Tag: identity theft

How can fintech companies ensure they’re one step ahead of fraudsters? Kathleen Peters discusses how fintechs can prepare for success in fraud prevention.

Identify your customers to spot fraud. It’s a simple concept, but it’s not so simple to do. In our 2018 Global Fraud and Identity Report, we found that consumers expect to be recognized and welcomed wherever and whenever they do business. Here are some other interesting findings regarding recognition and fraud: 66% of consumers surveyed appreciate seeing visible security when doing business online because it makes them feel protected. 75% of businesses want security measures that have little impact on consumers. More than half of businesses still rely on passwords as their top form of authentication. Even though you can’t see your customers face-to-face, the importance of being recognized can’t be overemphasized. How well are you recognizing your customers? Can you recognize your customers?

Cybersecurity has become one of the most significant issues impacting international security and political and economic stability. Our new report, Data Breach Industry Forecast 2018, outlines 5 predictions for the data breach industry in the coming year. Here are 3: The U.S. may experience its first large-scale attack on critical infrastructure, causing disruption for governments, companies and private citizens. Failure to comply with the new EU regulations will result in large penalties for U.S. companies. Attackers will use artificial intelligence to render traditional multifactor authentication methods useless. Read all five predictions>

Traditional verification and validation parameters alone are not enough to stop identity fraud. Fortunately, there are many emerging trends and best practices for modern fraud and identity strategies: Applying right-sized fraud and identity proofing solutions to reduce user friction and manage fraud risk appropriately. Maintaining a universal user view by employing diverse breadth and depth of data assets and applied analytics. Expanding the user view through a blended ecosystem by collaborating with vendors, peer agencies, and partners in identity and fraud management. The future of identity proofing is more than just verifying individual identities. Check out our tip sheet linked below for more strategies. Modernize your fraud and identity strategies>

Sophisticated criminals work hard to create convincing, verifiable personas they can use to commit fraud. Here are the 3 main ways fraudsters manufacture synthetic IDs: Credit applications and inquiries that build a synthetic credit profile over time. Exploitation of authorized user processes to take over or piggyback on legitimate profiles. Data furnishing schemes to falsify regular credit reporting agency updates. Fraudsters are highly motivated to innovate their approaches rapidly. You need to implement a solution that addresses the continuing rise of synthetic IDs from multiple engagement points. Learn more

Despite rising concerns about identity theft, most Americans aren’t taking basic steps to make it harder for their information to be stolen, according to a survey Experian conducted in August 2017: Nearly 3 in 4 consumers said they’re very or somewhat concerned their email, financial accounts or social media information could be hacked. This is up from 69% in a similar survey Experian conducted in 2015. Nearly 80% of survey respondents are concerned about using a public Wi-Fi network. Yet, barely half said they take the precaution of using a password-protected Wi-Fi network when using mobile devices. 59% of respondents are annoyed by safety precautions needed to use technology — up 12% from 2015. When your customer’s identity is stolen, it can negatively impact the consumer and your business. Leverage the tools and resources that can help you protect both. Protect your customers and your business>
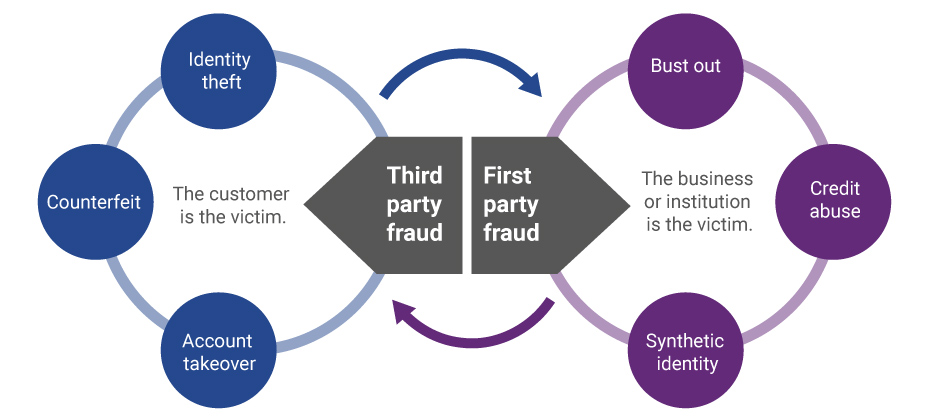
Evolution of first-party fraud to third Third-party and first-party schemes are now interchangeable, and traditional fraud detection practices are less effective in fighting these evolving fraud types. Fighting this shifting problem is a challenge, but it isn’t impossible. To start, incorporate new and more robust data into your identity verification program and provide consistent fraud classification and tagging. Learn more>

