Tag: fraud

While it’s important to recognize synthetic identities when they knock on your door, it’s just as important to conduct regular portfolio checkups. Every circumstance has unique parameters, but the overarching steps necessary to mitigate fraud from synthetic IDs remain the same: Identify current and near-term exposure using targeted segmentation analysis. Apply technology that alerts you when identity data doesn’t add up. Differentiate fraudulent identities from those simply based on bad data. Review front- and back-end screening procedures until they satisfy best practices. Achieve a “single customer view” for all account holders across access channels — online, mobile, call center and face-to-face. With the right set of analytics and decisioning tools, you can reduce exposure to fraud and losses stemming from synthetic identity attacks at the beginning and across the Customer Life Cycle. Learn more

I recently sat down with Kathleen Peters, SVP and Head of Fraud and Identity, to discuss the state of fraud and identity, the pace of change in the space and her recent inclusion in the Top 100 influencers in Identity by One World Identity. ----------- Traci: Congratulations on being included on the Top 100 influencers list. What a nice honor. Kathleen: Yes, thank you. It is a nice honor and inspiring to be included among some great innovators in the industry. The list includes entrepreneurs to leaders of large organizations like us. It’s a nice mix across all facets of identity. T: Tell me about your role. How long have you been at Experian? K: I lead the team that defines the product strategy for our global fraud and ID portfolio. I’ve been with Experian just over four years, joining soon after we acquired 41st Parameter®. T: What was your first job? K: My first job out of college was with Motorola in Chicago. I was an electrical engineer, working on advanced cellphone technology. T: They were not able to keep up with the market? K: The entire industry was caught by the introduction of the iPhone. All the major cellphone companies were impacted — Nokia, Ericsson, Siemens and others. Talk about disrupting an industry. T: Yeah. These are great examples of how the disrupters have taken out the initial companies. Certainly, Motorola, Nokia, those companies. Even RIM Blackberry, which redefined the digital or cellular space, has all but disappeared. K: Yes, exactly. It was interesting to watch RIM Blackberry when they disrupted Motorola’s pager business. Motorola had a very robust pager line. Even then they had a two-way pager with a keyboard. They just missed the idea of mobile email completely. It’s really, really fascinating to look back now. T: Changing the subject a little, what motivates you to get out of bed in the morning? K: One of my favorite questions. I’m a very purpose-driven person. One of the things I really like about my role and one of the reasons I came to Experian in the first place is that I could see this huge potential within the company to combine offline and online identity information and transaction information to better recognize people and stop fraud. T: What do you see as the biggest threat to organizations today? K: I would have to say the pace of change. As we were just talking about, major industries can be disrupted seemingly overnight. We’re in the midst of a real digital transformation in how we live, how we work, how we share information and even how we share money. The threat to companies is twofold. One is the “friendly fire” threat, like the pace of change, disrupters to the market, new ways of doing things and keeping pace with that innovation. The second threat is that with digitization comes new types of security and fraud risks. Today, organizations need to be ever-vigilant about their security. T: How do you stay ahead of that pace of change? K: Well, my husband and I have lived in Silicon Valley since 1997. Technology and innovation are all around us. We read about it and we hear about it in the news. We engage with our neighbors and other people who we meet socially and within our networks. You can’t help but be immersed in it all the time. It certainly influences the way we go about our lives and how we think and act and engage as a family. We’re all technically curious. We have two kids, and our neighborhood high school, Homestead High, is the same high school Steve Jobs went to. It’s fun that way. T: Definitely. What are some of the most effective ways for businesses to combat the threat of fraud? K: I firmly believe that nowadays it all needs to start with identity. What we’ve found — and confirmed through research in our recent Global Fraud Report, plus conversations I’ve had with clients and analysts — is that if you can better recognize someone, you’ll go a long way to prevent fraud. And it does more than prevent fraud; it provides a better experience for the people you’re engaged with. Because once you recognize an individual, that initiates a trusted relationship between the two of you. Once people feel they’re in a trusted relationship, whether it’s a social relationship or a financial transaction, whatever the relationship is — once you feel trusted, you feel safe, you feel protected. And you’re more likely to want to engage again in the future. I believe the best thing organizations can do is take a multilayered approach to authenticating and identifying people upfront. There are so many ways to do this digitally without disrupting the consumer, and this is the best opportunity for businesses. If we collectively get that right, we’ll stop fraud. T: What are some of the things Experian is focusing on to help businesses stop fraud? K: We’ve focused on our CrossCore® platform. CrossCore is a common access and decisioning capability platform that allows the combining and layering of many different approaches — some active, some passive — to identify a customer in a transaction. You can incorporate things like biometrics and behavioral attributes. You can incorporate digital information about the device you’re engaging with. You can layer in online and offline identity information, like that from our Precise ID® product. CrossCore also enables you to layer in other digital attributes and alternative data such as email address, phone number and the validity of that phone number. CrossCore provides a great opportunity for us to showcase innovation, whether that comes from a third-party partner or even from our own Experian DataLabs. T: How significant do you see machine learning moving forward? K: Machine learning, it has all kinds of names, right? I think of machine learning, artificial intelligence, data robotics, parallel computing — all these things are related to what we used to call big data processing, but that’s not really the trendy term anymore. The point is that there is so much data today. There’s a wealth of data from all different sources, and as a society we’re producing it in exponential volumes. Having more and more and more data is not useful if you can’t derive insights from it. That’s why machine learning, augmented with human intervention or direction, is the best way forward, because there’s so much data out there available in the world now. No matter what problem we’re trying to solve, there’s a wealth of data we can amass, but we need to make sense of it. And the way to make sense of massive amounts of data in a reasonable amount of time is by using some sort of artificial intelligence, or machine learning. We’re going to see it in all kinds of applications. We already are today. So, while I think of machine learning as a generic term, I do think it’s going to be with us for a while to quickly compute and derive meaningful insights from the massive amounts of data all around us. T: Thanks, okay. Last question, and I hope a little fun. How would you describe yourself in one word? K: Curious. T: Ah, that’s a good choice. K: I am always curious. That’s why I love living where I live. It’s why I like working in technology. I’ve always wondered how things work, how we might improve on them, what’s under the hood. Why people make the decisions they do. How does someone come up with this? I’m always curious. T: Well, thank you for the time, and congrats again on being included in the Top 100 influencers in Identity.

