Travel

Enterprise Security Magazine recently named Experian a Top 10 Fraud and Breach Protection Solutions Provider for 2020. Accelerating trends in the digital economy--stemming from stay-at-home orders and rapid increases in e-commerce and government funding--have created an attractive environment for fraudsters. At the same time, there’s been an uptick in the amount of personally identifiable information (PII) available on the dark web. This combination makes innovative fraud and breach solutions more crucial than ever. Enterprise Security Magazine met with Kathleen Peters, Experian’s Chief Innovation Officer, and Michael Bruemmer, Vice President of Global Data Breach and Consumer Protection, to discuss COVID-19 digital trends, the need for robust fraud protection, and how Experian’s end-to-end breach protection services help businesses protect consumers from fraud. According to the magazine, “With Experian’s best in class analytics, clients can rapidly respond to ever-changing environments by utilizing offerings such as CrossCore® and Sure ProfileTM to identify and prevent fraud.” In addition to our commitment to develop new products to combat the rising threat of fraud, Experian is focused on helping businesses minimize the consequences of a data breach. The magazine noted that, “To serve as a one-stop-shop for data breach protection, Experian offers a wide range of auxiliary services such as incident management, data breach notification, identity protection, and call center support.” We are continuously working to create and integrate innovative and robust solutions to prevent and manage different types of data breaches and fraud. Read the full article Contact us

Every few months we hear in the news about a fraud ring that has been busted here in the U.S. or in another part of the world. In May, I read about a fraud ring based in Georgia and Louisiana that bought 13,000 stolen identities of children who were on the Louisiana Medicaid program and billed the government for services not rendered. This group defrauded the Medicaid program of more than $500,000. This is just one of many stories that we hear about fraud rings, and given the rapidly changing economic environment, now is the time for businesses to think about how to protect against fraud rings. There are a number of challenges that organizations may have when it comes to sharing trends and collaborations, understanding the ways to tie fraud rings together, creating treatments for identifying fraud rings and ways to store and catalogue fraud ring experiences so they can be easily recognized. The trouble with identifying fraud rings It’s important to understand the challenges that organizations have because they see the fraud rings through their own internal lens. Here are a few of the top things businesses should work on: Think like a fraudster. This will help businesses become more creative in their approach to fraud prevention. Facilitate internal collaboration. Share with in-organization partners. Sometimes this can be difficult due to organizational structure. Promote external collaboration. Intel-sharing groups are a great way for businesses to network within their industries and learn about the fraud that others are seeing. An organization that I’ve worked with in the past is the National Cyber Forensic and Training Alliance (NCFTA). Putting the pieces together How do businesses identify a fraud ring? There are three steps to get started. The first is reviewing and understanding the data. Fraudsters are lazy and want to replicate the process over and over again, and because of this there is always some piece of information that is repeated. It could be a name, an email address, device fingerprint, or similar. The second step is tying the fraud ring together. This is done by creating rules to help identify the trends. Having rules in place to identify fraud rings allows businesses to easily pull stats together for their leadership. Lastly, applying an acronym or name to the particular fraud ring and adding comments to the cases associated with a particular ring will help with post-investigation analysis. Learning from the past Before I became a consultant, I remember identifying a fraud ring that was submitting events with the same language pack and where the device fingerprint was staying consistent. Those events were being referred out for review and marked with the same note. At a post-mortem review, I was able to talk to the fraud ring we had seen, and it was easy to pull all events associated with this fraud ring because my team had marked the events with the same comments. Another fraud ring example happened a few years ago. A client called me and said that they were under a fraud attack and this fraud ring was rotating the email handle. I reviewed the data and came up with a rule to catch this activity. Fraud rings will use email handle rotation to help them keep track of accounts that are opened or what emails they used in the past. By coupling the email handle rotation with an email verification service like Emailage, this insight could be very telling. I would assume that when fraud rings use email handle rotation these emails are new and have just been created. These are just a few of the many fraud rings that I’ve encountered over the course of my career and I’m sure there will be a lot more in the years to come. The best advice I can give to anyone that reads this post is to understand the data that you are reviewing, look for anomalies within the data, ask questions and test your theories by running queries on the data that you’re reviewing. I would love to hear about the different fraud rings that you’ve encountered over your career. Stay safe. Contact us