Businesses may be increasingly aware of identity theft threats to their customers, but an Experian survey shows that many consumers still seriously underestimate their risk of falling victim to identity thieves. In fact, the persistent and harmful myth that the majority of consumers are not vulnerable to identity theft is badly in need of debunking. Consumer misconceptions The online Experian survey of 1,000 Americans, age 18 and older, found many consumers have a false sense of security about identity theft, even those who regularly engage in behaviors that can dramatically elevate their risk of having their identities stolen. For example: Sixty-two percent of consumers said the security of their personal information online is a minor concern that doesn’t worry them much, and 17 percent never worry about it at all. The top reason for their lack of concern? Twenty-seven percent said it was because they didn’t share that much personal identifiable information (PII) online. Yet consumers store an average of 3.4 types of PII online, and have a large digital footprint that can make it easy for cybercrooks to track and steal their information. Half believe poor credit means identity thieves won’t be interested in stealing their PII. Twelve percent believe they’re safe because they take security precautions, and 9 percent think using only secure websites insulates them from identity theft risks. Risky behaviors When identity theft occurs, consumers are likely to blame any business they associate with the theft. A Gemalto survey found that consumers said protecting their data is 70 percent the responsibility of the companies they do business with, and just 30 percent their own responsibility, Infosecurity Magazine reports. What’s more, 29 percent said they don’t think businesses take their responsibilities seriously enough when it comes to protecting consumer data. Yet the survey found consumers are probably far more responsible for identity theft than they think because they continue to engage in behaviors that put them at greater risk. These include: Shopping online over a public Wi-Fi connection (43 percent) Allowing others to use online account names and passwords (33 percent) Letting others know their mobile device passwords (29 percent) Sharing payment card numbers and/or PINs (25 percent) Letting others use their PII to secure a job or credit (20 percent) Failing to enroll in credit monitoring or identity theft protection services (82 percent) Leaving it up to their banks and credit card companies to catch signs of fraud (81 percent) These dangerous habits can expose consumers’ PII to cybercriminals, even though half of those we surveyed didn’t think they were likely to become victims of identity theft. Impact of identity theft When consumers become identity theft victims, they experience a range of negative emotions and real consequences that affect them personally and financially. According to a survey by the Identity Theft Resource Center, identity theft victims reported feeling frustrated, fearful, angry and stressed. Many had trouble concentrating, lost sleep and felt physically ill because of the crime. They also reported the identity theft overshadowed their personal relationships, their personal and professional credibility, and even affected their ability to get jobs. Some even lost their jobs as a result. What companies can do Clearly, identity theft can be devastating and consumers need to do more to protect themselves. When it occurs, identity theft also undermines the consumer’s trust in companies and institutions, especially if the identity theft occurred in connection to or following a data breach. Helping consumers protect themselves from identity theft benefits everyone. Consumers can avoid the financial and emotional turmoil identity theft causes, and companies can help preserve their relationship with customers. As part of an effective data breach response plan, companies should include a consumer care element that provides breached consumers with: Free identity theft protection and credit monitoring services Dark web and internet records scanning Fraud resolution services Identity theft insurance Myth debunked Year after year, identity theft statistics demonstrate that most consumers are at risk of falling prey to identity thieves, no matter what they believe to the contrary. Unfortunately, consumers continue to take actions that can place their identities at risk. While you can’t force your customers to stop accessing their bank accounts over airport Wi-Fi or using the same password for all their financial accounts, you can take steps to reduce the risk they’ll experience identity theft because of something your organization did or didn’t do. Helping consumers protect themselves from identity theft makes good business sense, and it’s the right thing to do. Plus, consumers expect it; according to the Ponemon Institute’s “Mega Data Breach: Consumer Sentiment” survey, 63 percent of consumers believe a company that experiences a data breach should offer free identity protection to customers affected by the breach. Learn more about our Data Breach solutions

A combination of mass identity data compromise and the increasing abilities of organized fraud rings has created a synthetic identity epidemic that is impacting all markets. Here are the three ways that synthetic identities are generally created: Credit applications and inquiries that result in synthetic credit profile creation or build. Exploitation of the authorized user process designed to take over or piggyback on legitimate credit profiles. Data furnishing schemes that falsify regular credit reporting agency updates. When it comes to fighting synthetic fraud, we all need to be a part of the solution – or we are just a part of the problem. Mitigate synthetic identity fraud >

