Fraud & Identity Management

Today, our TrustInsight division announced a major milestone at this year’s CNP Expo (CardNotPresent). TrustInsight provides reliable TrustScores for a significant portion of US digital consumers leveraging insights from150 of the top online retailers in the US. Now retailers, banks and credit card companies can confidently approve more legitimate CNP transactions. As Surag Patel, vice president, global product management, put it, “We have been working with some of the largest online merchants to help them determine the trustworthiness of a customer during a transaction to help let more good transactions through. The result has been a sharp increase in top-line revenue that can be measured in the tens of millions of dollars.” Patel is leading a panel discussion on Digital Consumer Trust at CNP Expo 2014 on Thursday, May 22 with experts from the merchant community and financial services industry. During the hour-long session, the expert panel will discuss primary research explaining the $40 billion in revenue lost each year to unwarranted CNP credit-card declines and what businesses can do to avoid it. Read the full release here.
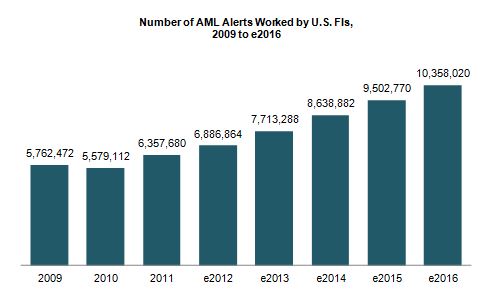
Julie Conroy - Research Director, Aite Group Finding patterns indicative of money laundering and other financial crimes is akin to searching for a needle in a haystack. With the increasing pressure on banks’ anti-money laundering (AML) and fraud teams, many with this responsibility increasingly feel like they’re searching for those needles while a combine is bearing down on them at full speed. These pressures include: Regulatory scrutiny: The high-profile—and expensive—U.S. enforcement actions that took place during the last couple of years underscore the extent to which regulators are scrutinizing FIs and penalizing those who don’t pass muster. Payment volumes and types increasing: As the U.S. economy is gradually easing its way into a recovery, payment volumes are increasing. Not only are volumes rebounding to pre-recession levels, but there have also been a number of new financial products and payment formats introduced over the last few years, which further increases the workload for the teams who have to screen these payments for money-laundering, sanctions, and global anti-corruption-related exceptions. Constrained budgets: All of this is taking place during a time in which top line revenue growth is constrained and financial institutions are under pressure to reduce expenses and optimize efficiency. Illicit activity on the rise: Criminal activity continues to increase at a rapid pace. The array of activity that financial institutions’ AML units are responsible for detecting has also experienced a significant increase in scope over the last decade, when the USA PATRIOT Act expanded the mandate from pure money laundering to also encompass terrorist financing. financial institutions have had to transition from activity primarily focused on account-level monitoring to item-level monitoring, increasing by orders of magnitude the volumes of alerts they must work (Figure 1) Figure 1: U.S. FIs Are Swimming in Alerts Source: Aite Group interviews with eight of the top 30 FIs by asset size, March to April 2013 There are technologies in market that can help. AML vendors continue to refine their analytic and matching capabilities in an effort to help financial insitutions reduce false positives while not adversely affecting detection rates. Hosted solutions are increasingly available, reducing total cost of ownership and making software upgrades easier. And many institutions are working on internal efficiency efforts, reducing vendors, streamlining processes, and eliminating the number of redundant efforts. How are institutions handling the increasing pressure cooker that is AML compliance? Aite Group wants to know your thoughts. We are conducting a survey of financial insitution executives to understand your pain points and proposed solutions. Please take 20 minutes to share your thoughts, and in return, we’ll share a complimentary copy of the resulting report. This data can be used to compare your efforts to those of your peers as well as to glean new ideas and best practices. All responses will be kept confidential and no institutions names will be mentioned anywhere in the report. You can access the survey here: SURVEY

As we discussed in our earlier Heartbleed post, there are several new vulnerabilities online and in the mobile space increasing the challenges that security professionals face. Fraud education is a necessity for companies to help mitigate future fraud occurrences and another critical component when assessing online and mobile fraud is device intelligence. In order to be fraud-ready, there are three areas within device intelligence that companies must understand and address: device recognition, device configuration and device behavior. Device recognition Online situational awareness starts with device recognition. In fraudulent activity there are no human users on online sites, only devices claiming to represent them. Companies need to be able to detect high-risk fraud events. A number of analytical capabilities are built on top of device recognition: Tracking the device’s history with the user and evaluating its trust level. Tracking the device across multiple users and evaluating whether the device is impersonating them. Maintaining a list of devices previously associated with confirmed fraud. Correlation of seemingly unrelated frauds to a common fraud ring and profiling its method of operation. Device configuration The next level of situational awareness is built around the ability to evaluate a device’s configuration in order to identify fraudulent access attempts. This analysis should include the following capabilities: Make sure the configuration is compatible with the user it claims to represent. Check out internal inconsistencies suggesting an attempt to deceive. Review whether there any indications of malware present. Device behavior Finally, online situational awareness should include robust capabilities for profiling a device’s behavior both within individual accounts and across multiple users: Validate that the device focus is not on activity types often associated with fraud staging. Confirm that the timing of the activities do not seem designed to avoid detection rules. By proactively managing online channel risk and combining device recognition with a powerful risk engine, organizations can uncover and prevent future fraud trends and potential attacks. Learn more about Experian fraud intelligence products and services from 41st Parameter, a part of Experian.