This week, Experian released a new version of our CrossCore® digital identity and fraud risk platform, adding new tools and functionality to help businesses quickly respond to today’s emerging fraud threats. The ability to confidently recognize your customers and safeguard their digital transactions is becoming an increasing challenge for businesses. Fraud threats are already rising across the globe as fraudsters take advantage of the global health crisis and rapidly shifting economic conditions. CrossCore combines risk-based authentication, identity proofing and fraud detection into a single cloud platform, which means businesses can more quickly respond to an ever-changing environment. And with flexible decisioning orchestration and advanced analytics, businesses can make real-time risk decisions throughout the customer lifecycle. “Now more than ever, businesses need to lean on capabilities and technology that will allow them to rapidly respond in these challenging times, increase identity confidence in every transaction, and provide a safe and convenient experience for customers,” said E.K. Koh, Experian’s Senior Vice President of Global Identity & Fraud Solutions in a recent press release. “This new CrossCore release enables businesses to easily leverage best-in-class, pre-integrated identity and fraud services through simple self-service.” This new version of CrossCore features a cloud architecture, modern user interface, progressive risk assessments, faster response times, self-service workflow configuration, and a transactional volume reporting dashboard. These enhancements give you a simpler way to manage how backing applications are utilized, allow you to analyze key performance indicators in near real-time, and empower you to catch more fraud faster - without impacting the customer experience. “Recent Aite Group research shows that many banks have seen digital channel usage increase 250% in the wake of the pandemic, so ensuring a seamless and safe customer experience is more important than ever,” said Julie Conroy, Research Director at Aite Group. “Platforms such as CrossCore that can enable businesses to nimbly respond to changing patterns of customer behavior as well as rapidly evolving attack tactics are more important than ever, as financial services firms work to balance fraud mitigation with the customer experience.” CrossCore is the first identity and fraud platform that enables you to connect, access, and orchestrate decisions across multiple solutions. With the newest version, Experian enhances your ability to consolidate numerous fraud risk signals into a single, holistic assessment to improve operational processes, stay ahead of fraudsters, and protect your customers. Read Press Release Learn More About CrossCore

Pickups are the most common vehicle in operation at 20% share today and hold 16.5% of new vehicle registrations in the market in Q1 2019.

There are four reasons why the auto industry should be enthusiastic about the electric vehicle segment’s future.

While electric vehicles remain a relatively niche part of the market, with only 0.9 percent of the total vehicle registrations through June 2018, consumer demand has grown quite significantly over the past few years. As I mentioned in a previous blog post, electric vehicles held just 0.5 percent in 2016. Undoubtedly, manufacturers and retailers will look to capitalize on this growing segment of the population. But, it’s not enough to just dig into the sales number. If the automotive industry really wants to position itself for success, it’s important to understand the consumers most interested in electric vehicles. This level of data can help manufacturers and retailers make the right decisions and improve the bottom line. Based on our vehicle registration data, below is detailed look into the electric vehicle consumer. Home Value Somewhat unsurprisingly, the people most likely to purchase an electric vehicle tend to own more expensive homes. Consumers with homes valued between $450,000-$749,000 made up 25 percent of electric vehicle market share. And, as home values increase, these consumers still make up a significant portion of electric vehicle market. More than 15 percent of the electric vehicle market share was made up by those with homes valued between $750,000-$999,000, and 22.5 percent of the share was made up by those with home values of more than $1 million. In fact, consumers with home values of more than $1 million are 5.9 times more likely to purchase an electric vehicle than the general population. Education Level Breaking down consumers by education level shows another distinct pattern. Individuals with a graduate degree are two times more likely to own an electric vehicle. Those with graduate degrees made up 28 percent of electric vehicle market share, compared to those with no college education, which made up just 11 percent. Consumer Lifestyle Segmentation Diving deeper into the lifestyles of individuals, we leveraged our Mosaic® USA consumer lifestyle segmentation system, which classifies every household and neighborhood in the U.S. into 71 unique types and 19 overachieving groups. Findings show American Royalty, who are described as wealthy, influential couples and families living in prestigious suburbs, led the way with a 17.8 percent share. Following them were Silver Sophisticates at 11.9 percent. Those in this category are described as mature couples and singles living an upscale lifestyle in suburban homes. Rounding out the top three were Cosmopolitan Achiever, described as affluent middle-aged and established couples and families who enjoy a dynamic lifestyle in metro areas. Their share was 10.1 percent. If manufacturers and retailers go beyond just the sales figures, a clearer picture of the electric vehicle market begins to form. They have an opportunity to understand that wealthier, more established individuals with higher levels of education and home values are much more likely to purchase electric vehicles. While these characteristics are consistent, the different segments represent a dynamic group of people who share similarities, but are still at different stages in life, leading different lifestyles and have different needs. As time wears on, the electric vehicle segment is poised for growth. If the industry wants to maximize its potential, they need to leverage data and insights to help make the right decisions and adapt to the evolving marketplace.
