Tag: fraud

Cybersecurity cannot be successful if siloed. The entire organization must be part of the effort. Take these steps to ensure a more engaged relationship between cybersecurity teams, C-suite executives and other departments: Make the company’s chief information officer accountable directly to the chief executive officer and/or the board. Train employees at every level to spot security risks and to understand their role in protecting the entire organization from cyberattacks. Put cybersecurity on the agenda for every board and executive-level meeting, and incorporate it into quarterly state-of-the-company, all-hands meetings. With cybersecurity threats evolving and escalating daily, companies need to make engagement a priority that starts at the top and continues through every level of the organization. Increasing engagement in cybersecurity >
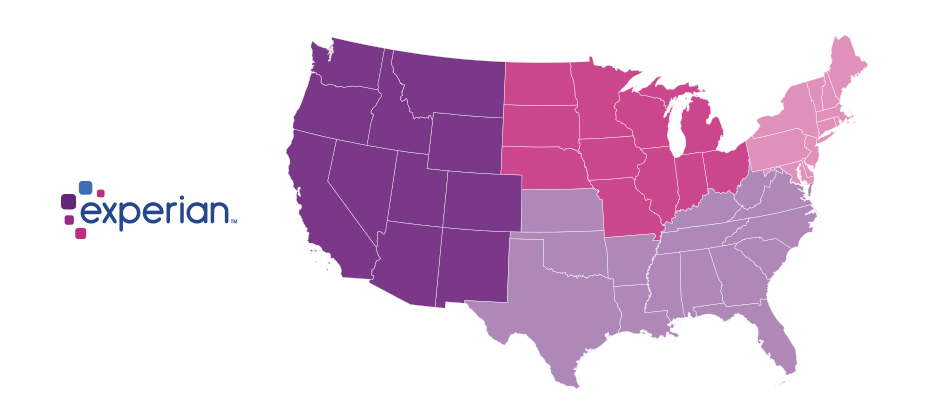
Since the advent of the internet, our lives have changed drastically for the better. We can perform many of life’s daily activities from the comfort of our own home. According to Aite, in 2016 alone 36 million Americans made some form of mobile payment — paying a bill, purchasing something online, paying for fast food or making a mobile wallet purchase at a retailer. Simply put, the internet has made our lives easier. But with the good also comes the bad. While most consumers have moved to the digital world, so have fraudsters. With minimal risk and high reward at stake, e-commerce fraud attacks have increased dramatically over the last few years, with no signs of slowing down. We recently analyzed millions of transactions from the first half of 2017 to identify fraud attack rates based on billing and shipping addresses and broke down the findings into various geographic trends. Fraud attack rates represent the attempted fraudulent e-commerce transactions against the population of overall e-commerce orders. Consumers living out West and in the South have experienced more than their fair share of fraud. During the first half of 2017, the West and the South were the top two regions for both billing and shipping attacks. While both regions were at the top during the same time last year, the attacks themselves have increased substantially. Given the proximity to seaports and major international airports, this is somewhat unsurprising — particularly for shipping fraud — as many fraudsters will leverage reshippers to transport goods soon after delivery. .dataTb{margin:20px auto;width:100%}.dataTb:after{clear:both}.dataTb table{}.dataTb td,.dataTb th{border:1px solid #ddd;padding:.8em}.dataTb th{background:#F4F4F4}.tbL{float:left;width:49%}.tbR{float:right;width:49%;margin:0 0 0 2%} Shipping: Riskiest Regions Region Attack rate West 38.1 South 32.1 Northeast 27.0 North Central 20.7 Billing: Riskiest Regions Region Attack rate West 37.2 South 32.9 Northeast 27.3 North Central 24.0 At the state level, the top three shipping fraud states remained the same as 2016 — Delaware, Oregon and Florida — but the order changed. Oregon was the most targeted, with a fraud rate of 135.2 basis points, more than triple its rate at in the end of 2016. Though no longer in the top spot, Delaware saw alarming spikes as well, with shipping attack rates nearly triple last year’s rate at 128.6 basis points and billing attacks at 79.6 basis points. .dataTb{margin:20px auto;width:100%}.dataTb:after{clear:both}.dataTb table{}.dataTb td,.dataTb th{border:1px solid #ddd;padding:.8em}.dataTb th{background:#F4F4F4}.tbL{float:left;width:49%}.tbR{float:right;width:49%;margin:0 0 0 2%} Shipping: Riskiest States State