The discovery of Heartbleed earlier this year uncovered a large-scale threat that exploits security vulnerability in OpenSSL posing a serious security concern. This liability gave hackers access to servers for many Websites and put consumers’ credentials and private information at risk. Since the discovery, most organizations with an online presence have been trying to determine whether their servers incorporate the affected versions of OpenSSL. However, the impact will be felt even by organizations that do not use OpenSSL, as some consumers could reuse the same password across sites and their password may have been compromised elsewhere. The new vulnerabilities online and in the mobile space increase the challenges that security professionals face, as fraud education is a necessity for companies. Our internal fraud experts share their recommendation in the wake of the Heartbleed bug and what companies can do to help mitigate future occurrences. Here are two suggestions on how to prevent compromised credentials from turning into compromised accounts: Authentication Adopting layered security strategy Authentication The importance of multidimensional and risk-based authentication cannot be overstated. Experian Decision Analytics and 41st Parameter® recommend a layered approach when it comes to responding to future threats like the recent Heartbleed bug. Such methods include combining comprehensive authentication processes at customer acquisition with proportionate measures to monitor user activities throughout the life cycle. "Risk-based authentication is best defined and implemented in striking a balance between fraud risk mitigation and positive customer experience," said Keir Breitenfeld, Vice President of Fraud Product Management for Experian Decision Analytics. "Attacks such as the recent Heartbleed bug further highlight the foundational requirement of any online business or agency applications to adopt multifactor identity and device authentication and monitoring processes throughout their Customer Life Cycle." Some new authentication technologies that do not rely on usernames and passwords could be part of the broader solution. This strategic change involves the incorporation of broader layered-security strategy. Using only authentication puts security strategists in a difficult position since they must balance: Market pressure for convenience (Note that some mobile banking applications now provide access to balances and recent transactions without requiring a formal login.) New automated scripts for large-scale account surveillance. The rapidly growing availability of compromised personal information. Layered security "Layered security through a continuously refined set of ‘locks’ that immediately identify fraudulent access attempts helps organizations to protect their invaluable customer relationships," said Mike Gross, Global Risk Strategy Director for 41st Parameter. "Top global sites should be extra vigilant for an expected rush of fraud-related activities and social engineering attempts through call centers as fraudsters try to take advantage of an elevated volume of password resets." By layering security consistently through a continuously refined set of controls, organizations can identify fraudulent access attempts, unapproved contact information changes and suspicious transactions. Learn more about fraud intelligence products and services from 41st Parameter, a part of Experian.