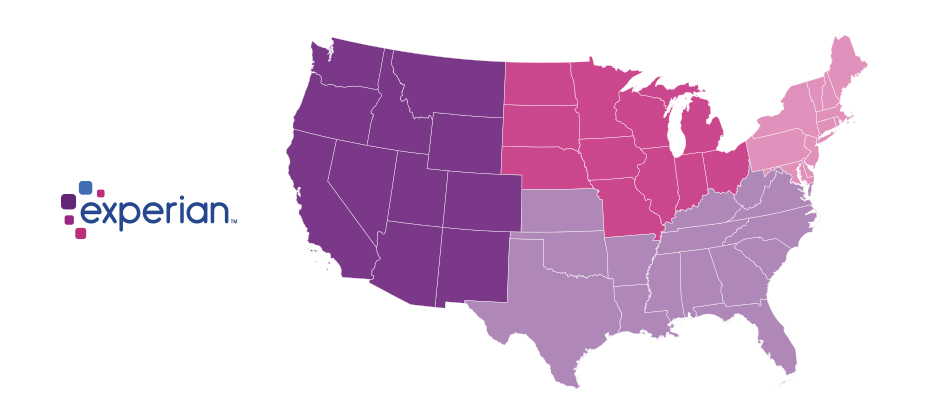
With 16.7 million reported victims of identity fraud in 2017 (that’s 6.64 percent of the U.S. population), it was another record year for the number of fraud victims. And as online and mobile transaction growth continued to significantly outpace brick-and-mortar growth, criminal attacks also grew rapidly. This past year, we saw an increase of more than 30 percent in e-commerce fraud attacks compared with 2016. As we’ve done over the past three years, Experian® analyzed millions of online transactions to identify fraud attack rates for both shipping and billing locations across the United States. We looked at several data points, including geography and IP address, to help businesses better understand how and where fraud is being perpetrated so they can better protect against it. The 2017 e-commerce fraud attack rate analysis shows: Delaware and Oregon continue to be the riskiest states for both billing and shipping fraud. Delaware; Oregon; Washington, D.C.; Florida; and Georgia are the top five riskiest states for billing fraud. Delaware, Oregon, Florida, New York and California are the top five riskiest states for shipping fraud, accounting for 50 percent of total fraud attacks. South El Monte, Calif., is the riskiest city overall, with an increase in shipping fraud of approximately 230 percent. Shipping fraud most often occurs near major airports and seaports due to reshippers and freight forwarders that receive domestic goods and often send them overseas. When a transaction originates from an international IP address, shipping fraud is 6.7 times likelier than the average, while billing fraud becomes 7.1 times likelier. Where is e-commerce fraud happening? Typically, the highest-risk areas for fraud are in ZIP™ codes and cities near large ports of entry or airports. These are ideal locations to reship fraudulent merchandise, enabling criminals to move stolen goods more effectively. Top 10 riskiest billing ZIP™ codes Top 10 riskiest shipping ZIP™ codes 97252 Portland, OR 97079 Beaverton, OR 33198 Miami, FL 33122 Miami, FL 33166 Miami, FL 91733 South El Monte, CA 33122 Miami, FL 97251 Portland, OR 77060 Houston, TX 97250 Portland, OR 33195 Miami, FL 33166 Miami, FL 97250 Portland, OR 97252 Portland, OR 97251 Portland, OR 33198 Miami, FL 33191 Miami, FL 33195 Miami, FL 97253 Portland, OR 33192 Miami, FL Source: Experian.com Source: Experian.com What’s more, many of the riskiest ZIP™ codes and cities experience a high volume of transactions originating from international IP addresses. In fact, the top 10 riskiest ZIP codes overall tend to experience fraudulent activity from numerous countries overseas, including China, Venezuela, Taiwan and Hong Kong, and Argentina. These fraudsters tend to implement complex fraud schemes that can cost businesses millions of dollars in fraud losses. Additionally, the analysis shows that traffic coming from a proxy server — which could originate from domestic and international IP addresses — is 74 times riskier than the average transaction. The problem The increase in e-commerce fraud attacks shouldn’t come as a huge surprise. The uptick in data breaches, merchants’ continued adoption of EMV-enabled terminals to protect against counterfeit card fraud and the abundance of consumer data on the dark web means that information is even more accessible to criminals. This enables them to open fraudulent accounts, take over legitimate accounts and submit fraudulent transactions. Another reason for the increase is automation. In the past, criminals needed a strong understanding of fraud methods and technology, but they can now bring down an entire organization by simply downloading a file and automating the submission of thousands of applications or transactions simultaneously. Since fraudsters need to make these transactions appear as normal as possible, they often leverage the cardholder’s actual billing details with slight differences, such as e-mail address or shipping location. Unfortunately, the mass availability of compromised data and the abundance of fraudsters makes it increasingly challenging to identify and separate legitimate customers from attackers across the country. Because of the widespread prevalence of fraud and data compromises, we don’t see billing fraud concentrated in just one region of the country. In fact, the top five states for billing fraud make up only about 18 percent of overall fraud attacks. Top 5 riskiest billing fraud states Top 5 riskiest shipping fraud states State Fraud attack rate State Fraud attack rate Delaware 93.4 Delaware 195.9 Oregon 86.1 Oregon 170.1 Washington, D.C. 46.5 Florida 45.1 Florida 39.2 New York 37.3 Georgia 31.5 California 32.6 Source: Experian.com Source: Experian.com Prevention and protection