Attack rate Oregon 135.2 Delaware 128.2 Florida 57.4 New York 45.0 Nevada 36.9 California 36.9 Georgia 33.5 Washington, D.C 30.8 Texas 29.6 Illinois 29.4 Billing: Riskiest States Region Attack rate Oregon 87.5 Delaware 79.6 Washington, D.C. 63.0 Florida 47.4 Nevada 38.8 California 36.9 Arkansas 36.6 New York 35.5 Vermont 34.2 Georgia 33.4 Diving a bit deeper, ZIPTM codes in Miami, Fla., make up a significant portion of the top 10 ZIP CodeTM lists for shipping and billing attacks — in fact, many of the same ZIP codes appear on both lists. The other ZIP Code that appears on both lists is South El Monte, Calif., which has a high percentage of industrial properties — common targets for fraudsters to ship packages, then reship overseas. You can download the top 100 riskiest Zip Codes in the U.S. for H1 2017. .dataTb{margin:20px auto;width:100%}.dataTb:after{clear:both}.dataTb table{}.dataTb td,.dataTb th{border:1px solid #ddd;padding:.8em}.dataTb th{background:#F4F4F4}.tbL{float:left;width:49%}.tbR{float:right;width:49%;margin:0 0 0 2%} Shipping: Top 10 riskiest ZIP™ Codes ZIP Code Attack rate 33122 [Miami, Fla.] 2409.4 91733 [South El Monte, Calif.] 1655.5 33198 [Miami, Fla.] 1295.2 33166 [Miami, Fla.] 1266.0 33195 [Miami, Fla.] 1037.3 33192 [Miami, Fla.] 893.9 97251 [Portland, Ore.] 890.6 07064 [Port Reading, NJ] 808.9 89423 [Minden, Nev.] 685.5 77072 [Houston, Tex.] 629.3 Billing: Top 10 riskiest ZIP™ Codes ZIP Code Attack rate 77060 [Houston, Tex.] 1337.6 33198 [Miami, Fla.] 1215.6 33122 [Miami, Fla.] 1106.2 33166 [Miami, Fla.] 1037.4 91733 [South El Monte, Calif.] 780.1 33195 [Miami, Fla.] 713.7 97252 [Portland, Ore.] 670.8 33191 [Miami, Fla.] 598.8 33708 [St. Petersburg, Fla.] 563.6 33792 [Miami, Fla.] 493.0 As e-commerce fraud continues to grow, businesses need to be proactive to keep themselves and their customers safe. That means incorporating multiple, layered fraud prevention strategies that work together seamlessly — for example, understanding details about users and their devices, knowing how users interact with the business and evaluating previous transaction history. This level of insight can help businesses distinguish real customers from nefarious ones without impacting the customer experience. While businesses are ultimately responsible for the safety of customers and their data, the onus doesn’t rest solely with them. Consumers should also be vigilant when it comes to protecting their digital identities and payment information. That means creating strong, unique passwords; actively monitoring online accounts; and using two-factor authentication to secure account access. At the end of the day, e-commerce fraud is a challenge that businesses and consumers will experience for the foreseeable future. But rising attack rates don’t have to spell doom and gloom for the industry. E-commerce growth is still extremely strong, as consumers interact through multiple channels (in-store, mobile and web) and expect a personalized experience. Establishing trust and verifying digital identities are key to meeting these latest expectations, which provide new opportunities for businesses and consumers to interact seamlessly and transact securely. With multiple safeguards in place, businesses have a variety of options to protect their customers and their brand reputation. Experian is a nonexclusive full-service provider licensee of the United States Postal Service®. The following trademarks are owned by the United States Postal Service®: ZIP and ZIP Code. The price for Experian’s services is not established, controlled or approved by the United States Postal Service.