By: Maria Moynihan In less than a year, my information has been compromised twice by a data breach. The companies involved varied significantly by way of size and type, yet both reacted expeditiously to inform me of the incident. As much as I appreciated the quick response and notification, I couldn’t help but wonder how well prepared we all are to handle these types of incidents within our own organizations. I recently read somewhere that data breaches are to be expected – like death and taxes. Can this be true? A recent Ponemon Institute Study, 2013 Cost of a Data Breach, highlighted alarming statistics around the typical impact a breach has on an organization. With costs amounting to approximately $5.4M and impact to brands ranging anywhere from $184M to $330M in losses, organizations cannot afford to pass breaches off as inevitable. Organizations must tighten their security standards, understand the evolving data breach environment and ensure their response plans are continuously enhanced to address emerging issues. To better understand what may lie ahead, Experian has developed six key predictions for how concerns about data breaches will evolve: 1. Data breach cost will be down – but still impactful The cost per record of a data breach will continue to decline, however security incidents and other breaches may still cause significant business disruption if not properly managed. 2. Will the Cloud and Big Data = Big International Breaches? With the rise of the cloud, data is now moving seamlessly across borders making the potential for complex, international breaches more possible. 3. Healthcare Breaches: Opening the Floodgates With the addition of the Healthcare Insurance Exchanges, millions of individuals will be introduced into the healthcare system and as a result, will increase the vulnerability of the already susceptible healthcare industry. 4. A Surge in Adoption of Cyber Insurance Many companies will look beyond investing in technology to protect against attacks and towards the insurance market to manage financial ramifications of breaches. 5. Breach Fatigue – Rise in Consumer Fraud? As the number of reported breaches in the media increases and the frequency of notifications that consumers receive grow, they may become apathetic towards the subject, thereby exposing themselves to greater risk. 6. Beyond the Regulatory Check Box State regulators and law enforcement will turn a new leaf this year, devoting significant attention to helping organizations better manage breaches. What is your organization doing to improve its data breach preparedness plan? Check out our 2014 Data Breach Industry Forecast and guide to handling data breach response. Check out other related content on data breach resolution.

By: Matt Sifferlen On January 17th, we celebrated the 308th birthday of one of America's most famous founding fathers, Ben Franklin. I've been a lifelong fan of his after reading his biography while in middle school, and each year when his birthday rolls around I'm inspired to research him a bit more since there is always something new to learn about his many meaningful contributions to this great nation. I find Ben a true inspiration for his capacity for knowledge, investigation, innovation, and of course for his many witty and memorable quotes. I think Ben would have been an exceptional blogger back in his day, raising the bar even higher for Seth Godin (one of my personal favorites) and other uber bloggers of today. And as a product manager, I highly respect Ben's lifelong devotion to improving society by finding practical solutions to complex problems. Upon a closer examination of many of Ben's quotes, I now feel that Ben was also a pioneer in providing useful lessons in commercial fraud prevention. Below is just a small sampling of what I mean. “An ounce of prevention is worth a pound of cure” - Preventing commercial fraud before it happens is the key to saving your organization's profits and reputation from harmful damage. If you're focused on detecting fraud after the fact, you've already lost. “By failing to prepare, you are preparing to fail.” - Despite the high costs associated with commercial fraud losses, many organizations don't have a process in place to prevent it. This is primarily due to the fact that commercial fraud happens at a much lower frequency than consumer fraud. Are you one of those businesses that thinks "it'll never happen to me?" “When the well’s dry, we know the worth of water.” - So you didn't follow the advice of the first two quotes, and now you're feeling the pain and embarrassment that accompanies commercial fraud. Have you learned your lesson yet? “After crosses and losses, men grow humbler and wiser.” Ah, no lender likes losses. Nothing like a little scar tissue from "bad deals" related to fraud to remind you of decisions and processes that need to be improved in order to avoid history repeating itself. “Honesty is the best policy.” - Lots of businesses stumble on this part, failing to communicate when they've been compromised by fraud or failing to describe the true scope of the damage. Be honest (quickly!) and set expectations about what you're doing to limit the damage and prevent similar instances in the future. “Life’s tragedy is that we get old too soon and wise too late.” - Being too late is a big concern when it comes to fraud prevention. It's impossible to prevent 100% of all fraud, but that shouldn't stop you from making sure that you have adequate preventive processes in place at your organization. “Never leave that till tomorrow which you can do today.” - Get a plan together now to deal with fraud scenarios that your business might be exposed to. Data breaches, online fraud and identity theft rates are higher than they've ever been. Shame on those businesses that aren't getting prepared now. “Beer is living proof that God loves us and wants us to be happy.” - I highly doubt Ben actually said this, but some Internet sites attribute it to him. If you already follow all of his advice above, then maybe you can reward yourself with a nice pale ale of your choice! So Ben can not only be considered the "First American," but he can also be considered one of the first fraud prevention visionaries. Guess we'll need to add one more thing to his long list of accomplishments!