need to be the priority As businesses get a better understanding of how and where fraud is perpetrated, they can implement proactive strategies to detect and prevent attacks, as well as protect payment information. While no one single strategy can address the entire scope of fraud, there are advanced data sets and technology — such as device intelligence, behavioral and physical biometrics, document verification and entity resolution — that can help businesses make better fraud decisions. Fortunately, consumers can also play a major role in safeguarding their information. In addition to regularly checking their credit reports and bank/credit card statements for fraudulent activity, consumers can limit the data they share on social networking sites, where attackers often begin when perpetrating identity fraud. While we continue to help both organizations and consumers limit their exposure to e-commerce fraud, we anticipate that criminals will attempt more sophisticated fraud schemes. But businesses can stay ahead of the curve. This comes down to having a keen understanding of how fraud is being perpetrated, as well as leveraging data, technology and multiple layered strategies to better recognize legitimate customers and make more precise fraud decisions. View our e-commerce fraud heat map and download the top 100 riskiest ZIP codes in the United States. Experian is a nonexclusive full-service provider licensee of the United States Postal Service®. The following trademark is owned by the United States Postal Service®: ZIP. The price for Experian’s services is not established, controlled or approved by the United States Postal Service.

Managing your customer accounts at the identity level is ambitious and necessary, but possible Identity-related fraud exposure and losses continue to grow. The underlying schemes have elevated in complexity. Because it’s more difficult to perpetrate “card present” fraud in the post–chip-and-signature rollout here in the United States, bad guys are more motivated and getting better at identity theft and synthetic identity attacks. Their organized nefarious response takes the form of alternate attack vectors and methodologies — which means you need to stamp out any detected exposure point in your fraud prevention strategies as soon as it’s detected. Experian’s recently published 2018 Global Fraud and Identity Report suggests two-thirds, or 7 out of every ten, consumers want to see visible security protocols when they transact. But an ever-growing percentage of them, fueled in no small part by those tech-savvy millennials, expect to be recognized with little or no friction. In fact, 42 percent of the surveyed consumers who stated they would do more transactions online if there weren’t so many security hurdles to overcome were — you guessed it — millennials. So how do you implement identity and account management procedures that are effective and, in some cases, even obvious while being passive enough to not add friction to the user experience? In other words, from the consumer’s perspective, “Let me know you know me and are protecting me but not making it too difficult for me when I want to access or manage my account.” Let’s get one thing out of the way first. This isn’t a one-time project or effort. It is, however, a commitment to the continued informing of your account management strategies with updated identity intelligence. You need to make better decisions on when to let a low-risk account transaction (monetary or nonmonetary) pass and when to double down a bit and step up authentication or risk assessment checks. I’d suggest this is most easily accomplished through a single, real-time access point to myriad services that should, at the very least, include: Identity verification and reverification checks for ongoing reaffirmation of your customer identity data quality and accuracy. Know Your Customer program requirements, anyone? Targeted identity risk scores and underlying attributes designed to isolate identity theft, first-party fraud and synthetic identity. Fraud risk comes in many flavors. So must your analytics. Device intelligence and risk assessment. A customer identity is no longer just their name, address, Social Security number and date of birth. It’s their phone number, email address and the various devices they use to access your services as well. Knowing how that combination of elements presents itself over time is critical. Layered passive or more active authentication options such as document verification, biometrics, behavioral metrics, knowledge-based verification and alternative data sources. Ongoing identity monitoring and proactive alerting and segmentation of customers whose identity risk has shifted to the point of required treatment. Orchestration, workflow and decisioning capabilities that allow your team to make sense of the many innovative options available in customer recognition and risk assessment — without a “throw the kitchen sink at this problem” approach that will undoubtedly be way too costly in dollars spent and good customers annoyed. Fraud attacks are dynamic. Your customers’ perceptions and expectations will continue to evolve. The markets you address and the services you provide will vary in risk and reward. An innovative marketplace of identity management services can overwhelm. Make sure your strategic identity management partner has good answers to all of this and enables you to future-proof your investments.

