still sought to overlay its payments approach over an existing framework. So that, when it comes to risk – it leans away from the consumer and towards a bank that understands how to manage risk. That’s the biggest disparity between these two approaches – Apple Pay and MCX – that, Apple built a secure wrapper around an existing payments hierarchy and the latter seeks to disrupt that status quo. Let the games begin: Consumers should get ready for an ad blitz from each of the launch partners of Apple Pay over the next few weeks. I expect we will also see these efforts concentrated around pockets of activation – because setting up Apple Pay is the next step to entering your Apple ID during activation. And for that reason – each of those launch partners understand the importance of reminding consumers why their card should be top of mind. There is also a subtle but important difference between top of wallet card (or default card) for payment in Apple Pay and it’s predecessors (Google Wallet for example). Changing your default card was an easy task – and wholly encapsulated – within the Google Wallet app. Where as in Apple Pay – changing your default card – is buried under Settings, and I doubt once you choose your default card – you are more likely to not bother with it. And here’s how quick the payment interaction is within Apple Pay (takes under 3 seconds) :- Bring your phone in to proximity of the reader. Screen turns on. Passbook is triggered and your default card is displayed. You place your finger and authenticate using TouchID. A beep notes the transaction is completed. You can flip the card to view a limited transaction detail. Yes – you could swipe down and choose another card to pay. But unlikely. I remember how LevelUp used very much the same strategy to signup banks – stating that over 90% of it’s customers never change their default card inside LevelUp. This will be a blatant land grab over the next few months – as tens of millions of new iPhones are activated. According to what Apple has told it’s launch partners – they do expect over 95% of activations to add at least one card. What does this mean to banks who won’t be ready in 2014 or haven’t yet signed up? As I said before – there will be a long tail of reduced utility – as we get in to community banks and credit unions. The risk is amplified because Apple Pay is the only way to enable payments in iOS that uses Apple’s secure infrastructure – and using NFC. For those still debating whether it was a shotgun wedding, Apple’s approach had five main highlights that appealed to a Bank – Utilizing an approach that was bank friendly (and to status quo) : NFC Securing the transaction beyond the prerequisites of EMV contactless – via network tokenization & TouchID Apple’s preference to stay entirely as an enabler – facilitating a secure container infrastructure to host bank issued credentials. Compressing the stack: further shortening the payment authorization required of the consumer by removing the need for PIN entry, and not introducing any new parties in to the transaction flow that could have introduced delays, costs or complexity in the roundtrip. Clear description of costs to participate – Free is ambiguous. Free leads to much angst as to what the true cost of participation really is(Remember Google Wallet?). Banks prefer clarity here – even if it means 15bps in credit. As I wrote above, Apple opting to strictly coloring inside the lines – forces the banks to shoulder much of the responsibility in dealing with the ‘before’ and ‘after’ of payment. Most of the bank partners will be updating or activating parts of their mobile app to start interacting with Passbook/Apple Pay. Much of that interaction will use existing hooks in to Passbook – and provide richer transaction detail and context within the app. This is an area of differentiation for the future – because those banks who lack the investment, talent and commitment to build a redeeming mobile services approach will struggle to differentiate on retail footprint alone. And as smarter banks build entirely digital products for an entirely digital audience – the generic approaches will struggle and I expect at some point – that this will drive bank consolidation at the low end. On the other hand – if you are an issuer, the ‘before’ and ‘after’ of payments that you are able to control and the richer story you are able to weave, along with offline incentives – can aid in recapture. The conspicuous and continued absence of Google: So whither Android? Uniformity in payments for Android is as fragmented as the ecosystem itself. Android must now look at Apple for lessons in consistency. For example, how Apple uses the same payment credential that is stored in the Secure Element for both in-person retail transactions as well as in-app payments. It may look trivial – but when you consider that Apple came dangerously close (and justified as well) in its attempt to obtain parity between those two payment scenarios from a rate economics point of view from issuers – Android flailing around without a coherent strategy is inexcusable. I will say this again: Google Wallet requires a reboot. And word from within Google is that a reboot may not imply a singular or even a cohesive approach. Google needs to swallow its pride and look to converge the Android payments and commerce experience across channels similar to iOS. Any delay or inaction risks a growing apathy from merchants who must decide what platform is worth building or focusing for. Risk vs Reward is already skewed in favor of iOS: Even if Apple was not convincing enough in its attempt to ask for Card Present rates for its in-app transactions – it may have managed to shift liability to the issuer similar to 3DS and VBV – that in itself poses an imbalance in favor of iOS. For a retail app in iOS – there is now an incentive to utilize Apple Pay and iOS instead of all the other competing payment providers (Paypal for example, or Google Wallet) because transactional risk shifts to the issuer if my consumer authenticates via TouchID and uses a card stored in Apple Pay. I have now both an incentive to prefer iOS over Android as well as an opportunity to compress my funnel – much of my imperative to collect data during the purchase was an attempt to quantify for fraud risk – and the need for that goes out of the window if the customer chooses Apple Pay. This is huge and the repercussions go beyond Android – in to CNP fraud, CRM and loyalty. Networks, Tokens and new end-points (e.g. LoopPay): The absence of uniformity in Android has provided a window of opportunity for others – regardless of how fragmented these approaches be. Networks shall parlay the success with tokenization in Apple Pay in to Android as well, soon. Prime example being: Loop Pay. If as rumors go – Samsung goes through with baking in Loop Pay in to its flagship S6, and Visa’s investment translates in to Loop using Visa tokenization – Loop may find the ubiquity it is looking for – on both ends. I don’t necessarily see the value accrued to Samsung for launching a risky play here: specifically because of the impact of putting Loop’s circuitry within S6. Any transaction failure in this case – will be attributed to Samsung, not to Loop, or the merchant, or the bank. That’s a risky move – and I hope – a well thought out one. I have some thoughts on how the Visa tokenization approach may solve for some of the challenges that Loop Pay face on merchant EMV terminals – and I will share those later. The return of the comeback: Reliance on networks for tokenization does allay some of the challenges faced by payment wrappers like Loop, Coin etc – but they all focus on the last mile and tokenization does little more for them than kicking the can down the road and delaying the inevitable a little while more. The ones that benefit most are the networks themselves – who now has wide acceptance of their tokenization service – with themselves firmly entrenched in the middle. Even though the EMVCo tokenization standard made no assumptions regarding the role of a Token Service Provider – and in fact Issuers or 3rd parties could each pay the role sufficiently well – networks have left no room for ambiguity here. With their role as a TSP – networks have more to gain from legitimizing more end points than ever before – because these translate to more token traffic and subsequently incremental revenue – transactional and additional managed services costs (OBO – On behalf of service costs incurred by a card issuer or wallet provider). It has never been a better time to be a network. I must say – a whiplash effect for all of us – who called for their demise with the Chase-VisaNet deal. So my predictions for Apple Pay a week before its launch: We will see a substantial take-up and provisioning of cards in to Passbook over the next year. Easy in-app purchases will act as the carrot for consumers. Apple Pay will be a quick affair at the point-of-sale: When I tried it few weeks ago – it took all of 3 seconds. A comparable swipe with a PIN (which is what Apple Pay equates to) took up to 10. A dip with an EMV card took 23 seconds on a good day. I am sure this is not the last time we will be measuring things. The substantial take-up on in-app transactions will drive signups: Consumers will signup because Apple’s array of in-app partners will include the likes of Delta – and any airline that shortens the whole ticket buying experience to a simple TouchID authentication has my money. Apple Pay will cause MCX to fragment: Even though I expect the initial take up to be driven more on the in-app side vs in-store, as more merchants switch to Apple Pay for in-app, consumers will expect a consistency in that approach across those merchants. We will see some high profile desertions – driven partly due to the fact that MCX asks for absolute fealty from its constituents, and in a rapidly changing and converging commerce landscape – that’s just a tall ask. In the near-term, Android will stumble: Question is if Google can reclaim and steady its own strategy. Or will it spin off another costly experiment in chasing commerce and payments. The former will require it to be pragmatic and bring ecosystem capabilities up to par – and that’s a tall ask when you lack the capacity for vertical integration that Apple has. And from the looks of it – Samsung is all over the place at the moment. Again – not confidence inducing. ISIS/SoftCard will get squeezed out of breath: SoftCard and GSMA can’t help but insert themselves in to the Apple Pay narrative by hoping that the existence of a second NFC controller on the iPhone6 validates/favors their SIM based Secure Element approach and indirectly offers Softcard/GSMA constituents a pathway to Apple Pay. If that didn’t make a lick of sense – It’s like saying ‘I’m happy about my neighbor’s Tesla because he plugs it in to my electric socket’. Discover how an Experian business consultant can help you strengthen your credit and risk management strategies and processes: http://ex.pn/DA_GCP This post originally appeared here.