In the days following the Target breach, both clarity and objectivity are in short supply. Everything that didn’t already exist became suddenly the cure-all – EMV being one. Retailers bristle, albeit in private – due to the asymmetry in blame they have come to share compared to banks – despite having equal ownership of the mess they have come to call payments. Issuers and Schemes scramble to find an empty deck chair on the Titanic, just to get a better view of the first of the lifeboats capsizing. Analogies aside, we may never fully eliminate breaches. Given an infinite amount of computing power and equal parts human gullibility – whether its via brute forcing encryption systems or through social engineering – a breach is only a matter of time. But we can shorten the half-life of what is stolen. And ensure that we are alerted when breaches occur – as fraudsters take care to leave little trace behind. Yet today our antiquated payments system offer up far too many attack vectors to a fraudster, that the sophistication in attempts of the likes of what we saw at Target, is the exception and not the norm. But are the retailers absolved of any responsibility? Hardly. Questions from a breach: According to Target, malware was found on Target’s PoS – presumably pushed by unauthorized outsiders or via compromised insiders. If so, how is it that unauthorized code managed to find its way to all or most of its PoS terminals? Could this have been uncovered by performing a binary or checksum comparison first, to ensure that files or packages are not tampered with, before they are deployed to the Point-of-Sale? Such a step could have certainly limited the attack vectors to a small group of people with administrative access – who would have the need to handle keys and checksums. Further, depending on the level of privilege accorded to every binary that gets deployed to the point of sale – Target could have prevented an unauthorized or remotely installed program from performing sensitive functions such as reading consumer data – either in transit or in RAM. That said – I am not sure if PoS manufacturers provide for such layered approach towards granting access and execution privileges to code that is deployed to their systems. If not, it should. Where DOES EMV come in? EMV helps to verify the card – indisputably. Beyond that, it offers no protection to either the consumer or the merchant. The risk of EMV, and it’s infallibility in the eyes of its true believers, is that it can lull the general public in to a sense of false security – much like what we have now under Reg E and Reg Z. With EMV, PAN and PIN continues to be passed in the clear, unencrypted. Retailers could deploy EMV terminals and still be riddled like cheese by fraudsters who can siphon off PANs in transit. Fraudsters who may find it nearly impossible to create counterfeit cards, instead will migrate online where inadequate fraud mitigation tools prevail – and those inadequacies will force both banks and retailers to be heavy handed when it comes to determining online fraud. Friction or Fraud should not be the only two choices. Solving Card Not Present Fraud: There are no silver bullets to solve Card Not Present fraud. Even with EMV Chip/Pin, there is an opportunity to put a different 16 digit PAN on the front of the card versus the one that is on the magstripe/chip. (I am told that Amex does this for its Chip/pin cards.) The advantage is that a fraudster using a fraudulently obtained PAN from the chip for an e-commerce purchase will standout to an card issuer compared to the legit customer using a different PAN on the front of the card for all her e-commerce purchases. This maybe one low tech way to address CNP fraud alongside of an EMV rollout. But if asking a consumer to enter his Zipcode or show his ID was enough for retail purchases, there exists equivalent friction-bound processes online. Authentication services like 3-D Secure are fraught with friction, and unfairly penalize the customer and indirectly – the retailer and issuer, for its blind attribution of trust in a user provided password or a token or a smart card reader. Where it may (in some cases) undeniably verifies consumer presence, it also overwhelms – and a customer who is frustrated with a multi-step verification will simply shop somewhere else or use Paypal instead. Ever had to input your Credit Card Verification code (CVV2 or CVC2) on an Amazon purchase? Me neither. Fraud in connected commerce: As connected devices outnumber us, there needs to be an approach that expands the notion of identity to look beyond the consumer and start including the device. At the core, that is what solutions like 41st Parameter – an Experian company, focuses on – which enables device attributes to collectively construct a more sophisticated indicator of fraud in an e-commerce transaction – using 100 or so anonymous device attributes. Further it allows for more nuanced policies for retailers and issuers, to mitigate fraud by not only looking at the consumer or device information in isolation – but in combination with transactional attributes. As a result, retailers and issuers can employ a frictionless, smarter, and more adaptive fraud mitigation strategy that relies less on what could be easily spoofed by a fraudster and more on what can be derived or implied. If you want to know more why this is a more sensible approach to fighting fraud, you should go here to read more about 41st Parameter. Remnants from a breach: Even though the material impact to Target is still being quantified, little doubt remains as to the harm done to its reputation. Target RED card remains