It’s clear the digital marketplace is here to stay. Online activities among consumers reflect the increased adoption of digital commerce. In fact, recent findings from our 2018 Global Fraud and Identity Report show the top activity on mobile devices is online shopping, followed closely by personal banking. Consumers trust technology and, by proxy, the businesses that help enable it. It’s critical for organizations to continue to build trust online without disrupting the consumer experience. It’s the goal — and the responsibility — of businesses. Learn more

Experian® is honored to be an MRC Technology Award nominee. But we can’t win the MRC People’s Choice Award without your help! The annual MRC Technology Awards recognize the most elite solution providers making significant contributions in the fraud, payments and risk industries. CrossCore® is the first smart, open, plug-and-play platform for fraud and identity services. We know, and our clients agree, that it delivers a better way to modify strategies quickly, catch fraud faster, improve compliance and enhance the customer experience. Need further convincing? Here are the top 3 reasons you should vote for CrossCore. Reason 1: common access Manage your entire fraud and identity portfolio. Start immediately by turning on Experian services through a single integration. Connect to services quickly with a common, flexible API. Reason 2: open approach Control the data being used in decisions. CrossCore supports a best-in-class approach to managing a portfolio of services that work together in any combination — including Experian solutions, third-party services and client systems — delivering the level of confidence needed for each transaction. Reason 3: workflow decisioning Act quickly and adapt to new risks with built-in strategy design and workflow capabilities. You can precisely tailor strategies based on transaction type or risk threshold. Make changes dynamically, with no downtime. We hope you’ll vote for CrossCore as a better way to manage fraud prevention and identity services.