By: Joel Pruis When the OCC put forth the supervisory guidance on model risk governance the big focus in the industry was around the larger financial institutions that had created their own risk models. The overall intent to make sure that the larger financial institutions were properly managing the risk they were assuming through the use of the custom risk models they had developed. While we can’t say that this model risk governance was a significant issue, the guidance provided by the OCC is intended to provide financial institutions with the minimum requirements for model risk governance. Now that the OCC and the Federal Reserve have gone through the model risk governance reviews for the largest financial institutions in the US, their attention has turned to the rest of the group. While you may not have developed your own custom scorecard model, you may be using a generic scorecard model to support your credit decisions either for loan origination and/or portfolio management. As a result of the use of even generic scorecards and models, you do have obligations for model risk governance as stated in the guidance. While you may not be basing any decisions strictly on a score alone, the questions you have to asking yourself are: Does my credit policy or underwriting guidelines reference the use of a score in my decision process? While I may not be doing any type of auto-decision, do I restrict any credit authority based upon a score? Do I adjust any thresholds/underwriting guidelines based upon a score that is returned? For example, do I allow a higher debt to income if the score is above a certain level? How long have you been using a score in your decision processes that may have become a significant influence on how you decision credit? As you can see from the questions above, the guidance covers a significant population of the financial institutions in the US. As a result, some of the basic components that your financial institution must demonstrate it has done (or will do) are: Recent validation of the scorecard against your portfolio performance Demonstration of appropriate policy governing the use of credit risk models per the regulation Independence around the authority and review of the model risk governance and validations Proper support and documentation from your generic scorecard provider per the guidance. If you would like to learn more on this topic, please join me at the upcoming RMA Annual Risk Management Conference where I will be speaking on Model Validation for Community Banks on Monday, Oct. 27, 9:30 a.m. – 10:30 a.m. or 11 a.m. – 12 p.m. Also, if you are interested in gaining deeper insight on regulations affecting financial institutions and how to prepare your business, download Experian’s Compliance as a Differentiator perspective paper.

