Travel

This article first appeared in Baseline Magazine Since it is possible for cyber-criminals to create a synthetic person, businesses must be able to differentiate...

Identity management traditionally has been made up of creating rigid verification processes that are applied to any access scenario. But the market is evolving...
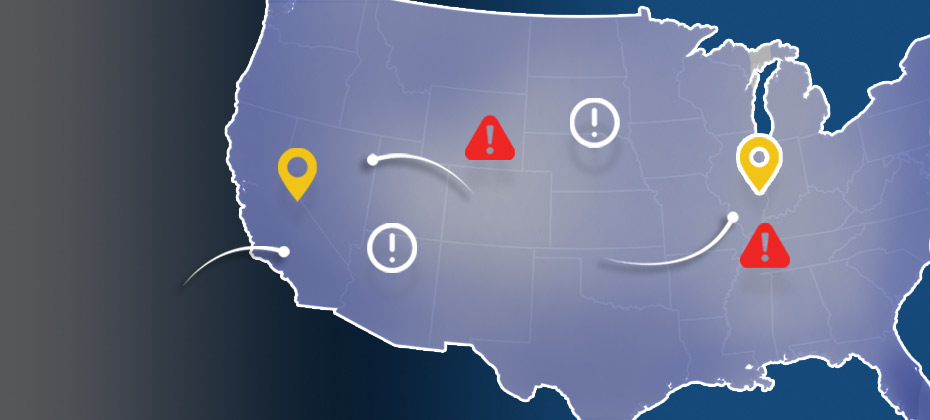
2015 data shows where billing and shipping e-commerce fraud attacks occur in the United States Experian e-commerce fraud attacks and rankings now available Does...

Loyalty fraud and the customer experience Criminals continue to amaze me. Not surprise me, but amaze me with their ingenuity. I previously wrote about...

What is blockchain? Blockchain is beginning to get a lot of attention, so I thought it might be time to figure out what it...

Ensure you’re protecting consumer data privacy Data Privacy Day is a good reminder for consumers to take steps to protect their privacy online —...

Looking at true fraud rate I’ve talked with many companies over the years about their fraud problems. Most have a genuine desire to operate...

Leveraging customer intelligence in the age of mass data compromise Hardly a week goes by without the media reporting a large-scale hack of sensitive...

Profile of an online fraudster I recently read a study about the profile of a cybercriminal. While I appreciate the study itself, one thing...

What the EMV Shift means for you I recently facilitated a Webinar looking at myths and truths in the market regarding the EMV liability...
While walking through a toy store in search of the perfect gift for a nephew, I noticed the board game Risk, which touts itself...

What will the EMV shift really mean for consumers and businesses here in the U.S.? Businesses and consumers across the U.S. are still adjusting...

Understanding and managing first party fraud Background/Definitions Wherever merchants, lenders, service providers, government agencies or other organizations offer goods, services or anything of value...

Imagine the following scenario: an attacker acquires consumers’ login credentials through a data breach. They use these credentials to test account access and observe...

Cont. Understanding Gift Card Fraud By: Angie Montoya In part one, we spoke about what an amazing deal gift cards (GCs) are, and why...