I recently sat down with Kathleen Peters, SVP and Head of Fraud and Identity, to discuss the state of fraud and identity, the pace of change in the space and her recent inclusion in the Top 100 influencers in Identity by One World Identity. ----------- Traci: Congratulations on being included on the Top 100 influencers list. What a nice honor. Kathleen: Yes, thank you. It is a nice honor and inspiring to be included among some great innovators in the industry. The list includes entrepreneurs to leaders of large organizations like us. It’s a nice mix across all facets of identity. T: Tell me about your role. How long have you been at Experian? K: I lead the team that defines the product strategy for our global fraud and ID portfolio. I’ve been with Experian just over four years, joining soon after we acquired 41st Parameter®. T: What was your first job? K: My first job out of college was with Motorola in Chicago. I was an electrical engineer, working on advanced cellphone technology. T: They were not able to keep up with the market? K: The entire industry was caught by the introduction of the iPhone. All the major cellphone companies were impacted — Nokia, Ericsson, Siemens and others. Talk about disrupting an industry. T: Yeah. These are great examples of how the disrupters have taken out the initial companies. Certainly, Motorola, Nokia, those companies. Even RIM Blackberry, which redefined the digital or cellular space, has all but disappeared. K: Yes, exactly. It was interesting to watch RIM Blackberry when they disrupted Motorola’s pager business. Motorola had a very robust pager line. Even then they had a two-way pager with a keyboard. They just missed the idea of mobile email completely. It’s really, really fascinating to look back now. T: Changing the subject a little, what motivates you to get out of bed in the morning? K: One of my favorite questions. I’m a very purpose-driven person. One of the things I really like about my role and one of the reasons I came to Experian in the first place is that I could see this huge potential within the company to combine offline and online identity information and transaction information to better recognize people and stop fraud. T: What do you see as the biggest threat to organizations today? K: I would have to say the pace of change. As we were just talking about, major industries can be disrupted seemingly overnight. We’re in the midst of a real digital transformation in how we live, how we work, how we share information and even how we share money. The threat to companies is twofold. One is the “friendly fire” threat, like the pace of change, disrupters to the market, new ways of doing things and keeping pace with that innovation. The second threat is that with digitization comes new types of security and fraud risks. Today, organizations need to be ever-vigilant about their security. T: How do you stay ahead of that pace of change? K: Well, my husband and I have lived in Silicon Valley since 1997. Technology and innovation are all around us. We read about it and we hear about it in the news. We engage with our neighbors and other people who we meet socially and within our networks. You can’t help but be immersed in it all the time. It certainly influences the way we go about our lives and how we think and act and engage as a family. We’re all technically curious. We have two kids, and our neighborhood high school, Homestead High, is the same high school Steve Jobs went to. It’s fun that way. T: Definitely. What are some of the most effective ways for businesses to combat the threat of fraud? K: I firmly believe that nowadays it all needs to start with identity. What we’ve found — and confirmed through research in our recent Global Fraud Report, plus conversations I’ve had with clients and analysts — is that if you can better recognize someone, you’ll go a long way to prevent fraud. And it does more than prevent fraud; it provides a better experience for the people you’re engaged with. Because once you recognize an individual, that initiates a trusted relationship between the two of you. Once