largely unaffected, yet it is but a fleeting comfort. Though some, thus had been quick to call decoupled debit a more secure product, those claims choose to ignore the lack of any real consumer protection that is offered alongside of these products. Though Reg E and Reg Z have been largely instrumental in building consumer trust in credit and debit cards, they have also encouraged general public to care less about fraud and credit card security. And this affects more than any other – MCX, whose charter calls for reduction of payment acceptance costs first, and to whom – decoupled debit offered a tantalizing low cost alternative to credit. But when it launches this year, and plans to ask each customer to waive protections offered by Reg E and Reg Z and opt for ACH instead – those consumers will find that choice harder to stomach. Without offering consumers something equivalent, MCX Retailers will find it exceedingly difficult to convince customers to switch. Consumer loyalty to retailer brands was once given as the reason for creating a retailer friendly payment backbone, but with Target’s reputation in tatters – that is hardly something one can bank on these days – pun intended. Where does this leave us? To be completed… This blog post was originally featured at: http://www.droplabs.co/?p=964

The growing cost and number of data breaches has spurred more interest in cyber insurance. While companies often increase investments in technology and training programs to reduce the likelihood of a breach, a recent Ponemon Institute survey of risk-management professionals found that 31 percent of companies surveyed have cyber insurance and 39 percent plan to purchase cyber insurance in the future. Learn how to outline your response plan with our data breach response guide. Source: Managing Cyber Security as a Business Risk: Cyber Insurance in the Digital Age

Billions of dollars are being issued in fraudulent refunds at the state and federal level. Most of the fraud can be categorized around identity theft. An example of this type of fraud may include fraudsters acquiring the Personal Identifying Information (PII) from a deceased individual, buying it from someone not filing or otherwise stealing it from legitimate sources like a doctor’s office. The PII is then used to fill out tax returns, add fraudulent income information and request bogus deductions. Additional forms of tax refund fraud may include: Direct consumer tax refund fraud using real PII of US Citizens to file fraudulent tax returns and claim bogus deductions thereby increasing refund amounts EITC (Earned Income Tax Credit)/ACC (Additional Childcare Credit) fraud which is usually perpetrated with the assistance of a tax preparer and claiming improper cash payments and/or deductions for non-existent children. Tax Preparer Fraud where tax preparers purposefully submit false information on tax returns or file false returns for clients. Under reporting of income on tax filings. Taking multiple Homestead Exemptions for tax credit. Since this Fraud more often occurs as an early filing using Fraudulent or stolen PII the individual consumer is at risk for long term Identity issues. Exacerbating the tax refund fraud problem: The majority of returns that request refunds are now filed online (83% of all federal filings in 2012 were online) -if you file online, there is no need to submit a W-2 form with that online filing. If your employment information cannot be pulled into the forms by your tax software you can fill it in manually. The accuracy of information regarding employer and wage information for which deductions are based, is only verified after the refund is issued. Refunds directly deposited - filers now have the option to have their refunds deposited into a bank account for faster receipt. Once these funds are deposited and withdrawn there is no way to trace where the funds have gone. Refunds provided on debit cards – filers can request their refund in the form of a debit card. This is an even bigger problem than bank account deposits because once issued, there is no way to trace who uses a debit card and for what purpose. So what do you need to look for when reviewing tax fraud prevention tools? Look for a provider that has experience in working with state and federal government agencies. Proven expertise in this domain is critical, and experience here means that the provider has cleared the disciplined review process that the government requires for businesses they do business with. Look for providers with relevant certifications for authentication services, such as the Kantara Identity Assurance Framework for levels of identity assurance. Look for providers that can authenticate users by verifying the device they’re using to access your applications. With over 80% of tax filings occurring online, it is critical that any identity proofing strategy also allows for the capability to verify the source or device used to access these applications. Since tax fraudsters don’t limit their use of stolen IDs to tax fraud and may also use them to perpetrate other financial crimes such as opening lines of credit – you need to be looking at all avenues of fraudulent activity If fraud is detected and stopped, consider using a provider that can offer post fraud mitigation processes for your customers/potential victims. Getting tax refunds and other government benefits into the right hands of their recipients is important to everyone involved. Since tax refund fraud detection is a moving target, it’s buyer beware if you hitch your detection efforts to a provider that has not proven their expertise in this unique space.