We live in a digital world where online identities are ubiquitous. But with the internet’s inherent anonymity, how do you know you’re interacting with a legitimate individual rather than an imposter? Too often we hear stories about consumers who see unauthorized purchases on their credit cards, enable access to their devices based on an imposter claiming to be a security vendor or send money to someone they met online only to learn they’ve been “catfished” by a fraudster. These are growing problems, as more consumers transition to digital services and look to businesses to protect them, enable seamless trusted interactions and maintain their privacy. I recently chatted with MarketWatch about how consumers can protect themselves and their privacy when using online dating apps, as well as what businesses are doing to safeguard digital data. As part of the discussion, I mentioned that a simple, standard verification process companies of all sizes can leverage is vital to our rapidly evolving digital economy. Today, companies have their own policies, processes and definitions of identity verification, depending on the services they offer. This ranges from secure access requiring strong identity proofing, document verification, multifactor authentication and biometric enrollment to new social profiles that do little more than validate receipt of an email to establish an online account. To satisfy those diverse risk-based needs, more organizations are turning to federated identity verification options. A federated system allows businesses to leverage trusted, reputable, third-party sources to validate identity by cross-referencing the information they’ve received from a consumer against these sources to determine whether to establish an account or allow a transaction. While some organizations have attempted to develop similar identity verification capabilities, many lack a trusted identity source. For example, there are solutions that leverage data from social media accounts or provide multifactor fraud and authentication options, but they often become easily compromised because of the absence of verifiable data. A trusted solution aggregates data across multiple providers that have undergone thorough security and data quality vetting to ensure the identity data is accurately submitted in accordance with business and compliance requirements. In fact, there are only a handful of trusted identity sources with this level of due diligence and oversight. At Experian, we assess verification requests against an aggregate of hundreds of millions of records that include identity relationships, profile risk attributes, historical usage records and demographic data assets. With decades of knowledge about identity management and fraud prevention, we help companies of all sizes balance risk mitigation and maintain compliance requirements — all while ensuring consumer data privacy. Trust takes years to build and mere seconds to lose, and the industry has made undeniable progress in security. But there is much left to do. Consumers are increasingly involved in the protection and use of their data. However, they often don’t realize downloading a hot new app and entering personal details or linking to their friends exposes them to unnecessary risk. It’s important for businesses to be clear about their identity verification processes so consumers can make educated decisions before electing to provide invaluable identity data. The most effective fraud prevention and identity strategy is one that quickly establishes trust without inconveniencing the consumer. By staying up to date on verification methods, businesses can ensure customers have a smooth, personalized and engaging online experience.