people feel they’re in a trusted relationship, whether it’s a social relationship or a financial transaction, whatever the relationship is — once you feel trusted, you feel safe, you feel protected. And you’re more likely to want to engage again in the future. I believe the best thing organizations can do is take a multilayered approach to authenticating and identifying people upfront. There are so many ways to do this digitally without disrupting the consumer, and this is the best opportunity for businesses. If we collectively get that right, we’ll stop fraud. T: What are some of the things Experian is focusing on to help businesses stop fraud? K: We’ve focused on our CrossCore® platform. CrossCore is a common access and decisioning capability platform that allows the combining and layering of many different approaches — some active, some passive — to identify a customer in a transaction. You can incorporate things like biometrics and behavioral attributes. You can incorporate digital information about the device you’re engaging with. You can layer in online and offline identity information, like that from our Precise ID® product. CrossCore also enables you to layer in other digital attributes and alternative data such as email address, phone number and the validity of that phone number. CrossCore provides a great opportunity for us to showcase innovation, whether that comes from a third-party partner or even from our own Experian DataLabs. T: How significant do you see machine learning moving forward? K: Machine learning, it has all kinds of names, right? I think of machine learning, artificial intelligence, data robotics, parallel computing — all these things are related to what we used to call big data processing, but that’s not really the trendy term anymore. The point is that there is so much data today. There’s a wealth of data from all different sources, and as a society we’re producing it in exponential volumes. Having more and more and more data is not useful if you can’t derive insights from it. That’s why machine learning, augmented with human intervention or direction, is the best way forward, because there’s so much data out there available in the world now. No matter what problem we’re trying to solve, there’s a wealth of data we can amass, but we need to make sense of it. And the way to make sense of massive amounts of data in a reasonable amount of time is by using some sort of artificial intelligence, or machine learning. We’re going to see it in all kinds of applications. We already are today. So, while I think of machine learning as a generic term, I do think it’s going to be with us for a while to quickly compute and derive meaningful insights from the massive amounts of data all around us. T: Thanks, okay. Last question, and I hope a little fun. How would you describe yourself in one word? K: Curious. T: Ah, that’s a good choice. K: I am always curious. That’s why I love living where I live. It’s why I like working in technology. I’ve always wondered how things work, how we might improve on them, what’s under the hood. Why people make the decisions they do. How does someone come up with this? I’m always curious. T: Well, thank you for the time, and congrats again on being included in the Top 100 influencers in Identity.

Experian® is honored to be an MRC Technology Award nominee. But we can’t win the MRC People’s Choice Award without your help! The annual MRC Technology Awards recognize the most elite solution providers making significant contributions in the fraud, payments and risk industries. CrossCore® is the first smart, open, plug-and-play platform for fraud and identity services. We know, and our clients agree, that it delivers a better way to modify strategies quickly, catch fraud faster, improve compliance and enhance the customer experience. Need further convincing? Here are the top 3 reasons you should vote for CrossCore. Reason 1: common access Manage your entire fraud and identity portfolio. Start immediately by turning on Experian services through a single integration. Connect to services quickly with a common, flexible API. Reason 2: open approach Control the data being used in decisions. CrossCore supports a best-in-class approach to managing a portfolio of services that work together in any combination — including Experian solutions, third-party services and client systems — delivering the level of confidence needed for each transaction. Reason 3: workflow decisioning Act quickly and adapt to new risks with built-in strategy design and workflow capabilities. You can precisely tailor strategies based on transaction type or risk threshold. Make changes dynamically, with no downtime. We hope you’ll vote for CrossCore as a better way to manage fraud prevention and identity services.