By: Matt Sifferlen I recently read interesting articles on the Knowledge@Wharton and CNNMoney sites covering the land grab that's taking place among financial services startups that are trying to use a consumer's social media activity and data to make lending decisions. Each of these companies are looking at ways to take the mountains of social media data that sites such as Twitter, Facebook, and LinkedIn generate in order to create new and improved algorithms that will help lenders target potential creditworthy individuals. What are they looking at specifically? Some criteria could be: History of typing in ALL CAPS or all lower case letters Frequent usage of inappropriate comments Number of senior level connections on LinkedIn The quantity of posts containing cats or annoying self-portraits (aka "selfies") Okay, I made that last one up. The point is that these companies are scouring through the data that individuals are creating on social sites and trying to find useful ways to slice and dice it in order to evaluate and target consumers better. On the consumer banking side of the house, there are benefits for tracking down individuals for marketing and collections purposes. A simple search could yield a person's Facebook, Twitter, or LinkedIn profile. The behaviorial information can then be leveraged as a part of more targeted multi-channel and contact strategies. On the commercial banking side, utilizing social site info can help to supplement any traditional underwriting practices. Reviewing the history of a company's reviews on Yelp or Angie's List could share some insight into how a business is perceived and reveal whether there is any meaningful trend in the level of negative feedback being posted or potential growth outlook of the company. There are some challenges involved with leveraging social media data for these purposes. 1. Easily manipulated information 2. Irrelevant information that doesn't represent actual likes, thoughts or relevant behaviors 3. Regulations From a Fraud perspective, most online information can easily and frequently be manipulated which can create a constantly moving target for these providers to monitor and link to the right customer. Fake Facebook and Twitter pages, false connections and referrals on LinkedIn, and fabricated positive online reviews of a business can all be accomplished in a matter of minutes. And commercial fraudsters are likely creating false business social media accounts today for shelf company fraud schemes that they plan on hatching months or years down the road. As B2B review websites continue to make it easier to get customers signed up to use their services, the downside is there will be even more unusable information being created since there are less and less hurdles for commercial fraudsters to clear, particularly for sites that offer their services for free. For now, the larger lenders are more likely to utilize alternative data sources that are third party validated, like rent and utility payment histories, while continuing to rely on tools that can prevent against fraud schemes. It will be interesting to see what new credit and non credit data will be utilized as a common practice in the future as lenders continue their efforts to find more useful data to power their credit and marketing decisions.

If you're looking to implement and deploy a knowledge-based authentication (KBA) solution in your application process for your online and mobile customer acquisition channels - then, I have good news for you! Here’s some of the upside you’ll see right away: Revenues (remember, the primary activities of your business?) will accelerate up Your B2C acceptance or approval rates will go up thru automation Manual review of customer applications will go down and that translates to a reduction in your business operation costs Products will be sold and shipped faster if you’re in the retail business, so you can recognize the sales revenue or net sales quicker Your customers will appreciate the fact that they can do business in minutes vs. going thru a lengthy application approval process with turnaround times of days to weeks And last but not least, your losses due to fraud will go down To keep you informed about what’s relevant when choosing a KBA vendor, here’s what separates the good KBA providers from the bad: The underlying data used to create questions should be from multiple data sources and should vary in the type of data, for example credit and non-credit Relying on public record data sources is becoming a risky proposition given recent adoption of various social media websites and various public record websites Have technology that will allow you to create a custom KBA setup that is unique to your business and business customers, and the proven support structure to help you grow your business safely Provide consulting (performance monitoring)and analytical support that will keep you ahead of the fraudsters trying to game your online environment by assuring your KBA tool is performing at optimal levels Solutions that can easily interface with multiple systems, and assist from a customer experience perspective. How are your peers in the following 3 industries doing at adopting a KBA strategy to help grow and protect their businesses? E-commerce 21% use KBA today and are satisfied with the results* 13% have KBA on roadmap and the list is growing fast* Healthcare 20% use dynamic KBA* Financial Institutions 30% combination of dynamic & static KBA* 20% dynamic KBA* What are the typical uses of KBA?* Call center Web / mobile verification Enrollment ID verification Provider authentication Eligibility *According to a 2012 report on knowledge-based authentication by Aite Group LLC Knowledge-based authentication, commonly referred to as KBA, is a method of authentication which seeks to prove the identity of someone accessing a service, such as a website. As the name suggests, KBA requires the knowledge of personal information of the individual to grant access to the protected material. There are two types of KBA: "static KBA", which is based on a pre-agreed set of "shared secrets"; and "dynamic KBA", which is based on questions generated from a wider base of personal information.