Global Fraud and Identity Report 2018 Customer recognition. Convenience. Trust. Fraud risk. We obtained input from more than 5,500 consumers and 500 businesses worldwide on these priorities for our Global Fraud and Identity Report 2018. Top takeaways include: Your customers expect you to protect them. Are you meeting this need? Spot fraud by recognizing your customers. Can you identify yours? While perfect fraud prevention shouldn't undermine customer happiness, we can't forget that fraud victims aren’t happy customers. Businesses recognize the importance of trust - and the need for technology to enable it. Most businesses tend to demonstrate suspicion when it comes to preventing fraud, following a route of detection rather than permission or trust. This leads to lost sales and damages that customer’s lifetime value. There’s a better approach. Read the full report>

The multitude of modern fraud strategies available today necessitates applying an appropriate level of confidence to increase the likelihood of catching fraudsters without disrupting legitimate customers’ experiences. This approach is known as “rightsizing” your fraud solution. Here’s how fraud detection rates can be improved while reducing the number of false positives and disruption of legitimate customers: A right-size approach means tackling your fraud problem with a highly tailored solution that enables your business rather than crippling it. Next week, we’ll discuss this forward-looking approach to fighting fraud, or you can jump ahead and read our latest tip sheet. Tip sheet>

Traditional verification and validation parameters alone are not enough to stop identity fraud. Fortunately, there are many emerging trends and best practices for modern fraud and identity strategies: Applying right-sized fraud and identity proofing solutions to reduce user friction and manage fraud risk appropriately. Maintaining a universal user view by employing diverse breadth and depth of data assets and applied analytics. Expanding the user view through a blended ecosystem by collaborating with vendors, peer agencies, and partners in identity and fraud management. The future of identity proofing is more than just verifying individual identities. Check out our tip sheet linked below for more strategies. Modernize your fraud and identity strategies>

Sophisticated criminals work hard to create convincing, verifiable personas they can use to commit fraud. Here are the 3 main ways fraudsters manufacture synthetic IDs: Credit applications and inquiries that build a synthetic credit profile over time. Exploitation of authorized user processes to take over or piggyback on legitimate profiles. Data furnishing schemes to falsify regular credit reporting agency updates. Fraudsters are highly motivated to innovate their approaches rapidly. You need to implement a solution that addresses the continuing rise of synthetic IDs from multiple engagement points. Learn more

Juniper Research recently recognized Experian as a Fraud Detection and Prevention Market Leader in its Online Payment Fraud Whitepaper. Juniper also shared important market insights in the report. The transactional value of card-not-present fraud is estimated to reach $19.3 billion in 2022. Online payment fraud is anticipated to grow 13.7% annually from 2017 to 2022. Digital banking fraud should reach $7.9 billion by 2022. $50.9 billion is expected to be spent on fraud detection and prevention software between 2017 and 2022. Fraud’s not going away anytime soon. Protecting your organization and customers is the new cost of doing business. Don’t wait until 2022 to start protecting yourself. Read the report>