Card-to-card balance transfers represent a substantial profit opportunity for lenders.

By: Maria Moynihan Mobile devices are everywhere, and landlines and computer desktops are becoming things of the past. A recent American Marketing Association post mentioned that there already are more than 1 billion smartphones and more than 150 million tablets worldwide. As growth in mobile devices continues, so do expectations around convenience, access to mobile-friendly sites and apps, and security. What is your agency doing to get ahead of this trend? Allocating resources toward mobile device access and improved customer service is inevitable, and, arguably, investment and shifts in one of these areas ultimately will affect the other. As ease of information and services improves online or via mobile app, secure logons, identity theft safeguards and authentication measures must all follow suit. Industry best practices in network security call for advancements in: Authenticating users and their devices at the point of entry Detecting new and emerging fraud schemes in processes Developing seamless cross-checks of individuals across channels Click here to see what leading information service providers like Experian are doing to help address fraud across devices. There is a way to confidently authenticate individuals without affecting their overall user experience. Embrace the change.

According to a recent 41st Parameter® study, 85 percent of consumers use online or mobile channels to conduct business.

In a recent webinar, we addressed how both the growing diversity of technology used for online transactions and the many different types of access can make authentication complicated. Technology is ever-changing and is continually reshaping the way we live. This leaves our industry to question how device intelligence factors into both the problem and solution surrounding diverse technologies in the online transaction space. Industry experts Cherian Abraham from the Experian Decision Analytics team and David Britton from 41st Parameter, a part of Experian, weighed in on the discussion. Putting It All Into Context Britton harkened back to a simpler time of authentication practices. In the early days of the web, user names and passwords were the only tools people had to authenticate online identities. Eventually, this led organizations to begin streamlining the process. “They did things like using cookies or placing files onto a computer so that the computer would be “known” to the business,” said Britton. However, those original methods are now struggling to fit into the modern-day authentication puzzle. “The challenge has been that for both privacy reasons and for the advancements of technology we have actually moved to a more privacy-centric environment where those types of things have fallen away in terms of their efficacy. For example, cookies are often easily deleted by simply browsing incognito. So as a result there’s been a counter move approach to how to authenticate online,” said Britton. New Technology – A Quick Fix? Don’t be fooled. Newer technologies cannot necessarily provide an easy alternative and incorporate older authentication methods. Britton referenced how the advent of mobile has actually made recognizing the consumer behind the device, the behavior of the machine and the data that the consumer is presenting even more complex. Additionally, rudimentary methods of authentication don’t actually exist well in the mobile environment. On the other hand, newer technologies and the mobile environment force a more layered approach to authentication methods. “There is a better way and the better way is to look at a variety of other inspirations beyond user names and passwords before vindicating the customer. This is all the more evident when you get to newer channels such as mobile where consumer expectations are so different and you cannot rely on the customer having to answer a long stream of characters and letters such as a user name or a password,” said Abraham. Britton weighed in as well on device intelligence and the layered approach. “Our whole philosophy around this has been that if you can recognize aspects of the device in the form of device intelligence – we’re able to actually leverage that information without crossing the boundaries of good privacy management. Furthermore, we are then able to say we recognize the attributes of the device and can recognize the device as that person is attempting to come back into an environment,” said Britton. He emphasized how being able to help companies understand who might be on the other end of the device has made a world of difference. This increasingly points to how authentication will continue to evolve in a in a multi-device, multi-screen and multi-channel environment. For more information and access to the full webinar – Stay tuned for additional #fraudlifecycle posts.