A combination of mass identity data compromise and the increasing abilities of organized fraud rings has created a synthetic identity epidemic that is impacting all markets. Here are the three ways that synthetic identities are generally created: Credit applications and inquiries that result in synthetic credit profile creation or build. Exploitation of the authorized user process designed to take over or piggyback on legitimate credit profiles. Data furnishing schemes that falsify regular credit reporting agency updates. When it comes to fighting synthetic fraud, we all need to be a part of the solution – or we are just a part of the problem. Mitigate synthetic identity fraud >

Mitigating synthetic identities Synthetic identity fraud is an epidemic that does more than negatively affect portfolio performance. It can hurt your reputation as a trusted organization. Here is our suggested 4-pronged approach that will help you mitigate this type of fraud: Identify how much you could lose or are losing today to synthetic fraud. Review and analyze your identity screening operational processes and procedures. Incorporate data, analytics and cutting-edge tools to enable fraud detection through consumer authentication. Analyze your portfolio data quality as reported to credit reporting agencies. Reduce synthetic identity fraud losses through a multi-layer methodology design that combats both the rise in synthetic identity creation and use in fraud schemes. Mitigating synthetic identity fraud>

The creation of synthetic identities (synthetic id) relies upon an ecosystem of institutions, data aggregators, credit reporting agencies and consumers. All of which are exploited by an online and mobile-driven market, along with an increase in data breaches and dark web sharing. It’s a real and growing problem that’s impacting all markets. With significant focus on new customer acquisition and particular attention being paid to underbanked, emerging, and new-to-country consumers, this poses a large threat to your onboarding and customer management policies, in addition to overall profitability. Synthetic identity fraud is an epidemic that does more than negatively affect portfolio performance. It can hurt your reputation as a trusted organization and expose institutions, like yours, as paths of lesser resistance for fraudsters to use in the creation and farming of synthetic identities. Here is a suggested four-pronged approach to mitigate this type of fraud: The first step is knowing your risk exposure to synthetic identity fraud. Identify how much you could lose or are losing today using a targeted segmentation analysis to examine portfolios or customer populations. Next, review your front- and back-end identity screening operational processes and procedures and analyze that information to ensure you have industry best practices, procedures and verification tools deployed. Then incorporate data, analytics and some of the industry’s cutting edge tools. This enables you to perform targeted consumer authentication and identify opportunities to better capture the majority of fraud and operational waste. Lastly, ensure your organization is part of the solution – not the problem. Analyze your portfolio data quality as reported to credit reporting agencies and then minimize your exposure to negative compliance audit results and reputational risk. Our fraud and identity management consultants can help you reduce synthetic identity fraud losses through a multilayer methodology design that combats the rise in synthetic identity creation and use in fraud schemes.

Experian’s ID Fraud Tracker, a quarterly analysis of fraud rates across consumer financial products, found that British families who are struggling financially — about 4 million people — are increasingly becoming prime targets of financial fraud. The research performed on data from 2014 to 2016 in the United Kingdom also revealed: There has been a 203% increase in the total number of fraudulent credit applications over the past two years. Current account, credit card and loan fraud were the most common types of credit products fraudsters applied for in other people’s names, making up 94% of the total. 35% of all third-party fraud came from households with high salaries and large disposable incomes. Fraud’s increasing around the world. We all have a responsibility to be vigilant and take measures to protect our business and customers, online and offline. Protect your customers >

The final day of Vision 2017 brought a seasoned group of speakers to discuss a wide range of topics. In just a few short hours, attendees dove into a first look at Gen Z and their use of credit, ecommerce fraud, the latest in retail, the state of small business and leadership. Move over Millennials – Gen Z is coming of credit age Experian Analytics leaders Kelley Motley and Natasha Madan gave audience members an exclusive look at how the first wave of Gen Z is handling and managing credit. Granted most of this generation is still under the age of 18, so the analysis focused on those between the ages of 18 to 20. Yes, Millennials are still the dominant generation in the credit world today, standing strong at 61 million individuals. But it’s important to note Gen Z is sized at 86 million, so as they age, they’ll be the largest generation yet. A few stats to note about those Gen Z individuals managing credit today: Their average debt is $12,679, compared to younger Millennials (21 to 27) who have $65,473 in debt and older Millennials (28 to 34) who sport $121,460. Given their young age, most of Gen Z is considered thin-file (less than 5 tradelines) Average Gen Z income is $33,000, and average debt-to-income is low at 5.7%. New bankcard balances are averaging around $1,574. As they age, acquire mortgages and vehicles, their debt and tradelines will grow. In the meantime, the speakers provided audience members a few tips. Message with authenticity. Think long-term with this group. Maintain their technological expectations. Build trust and provide financial education. State of business credit and more on the economy Moody’s Cris deRitis reiterated the U.S. economy is looking good. He quoted unemployment at 4.5%, stating “full employment is here.” Since the recession, he said we’ve added 15 million jobs, noting we lost 8 million during the recession. The great news is that the U.S. continues to add about 200,000 jobs a month, and that job growth is broad-based. Small business loans are up 10% year-to-date vs. last year. While there has been a tremendous amount of buzz around small business, he adds that most job creation has come from mid0size business (50 to 499 employees). The case for layered fraud systems Experian speaker John Sarreal shared a case study that revealed by layering on fraud products and orchestrating collaboration, a business can go from a string 75% fraud detection rate to almost 90%. Additionally, he commented that Experian is working to leverage dark web data to mine for breached identity data. More connections for financial services companies to make with mobile and social Facebook speaker Olivia Basu reinforced the need for all companies to be thinking about mobile. “Mobile is not about to happen,” she said. “Mobile is now. Mobile is everything. You look at the first half of 2017 and we’re seeing 40% of all purchases are happening on mobile devices.” Her challenge to financial services companies is to make marketing personal again, and of course leverage the right channels. Experian Sr. Director of Credit Marketing Scott Gordon commented on Experian’s ability to reach consumers accurately – whether that be through direct or digital delivery channels. A great deal of focus has been around person-based marketing vs. leveraging the cookie. -- The Vision conference was capped off with a keynote speech from legendary quarterback and Super Bowl MVP Tom Brady. He chatted about the details of this past season, and specifically the comeback Super Bowl win in February 2017. He additionally talked about leadership and what that means to creating a winning team and organization. -- Multiple keynote speeches, 65 breakout sessions, and hours of networking designed to help all attendees ready themselves for growing profits and customers, step up to digital, regulatory and fraud challenges, and capture the latest data insights. Learn more about Experian’s annual Vision conference.