The data to create synthetic identities is available. And the marketplace to exchange and monetize that data is expanding rapidly. The fact that hundreds of millions of names, addresses, dates of birth, and Social Security numbers (SSNs) have been breached in the last year alone, provides an easy path for criminals to surgically target new combinations of data. Armed with an understanding of the actual associations of these personally identifiable information (PII) elements, fraudsters can better navigate the path to perpetrate identity theft, identity manipulation, or synthetic identity fraud schemes on a grand scale. Using information such as birth dates and addresses in combination with Social Security numbers, criminals can target new combinations of data to yield better results with lower risk of detection. Some examples of this would be: identity theft, existing account takeovers, or the deconstruction and reconstruction of those PII elements to better create effective synthetic identities. Experian has continued to evolve and innovate against fraud risks and attacks with an understanding of attack rates, vectors, and the shifting landscape in data availability and security. In doing so, we’ve historically operated under the assumption that all PII is already compromised in some way or is easily done so. Because of this, we employ a layered approach, providing a more holistic view of an identity and the devices that are used over time by that identity. Relying solely on PII to validate and verify an identity is simply unwise and ineffective in this era of data compromise. We strive to continuously cultivate the broadest and most in-depth set of traditional, innovative and alternative data assets available. To do this, we must enable the integration of diverse identity attributes and intelligence to balance risk, while maintaining a positive customer experience. It’s been quite some time since the use of basic PII verification alone has been predictive of identity risk or confidence. Instead, validation and verification is founded in the ongoing definition and association of identities, the devices commonly used by those individuals, and the historical trends in their behavior. Download our newest White Paper, Synthetic Identities: Getting real with customers, for an in-depth Experian perspective on this increasingly significant fraud risk.

Despite rising concerns about identity theft, most Americans aren’t taking basic steps to make it harder for their information to be stolen, according to a survey Experian conducted in August 2017: Nearly 3 in 4 consumers said they’re very or somewhat concerned their email, financial accounts or social media information could be hacked. This is up from 69% in a similar survey Experian conducted in 2015. Nearly 80% of survey respondents are concerned about using a public Wi-Fi network. Yet, barely half said they take the precaution of using a password-protected Wi-Fi network when using mobile devices. 59% of respondents are annoyed by safety precautions needed to use technology — up 12% from 2015. When your customer’s identity is stolen, it can negatively impact the consumer and your business. Leverage the tools and resources that can help you protect both. Protect your customers and your business>

Synthetic identity fraud is on the rise across financial services, ecommerce, public sector, health and utilities markets. The long-term impact of synthetic identity remains to be seen and will hinge largely upon forthcoming efforts across the identity ecosystem made up of service providers, institutions and agencies, data aggregators and consumers themselves. Making measurement more challenging is the fact that much of the assumed and confirmed losses are associated with credit risk and charge offs, and lack of common and consistent definitions and confirmation criteria. Here are some estimates on the scope of the problem: Losses due to synthetic identity fraud are projected to reach more than $800 million in 2017.* Average loss per account is more than $10,000.* U.S. synthetic credit card fraud is estimated to reach $1.257 billion in 2020.* As with most fraud, there is no miracle cure. But there are best practices, and topping that list is addressing both front- and back-end controls within your organization. Synthetic identity fraud webinar> *Aite Research Group