Auto loan originations reached $153 billion in Q2 2014, which was a 16 percent increase over the same quarter last year. While the largest contribution came from captive auto lenders at $47 billion (a 14 percent increase), credit unions experienced the largest year-over-year increase of 35 percent, with originations reaching $37 billion in the latest quarter. As auto loan originations continue to grow, lenders can stay ahead of the competition by using advanced analytics to target the right customers and increase profitability. Learn how your automotive portfolio compares through the peer-benchmarking capabilities of IntelliViewSM, and view sample reports by industry. Source: Access the latest credit trends with Experian's IntelliView.

Our second annual data breach preparedness study, Is Your Company Ready for a Big Breach?, conducted by the Ponemon Institute, reveals good news and bad news for businesses concerned with data security—and that should be all business. First, the good news: more companies are acting to address data breach risks. The majority (73%) of organizations now have a data breach response plan in place – 12 percent more than in 2012. And nearly half (48%) have boosted investment in security technologies in the past 12 months, aiming to better detect and respond to a data breach. Now, for the not-so-good news: they’re not doing enough, and don’t have confidence in the effectiveness of their current measures. Survey results illustrate that not everyone is taking all the necessary steps to prepare for a data breach: A majority of 78 percent don’t regularly update their data breach response plans to address evolving threats. About two-thirds don’t have trained customer service staff who can respond to customer questions, concerns or complaints if a breach occurs. Only 29 percent of companies involve the CEO in dealing with security risks. Nearly three-quarters don’t have cyber insurance policies. Just 44 percent conducted a technical impact assessment to understand potential fallout from an incident. Less than a third had SIEM systems to facilitate early detection of an incident. 66 percent lack Mobile Device Management (MDM) to protect sensitive information from being pushed to mobile devices. Those who have made provisions don’t necessarily feel more secure because of them: 62 percent don’t feel their organizations are prepared to respond to a data breach. 49 percent didn’t feel they were prepared to respond to the theft of information that would require notification to victims and regulators. Just a quarter were confident they could communicate about a breach and manage customer needs. 40 percent worry about the potential for a third party losing their data. Insider threats concern 56 percent, with 43 percent citing BYOD and cloud services as their top two internal threat concerns. As to post-breach response, we are pleased to see however that companies are well aware of the importance of providing customers involved in a breach with identity theft protection products and access to a call center; in fact, they cited those two as the most important services companies could provide post-breach. Many of the concerns companies expressed over data breach preparedness and response – and in particular, worries over customer communication and regulatory compliance – can be addressed by preparing a response plan and practicing the plan on an ongoing basis. It’s also important to secure external partners such as legal counsel and a public relations firm, and make a selection of a quality identity protection product to offer affected customers ahead of time. When a breach occurs, the complete response team and moving parts are ready to allow for a quick and smooth response. Learn more about our Data Breach solutions

According to a recent Experian Data Quality study, three out of four organizations personalize their marketing messages or are in the process of doing so.

Fraud is not a point-in-time problem and data breaches should not be considered isolated attacks, which break through network defenses to abscond with credentials. In fact, data breaches are just the first stage of a rather complex lifecycle that begins with a vulnerability, advances through several stages of validation and surveillance, and culminates with a fraudulent transaction or monetary theft. Cyber criminals are sophisticated and have a growing arsenal of weapons at their disposal to infect individual and corporate systems and capture account information: phishing, SMSishing and Vishing attacks, malware, and the like are all attempts to thwart security and access-protected information. Criminal tactics have even evolved to include physical-world approaches like infiltrating physical call centers via social engineering attacks aimed at unsuspecting representatives. This, and similar efforts, are all part of the constant quest to identify and exploit weaknesses in order to stage and commit financial crimes. There are some companies that claim malware detection is the silver bullet to preventing fraud. This is simply not the case. The issue is that malware is only one method by which fraudsters may obtain credentials. The seemingly endless supply of pristine identity and account data in the criminal underground means that detecting a user’s system has been compromised is akin to closing the barn door after the hose has bolted. That is, malware can be an indicator that an account has been compromised, but it does not help identify the subsequent usage of the stolen credentials by the criminals, regardless of how the credentials were compromised. Compromised data is first validated by the seller as one of their “value adds” to the criminal underground and typically again by the buyer. Validation usually involves logging into an account to ensure that the credentials work as expected, and allows for a much higher “validated” price point. Once the credentials and/or account have been validated, cyber criminals can turn their attention to surveillance. Remember, by the time one realizes that credential information has been exposed, cyber criminal rings have captured the information they need – such as usernames, passwords, challenge responses and even token or session IDs – and have aded it to their underground data repositories. with traditional online authentication controls, it is nearly impossible to detect the initial fraudulent login that uses ill-gotten credentials. That is why it is critical to operate from the assumption that all account credentials have been compromised when designing an online authentication control scheme.