Experian on the State of Identity podcast In today’s environment, any conversation on the identity management industry needs to include some mention of synthetic identity risk. The fact is, it’s top of mind for almost everyone. Institutions are trying to scope their risk level and identify losses, while service providers are innovating ways to solve the problem. Even consumers are starting to understand the term, albeit via a local newscast designed to scare the heck out of them. With all this in mind, I was very happy to be invited to speak with Cameron D’Ambrosi at One World Identity (OWI) on the State of Identity podcast, focusing on synthetic identity fraud. Our discussion focused on some of the unique findings and recommended best practices highlighted in our recently published white paper on the subject, Synthetic identities: getting real with customers. Additionally, we discussed how a lack of agreement on the definition and size of the synthetic identity problem further complicates the issue. This all stems from inconsistent loss reporting, a lack of confirmable victims and an absence of an exact definition of a synthetic identity to begin with. Discussions must continue to better align us all. I certainly appreciate that OWI dedicated the podcast to this subject. And I hope listeners take away a few helpful points that can assist them in their organization’s efforts to better identify synthetic identities, reduce financial losses and minimize reputation risks.

As we enter the holiday season, headlines abound around the shifts and trends in retail. How are consumers shopping? What are they buying online versus in-store? How can retailers maintain share and thrive? To gain some fresh perspective on the retail space, we interviewed John Squire, CEO and co-founder of DynamicAction, a business featuring advanced analytics solutions designed specifically for eCommerce, store and omnichannel retail teams. Squire has had a tenured career in the retail and technology sectors serving in key executive roles for IBM Smarter Commerce and Coremetrics. He has spent the past decade guiding nearly every retail brand to a better understanding of their customers and utilization of their data to make profitable decisions. Business headlines claim we are in the midst of a retail apocalypse. Is this statement a reality? The reality is that retail is in a renaissance – a revolution driven by the most empowered, connected consumer in history, a burgeoning technology infrastructure and retail tech innovators who have disrupted the status quo. The most agile of retailers and brands are leaning forward to serve their customer with remarkable experiences in the store, online and anywhere the customer decides to interact with the brand. And for those retailers, the days ahead are filled with newfound opportunity. However, the retailers and brands who don’t have a strong core purpose beyond being filler between anchor stores may no longer have a place in this new world of retail. The strongest retailers and brands will tap into their wealth of customer data to better understand, and therefore better serve their customers, creating long-term relationships. They should only continue gain in strength as consumers concentrate more and more of their time (and wallets) with businesses that passionately focus on their unique needs and buying patterns. It seems like shoppers are increasingly turning online to make their purchases. Is this the case, and do we see seasonal spikes with this trend? The key for successful retailers is to understand that customers aren’t just searching, browsing, buying and returning online OR in-store. They are shopping online AND in-store … and even online while in-store. Shoppers simply do not see channels, and the sooner that retailers reorganize their mindset, their organizations and their data understanding around this reality, the more successful they will become. Shoppers are indeed moving online with increasing frequency and larger amounts of their overall spending. Connecting data across the enterprise, across their partners and across social channels is critical in enabling their retailing teams to make decisions on how best to simultaneously serve their customers and their company’s shareholders. If retailers have a store credit card to offer to consumers, how can they encourage use and get them to maximize spend? Are there particular strategies they should employ? As with any loyalty program or service item, consumers are looking for tools and offers they value. Therein lies the opportunity and the challenge. Value can come in many forms, depending on the individual. Does the credit card offer travel or retail points, or dollars that they can accumulate? Does the credit card save them time? Provide them with additional purchasing power? Reduce their friction of making large purchases? Increase the security of the initial purchase and long-time use of the product or service? The competition for just a consumer’s current and future wallet is being upended by retailing offers that are serving up entertainment, services, convenience and broader product selections. Understanding the high-value activities correlated to their VIP consumers generating the highest amount of profit for the business is the essential to building strategies for encouraging card use. Beyond online shopping, are there other retail trends you see emerging in the coming year? What excites you about the space? Online shopping is not a trend; it is retail’s greatest disruption of the last 100 years. Digitization of shopping in both the online and store setting is what thrills me. One to watch is Wal-mart. The company is taking a highly energized track to build a business of next-gen brands and using their supply chain acumen to battle Amazon, while simultaneously gaining huge amounts of market share from other less sophisticated and strong retailers. In addition, seeing how next-gen brands like Warby Parker, Everlane, Untuckit, Bonobos, Indochino and Rent the Runway are rapidly building out a store experience, albeit radically different than the stores of the past, is exciting to watch. Seeing the growth in Drone deliveries outside the US for retail and commercial applications is surely the next big jump for ‘Next Hour’ in-home delivery. Made-to-order with a very short lead-time is also a big trend to keep an eye on. However, what excites me most in the industry is the universal mind shift that is becoming undeniable in retail: that data understanding and action will be the very basis for customer centricity and companies’ growth. Retailers have had access to these data pools for ages, but the ability to sync the data sets across channels, make sense of the findings and take action at the speed the consumer expects is truly the next leap forward for great retailers. To learn more about the state of retail credit cards, access our latest report.