Earlier this week, Javelin Strategy & Research announced its inaugural edition of the 2017 Identity Proofing Platform Awards. We were honored to see CrossCore as the leader – taking the award for the best overall identity proofing platform. According to the report, “Experian’s identity proofing platform is a strong performer in every category of Javelin’s FIT model. It is functional. It is innovative. And, most important, it is tailored toward the advisory’s expectations. The comprehensive nature of CrossCore makes it the market-leading solution for identity proofing.” It’s harder than ever to confidently identify your customers in today’s digital economy. You have lots of vendor solutions to choose from in the identity proofing space. And, now Javelin has made it much easier for you to select the partner that is right for your needs. Javelin’s newly minted Identity Proofing Platform Scorecard assesses current capabilities in the market to help you make that decision. And they have done a lot of the heavy lifting, looking across 23 vendors and scoring them based on three categories of their FIT model – functional, innovative, and tailored. Protecting customers is a priority for you – and for us. Here at Experian, we have a range of capabilities to help businesses manage identity proofing, and our CrossCore platform brings them all together. We launched CrossCore last year, with the goal of making the industry’s fraud and identity solutions work better for everyone. CrossCore delivers a future-proof way to modify strategies quickly, catch fraud faster, improve compliance and enhance the customer experience. We’re proud of the work we’ve done so far, integrating our products as well as adding more than 10 partners to the program. We’re pleased to see so many of our partners included in Javelin’s report. We’re working closely with our clients to pull in more partner capabilities, and further enhance our own platform to create a layered approach that supports a risk-based, adaptable strategy. As highlighted in the Javelin report, a reliance on traditional identity verification approaches are no longer sufficient or appropriate for digital channels. With CrossCore, our clients can choose the capabilities they want, when they want them, to dial in the right confidence level for each and every transaction. This is because CrossCore supports a layered approach to managing risk, allowing companies to connect multiple disparate services through a common access point. We are committed to making it easier for you to protect consumers against fraud. CrossCore is helping us all do just that.
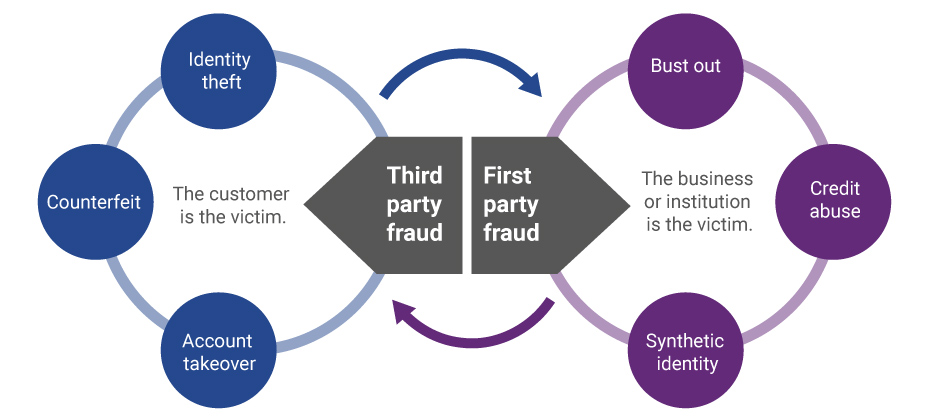
Evolution of first-party fraud to third Third-party and first-party schemes are now interchangeable, and traditional fraud detection practices are less effective in fighting these evolving fraud types. Fighting this shifting problem is a challenge, but it isn’t impossible. To start, incorporate new and more robust data into your identity verification program and provide consistent fraud classification and tagging. Learn more>
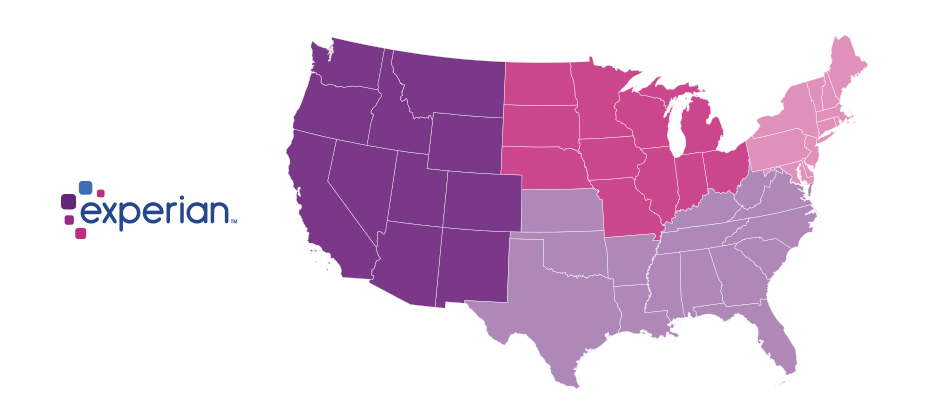
We recently analyzed millions of online transactions from the first half of 2017 to identify fraud attack rates. Here are the top 3 riskiest states for e-commerce billing and shipping fraud for H1 2017: Riskiest states for billing fraud Oregon Delaware Washington, D.C. Riskiest states for shipping fraud Oregon Delaware Florida Fraudsters are extremely creative, motivated and often connected. Protect all points of contact with your customers to prevent this growing type of fraud. Is your state in the top 10?