With the recent switch to EMV and more than 4.2 billion records exposed by data breaches last year*, attackers are migrating their fraud attempts to the card-not-present channel. Our recent analysis found the following states to be the riskiest for e-commerce fraud in 2016. Delaware Oregon Florida New York Nevada Attackers are extremely creative, motivated, and often connected. Prevent e-commerce fraud by protecting all of your customer contact points. Fraud Heat Map>

Turns out, Americans still don’t know much about CyberSecurity. That’s according to new research from the Pew Data Center, which conducted a cybersecurity knowledge quiz. The 13 question quiz was designed to test American’s knowledge on a number of cybersecurity issues and terms. A majority of online adults can identify a strong password and recognize the dangers of using public Wi-Fi. However, many struggle with more technical cybersecurity concepts, such as how to identify true two-factor authentication or determine if a webpage they are using is encrypted. As we in the industry know, cybersecurity is a complicated and diverse subject, but given the pervasiveness of news around cybersecurity, I was still a little surprised by the lack of knowledge. The typical (median) respondent answered only five of the 13 questions correctly (with a mean of 5.5 correct answers). 20% answered more than eight questions accurately, and just 1% received a “perfect score” by correctly answering all 13 questions. The study showed that public knowledge of cybersecurity is low on some relatively technical issues, like identifying the correct example of multi-factor authentication, understanding how VPNs minimize risk and knowing what a botnet is. On the flip side, the two questions that the majority of respondents answered correctly included identifying the strongest password from a list of four options and understanding that public Wi-Fi networks have risk even when they are password protected. Given the median scores, I was proud of missing only one question – guess I have more reading to do on Botnets. As an industry, it is our duty to not only create systems and securities to improve the tactical effectiveness of fraud prevention, but to educate consumers on many of these topics as well. They often are the first line of defense in stopping fraud and reducing the threat of breaches.

Has the EMV liability shift caused e-commerce fraud to increase 33% in 2016? According to Experian data, CNP fraud increased with Florida, Delaware, Oregon and New York ranked as the riskiest states. Miami accounted for the most fraudulent ZIP™ Codes in the US for shipping and billing fraud.

The adoption of EMV terminals has pressured attackers to migrate their fraud attempts to the card-not-present channel. This is a major driver to the increase in e-commerce fraud attacks – more than 30% over last year. Here’s how this fraud victimization has increased across the country: 16% in North Central states. 25% in Northeastern states. 32% in Southern states. 25% in Western states. Attackers are extremely creative, motivated, and often connected. Protect all points of connection with your customers to prevent e-commerce fraud with a comprehensive, multilayered approach. Where does your state rank?

We’re excited to announce Family Account Management: a new feature available for our partners that makes it easy for their subscribers to extend identity protection services to family and friends. Family Account Management allows our partners to offer quick and easy enrollment, enabling new subscribers to opt in to a family plan by inputting family or friends’ email addresses within their portal. Subscribers can invite anyone of the age of 18 to join. Every family has different security needs and preferences. This feature offers plan options that can be configured to match the primary subscriber’s current enrolled services, or customized to include a set of services that best suits each family’s needs. The Consumer Sentinel Network, a division of the Federal Trade Commission, reported over 1.2 million fraud-related complaints in 2015. With identity fraud on the rise, we need to be more vigilant than ever before and take steps to improve our own security and the security of our loved ones. We all have unique identity elements, including birthday, email address, and Social Security number, and monitoring one person’s identity elements won’t minimize risk for other family members. That’s why Family Account Management is so important, allowing subscribers to extend coverage for what matters most – family. “Families are more connected than ever before, but with more ways to stay connected, there are new threats putting families at risk of identity theft,” said Joe Ross, Experian President and Co-Founder. “With Family Account Management, businesses can provide their subscribers with an easy and convenient way to extend identity protection services to their loved ones.” Visit our website for more information on identity protection products you can offer your customers and stay up to date with all Experian news on LinkedIn.

Internet-connected devices provide endless possibilities, but they rely on technology and collected data to deliver on their promises. This can compromise your network security. Follow these tips to enjoy the conveniences provided by Internet of Things devices while keeping your network safe. Look for devices that use end-to-end encryption. Change default passwords before connecting devices to your network. Enable two-factor authentication, when available. Leverage all security options, such as passwords, encryption, firewalls and firmware. The Internet of Things is only as strong as its weakest link. That's why it’s so important to understand and treat each connected device as part of a broader network. More security tips