So many insights and learnings to report after the first full day of 2017 Vision sessions. From the musings shared by tech engineer and pioneer Steve Wozniak, to a panel of technology thought leaders, to countless breakout sessions on a wide array of business topics … here’s a look at our top 10 from the day. A mortgage process for the digital age. At last. In his opening remarks, Experian President of Credit Services Alex Lintner asked the audience to imagine a world when applying for a mortgage simply required a few clicks or swipes. Instead of being sent home to collect a hundred pieces of paper to verify employment, income and assets, a consumer could click on a link and provide a few credentials to verify everything digitally. Finally, lenders can make this a reality, and soon it will be the only way consumers expect to go through the mortgage process. The global and U.S. economies are stable. In fact, they are strong. As Experian Vice President of Analytics Michele Raneri notes, “the fundamentals and technicals look really solid across the countries.” While many were worried a year ago that Brexit would turn the economy upside down, it appears everything is good. Consumer confidence is high. The Dow Jones Index is high. The U.S. unemployment rate is at 4.7%. Home prices are up year-over-year. While there has been a great deal of change in the world – politically and beyond – the economy is holding strong. The rise of the micropreneur. This term is not officially in the dictionary … but it will be. What is it? A micropreneur is a business with 0 to 4 employees bringing in no more than $200k in annual revenue. But the real story is that numbers show microbusiness are improving on many fronts when it comes to contribution to the economy and overall performance compared to other small businesses. Keep an eye on these budding business people. Fraud is running fierce. Synthetic identity losses are estimated in the hundreds of millions annually, with 50% year-over year growth. Criminals are now trying to use credit cleaners to get tradelines removed from used Synthetic IDs. Oh, and it is essential for businesses to ready themselves for “Dark Web” threats. Experts advise to harden your defenses (and play offense) to keep pace with the criminal underground. As soon as you think you’ve protected everything, the criminals will find a gap. The cloud is cool and so are APIs. A panel of thought leaders took to the main stage to discuss the latest trends in tech. Experian Global CIO Barry Libenson said, “The cloud has changed the way we deliver services to our customers and clients, making it seamless and elastic.” Combine that with API, and the goal is to ultimately make all Experian data available to its customers. Experian President of Decision Analytics Steve Platt added, “We are enabling you to tap into what you need, when you need it.” No need to “rip and replace” all your tech. Expect more regulation – and less. A panel of regulatory experts addressed the fast-changing regulatory environment. With the new Trump administration settling in, and calls for change to Dodd-Frank and the Consumer Financial Protection Bureau (CFPB), it’s too soon to tell what will unfold in 2017. CFPB Director Richard Cordray may be making a run for governor of Ohio, so he could be transitioning out sooner than the scheduled close of his July 2018 term. The auto market continues to cruise. Experian’s auto expert, Malinda Zabritski, revealed the latest and greatest stats pertaining to the auto market. A few numbers to blow your mind … U.S. passenger cars and light trucks surpassed 17 million units for the second consecutive year Most new vehicle buyers in the U.S. are 45 years of age or older Crossover and sport utility vehicles remain popular, accounting for 40% of the market in 2016 – this is also driving up finance payments since these vehicles are more expensive. There are signs the auto market is beginning to soften, but interest rates are still low, and leasing is hot. Defining alternative data. As more in the industry discuss the need for alternative data to decision, it often gets labeled as something radical. But in reality, alternative data should be simple. Experian Sr. Director of Government Affairs Liz Oesterle defined it as “getting more financial data in the system that is predicted, validated and can be disputed.” #DeathtoPasswords – could it be a reality? It’s no secret we live in a digital world where we are increasingly relying on apps and websites to manage our lives, but let’s throw out some numbers to quantify the shift. In 2013, the average U.S. consumer had 26 online accounts. By 2015, that number increased to 118 online accounts. By 2020, the average person will have 207 online accounts. When you think about this number, and the passwords associated with these accounts, it is clear a change needs to be made to managing our lives online. Experian Vice President David Britton addressed his session, introducing the concept of creating an “ultimate consumer identity profile,” where multi-source data will be brought together to identify someone. It’s coming, and all of us managing dozens of passwords can’t wait. “The Woz.” I guess you needed to be there, but let’s just say he was honest, opinionated and notes that while he loves tech, he loves it even more when it enables us to live in the “human world.” Too much wonderful content to share, but more to come tomorrow …