I don’t know about your neighborhood this past Fourth of July, but mine contained an interesting mix of different types of fireworks. From our front porch, we watched a variety of displays simultaneously: an organized professional fireworks show several miles away, our next-door neighbor setting off the “Safe and Sane” variety and the guy at the end of the street with clearly illegal ones. This made me think about how our local police approach this night. There’s no way they can investigate every report or observance of illegal fireworks as well as all of the other increased activity that occurs on a holiday. So it must come down to prioritization, resources and risk assessment. When it comes to fraud prevention, compliance and risk, businesses — much the same as the police — have a lot of ground to cover and limited resources. Consider the bureau alerts (aka high-risk conditions) on a credit report. They’re an easy, quick tool that can help mitigate risk and save money cost-effectively. When considering bureau alerts, clients commonly ask the following questions: How do I investigate all of the alerts with the limited resources I have? How should I prioritize the ones I am able to review? I usually recommend that, if possible, they incorporate a fraud risk score into their evaluation process. The job of the fraud risk score is to take a very large amount of data and put it into an easy-to-understand and actionable form. It is built to evaluate negative or risky information (at Experian, this includes bureau alerts and many other items) as well as positive or low-risk information (analysis of address, Social Security number, date of birth, and other current and historical personal information). The result is a holistic assessment rather than a binary flag, which can be tuned to resource levels, risk tolerance or other drivers. That’s always where I start. If a fraud score is not an option, then I suggest prioritizing the alerts by the most risk and the frequency of occurrence. With some light analysis, you’ll typically see that the frequency of the most risky alerts is often low, so you can be sure to review each one — or as many as possible. As the frequency of occurrence increases, you then can make decisions about which ones to review or how many of them you can handle. For example, I worked with a client recently to prioritize high-risk but low-frequency alerts. Almost all involved the Social Security number (SSN): The inquiry SSN was recorded as deceased The report contained a security statement There was a high probability that the SSN belongs to another person The best on-file SSN was recorded as deceased I would expect other organizations to have a similar prioritized risk-to-frequency ratio. However, it’s always good (and pretty easy) to make sure your data backs this up. That way, you’re making the most of your limited resources and your tools.

A recent survey of government benefit agencies shows an increased need for fraud detection technology to prevent eligibility fraud. Only 26 percent of respondents currently use fraud detection technology, and 57 percent cite false income reporting as the leading cause of fraud. Insufficient resources and difficulty integrating multiple data sources were the greatest challenges in preventing eligibility fraud.