During our recent webinar, Detect and Prevent: The current state of e-commerce fraud, Julie Conroy, Aite Group research director, shared 5 key trends relating to online fraud: Rising account takeover fraud. Targeting of loyalty points. Growing global transactions. Frustrating false declines. Increasingly mobile consumers. Fraud is increasing. Be prepared. Protect your business and customers with a multilayered approach to fraud prevention. For more trends and predictions, watch the webinar recording.

With the recent switch to EMV and more than 4.2 billion records exposed by data breaches last year*, attackers are migrating their fraud attempts to the card-not-present channel. Our recent analysis found the following states to be the riskiest for e-commerce fraud in 2016. Delaware Oregon Florida New York Nevada Attackers are extremely creative, motivated, and often connected. Prevent e-commerce fraud by protecting all of your customer contact points. Fraud Heat Map>

Turns out, Americans still don’t know much about CyberSecurity. That’s according to new research from the Pew Data Center, which conducted a cybersecurity knowledge quiz. The 13 question quiz was designed to test American’s knowledge on a number of cybersecurity issues and terms. A majority of online adults can identify a strong password and recognize the dangers of using public Wi-Fi. However, many struggle with more technical cybersecurity concepts, such as how to identify true two-factor authentication or determine if a webpage they are using is encrypted. As we in the industry know, cybersecurity is a complicated and diverse subject, but given the pervasiveness of news around cybersecurity, I was still a little surprised by the lack of knowledge. The typical (median) respondent answered only five of the 13 questions correctly (with a mean of 5.5 correct answers). 20% answered more than eight questions accurately, and just 1% received a “perfect score” by correctly answering all 13 questions. The study showed that public knowledge of cybersecurity is low on some relatively technical issues, like identifying the correct example of multi-factor authentication, understanding how VPNs minimize risk and knowing what a botnet is. On the flip side, the two questions that the majority of respondents answered correctly included identifying the strongest password from a list of four options and understanding that public Wi-Fi networks have risk even when they are password protected. Given the median scores, I was proud of missing only one question – guess I have more reading to do on Botnets. As an industry, it is our duty to not only create systems and securities to improve the tactical effectiveness of fraud prevention, but to educate consumers on many of these topics as well. They often are the first line of defense in stopping fraud and reducing the threat of breaches.

Has the EMV liability shift caused e-commerce fraud to increase 33% in 2016? According to Experian data, CNP fraud increased with Florida, Delaware, Oregon and New York ranked as the riskiest states. Miami accounted for the most fraudulent ZIP™ Codes in the US for shipping and billing fraud.

The adoption of EMV terminals has pressured attackers to migrate their fraud attempts to the card-not-present channel. This is a major driver to the increase in e-commerce fraud attacks – more than 30% over last year. Here’s how this fraud victimization has increased across the country: 16% in North Central states. 25% in Northeastern states. 32% in Southern states. 25% in Western states. Attackers are extremely creative, motivated, and often connected. Protect all points of connection with your customers to prevent e-commerce fraud with a comprehensive, multilayered approach. Where does your state rank?

Legitimate address discrepancies are common, which surprises most people. And handling every address discrepancy as a high fraud risk is operationally expensive and inhibits the customer experience. You can avoid this type of fraud by employing these best practices: Use a distinct Know Your Customer and underlying Customer Identification Program process. Avoid verifications based on self-reported data. Maintain hotlist addresses. Fraud always will find the path of least resistance, and organized criminals will test you daily to isolate the weakest link. Be sure to regularly revisit your own policies and procedures for handling this type of fraud. Address manipulation fraud