By: Matt Sifferlen Ah, fraudulent behavior is currently enjoying a bright shiny moment in the sun in today's pop culture, particularly in the world of sports. Whether it's a college athlete being duped for months by telephone conversations with a non-existent girlfriend, or the world's best known cyclist coming clean on a lifetime of deceit, in both cases we're left shaking our heads and laughing, crying, or cringing while telling ourselves "I'm glad I'm too smart to fall for any of this." But are you just kidding yourself? In the case of the college football player, most of us have been scratching our heads wondering how any adult could possibly get strung along for such an extended period of time by such a scam. But if you take a closer look at the interaction between the athlete and the fraudster, you'll see that the fraudster deployed some typical tactics that allowed him to keep the scam living and breathing. In particular, he continuously kept communicating with the athlete via phone and social media, reinforcing the perception that he's aboveboard and genuinely interested in the athlete's life. We see this in commercial fraud interactions too, where the commercial fraudster will perform expected, normal tasks and activities (e.g. making small payments on loans, placing phone calls to lender support staff) that will reinforce the lender's perception that the fraudster is just another normal client. But unlike the athlete's scenario where the fraudster's story unraveled due to no logical conclusion being planned, commercial fraudsters will string lenders along until they get what they want -- then they vanish. Lenders can't get too complacent in their fraud prevention efforts, assuming that the mere presence of normal account activity equates to a validation of a client's authenticity. To complicate things, while electronic communication methods like text messages, emails, and Twitter or Facebook messages offer many convenience advantages, they are ripe for manipulation by fraudsters who certainly find these methods preferable to any awkward face to face encounters with someone they're victimizing. The cyclist that admitted to a lifetime of lies also shines the light on some other tactics that commercial fraudsters might use -- using perceived image and reputation to deceive. Fraudsters will often steal identities of licensed professionals (think physicians, dentists) with favorable credit profiles and use their information to apply for commercial credit or services, knowing that they will likely be viewed favorably due to their impressive profiles, at least on paper. In today's world where lightly staffed underwriting teams struggle to keep up with their workloads, it's easy to see why this tactic can help increase the odds that an application might escape closer scrutiny. After all, it's a doctor's office so what could possibly go wrong? A lot, if you're approving someone who really isn't the doctor! An objective evaluation and screening process where underwriting and analyst staff consistently verify all applicant data and not just cherry pick the ones that look suspicious on paper can go a long way towards avoiding this typical trap set by commercial fraudsters. And in the final scenario of art imitating life, there is the recent release of a major motion picture comedy about identify theft. I'm sure anyone who has been a victim of identity theft won't find hilarity in the scenes of the victim's life getting turned upside down, suddenly unable to use his credit cards at the gas station and being asked about transactions that took place somewhere else in the country that he's never visited. But undoubtedly many folks will find this humor hilarious because we probably know of some horror story that a friend or acquaintance has shared with us that is similar to one of the wacky scenarios covered in this movie. So we'll laugh and take comfort in the fact that we're too smart to get scammed like this, but if the FTC is stating that identity theft will affect 1 in 6 people each year then we're fooling ourselves in thinking that our number won't be up at some point soon. So what can be learned from these high profile pop culture events? I think a couple things. First, know your customers (or athletes, heroes, girlfriends). It sounds simple, but make sure they are who they say they are. Whether you're lending to a business or a consumer, there are tools out there that can enable you to objectively screen your applicants and minimize any bias that might get exploited by fraudsters in a manual review heavy process. If you're not cautious and get burnt, you might not have to go on Oprah or Dr. Phil to explain to your management team where things went horribly wrong, but the level of financial and reputational damage inflicted could be a painful lesson for you and your institution. Or if you're really (un)lucky, maybe they'll make a movie about your story -- wouldn't that be hilarious? (sarcasm intended)

By: Maria Moynihan Cybersecurity, identity management and fraud are common and prevalent challenges across both the public sector and private sector. Industries as diverse as credit card issuers, retail banking, telecom service providers and eCommerce merchants are faced with fraud threats ranging from first party fraud, commercial fraud to identity theft. If you think that the problem isn't as bad as it seems, the statistics speak for themselves: Fraud accounts for 19% of the $600 billion to $800 billion in waste in the U.S. healthcare system annually Medical identity theft makes up about 3% of 8.3 million overall victims of identity theft In 2011, there were 431 million adult victims of cybercrime in 24 countries In fiscal year 2012, the IRS’ specialized identity theft unit saw a 78% spike from last year in the number of ID theft cases submitted The public sector can easily apply the same best practices found in the private sector for ID verification, fraud detection and risk mitigation. Here are four sure fire ways to get ahead of the problem: Implement a risk-based authentication process in citizen enrollment and account management programs Include the right depth and breadth of data through public and private sources to best identity proof businesses or citizens Offer real-time identity verification while ensuring security and privacy of information Provide a Knowledge Based Authentication (KBA) software solution that asks applicants approved random questions based on “out-of-wallet” data What fraud protection tactics has your organization implemented? See what industry experts suggest as best practices for fraud protection and stay tuned as I share more on this topic in future posts. You can view past Public Sector blog posts here.