The data to create synthetic identities is available. And the marketplace to exchange and monetize that data is expanding rapidly. The fact that hundreds of millions of names, addresses, dates of birth, and Social Security numbers (SSNs) have been breached in the last year alone, provides an easy path for criminals to surgically target new combinations of data. Armed with an understanding of the actual associations of these personally identifiable information (PII) elements, fraudsters can better navigate the path to perpetrate identity theft, identity manipulation, or synthetic identity fraud schemes on a grand scale. Using information such as birth dates and addresses in combination with Social Security numbers, criminals can target new combinations of data to yield better results with lower risk of detection. Some examples of this would be: identity theft, existing account takeovers, or the deconstruction and reconstruction of those PII elements to better create effective synthetic identities. Experian has continued to evolve and innovate against fraud risks and attacks with an understanding of attack rates, vectors, and the shifting landscape in data availability and security. In doing so, we’ve historically operated under the assumption that all PII is already compromised in some way or is easily done so. Because of this, we employ a layered approach, providing a more holistic view of an identity and the devices that are used over time by that identity. Relying solely on PII to validate and verify an identity is simply unwise and ineffective in this era of data compromise. We strive to continuously cultivate the broadest and most in-depth set of traditional, innovative and alternative data assets available. To do this, we must enable the integration of diverse identity attributes and intelligence to balance risk, while maintaining a positive customer experience. It’s been quite some time since the use of basic PII verification alone has been predictive of identity risk or confidence. Instead, validation and verification is founded in the ongoing definition and association of identities, the devices commonly used by those individuals, and the historical trends in their behavior. Download our newest White Paper, Synthetic Identities: Getting real with customers, for an in-depth Experian perspective on this increasingly significant fraud risk.

Earlier this week, Javelin Strategy & Research announced its inaugural edition of the 2017 Identity Proofing Platform Awards. We were honored to see CrossCore as the leader – taking the award for the best overall identity proofing platform. According to the report, “Experian’s identity proofing platform is a strong performer in every category of Javelin’s FIT model. It is functional. It is innovative. And, most important, it is tailored toward the advisory’s expectations. The comprehensive nature of CrossCore makes it the market-leading solution for identity proofing.” It’s harder than ever to confidently identify your customers in today’s digital economy. You have lots of vendor solutions to choose from in the identity proofing space. And, now Javelin has made it much easier for you to select the partner that is right for your needs. Javelin’s newly minted Identity Proofing Platform Scorecard assesses current capabilities in the market to help you make that decision. And they have done a lot of the heavy lifting, looking across 23 vendors and scoring them based on three categories of their FIT model – functional, innovative, and tailored. Protecting customers is a priority for you – and for us. Here at Experian, we have a range of capabilities to help businesses manage identity proofing, and our CrossCore platform brings them all together. We launched CrossCore last year, with the goal of making the industry’s fraud and identity solutions work better for everyone. CrossCore delivers a future-proof way to modify strategies quickly, catch fraud faster, improve compliance and enhance the customer experience. We’re proud of the work we’ve done so far, integrating our products as well as adding more than 10 partners to the program. We’re pleased to see so many of our partners included in Javelin’s report. We’re working closely with our clients to pull in more partner capabilities, and further enhance our own platform to create a layered approach that supports a risk-based, adaptable strategy. As highlighted in the Javelin report, a reliance on traditional identity verification approaches are no longer sufficient or appropriate for digital channels. With CrossCore, our clients can choose the capabilities they want, when they want them, to dial in the right confidence level for each and every transaction. This is because CrossCore supports a layered approach to managing risk, allowing companies to connect multiple disparate services through a common access point. We are committed to making it easier for you to protect consumers against fraud. CrossCore is helping us all do just that.

Since the advent of the internet, our lives have changed drastically for the better. We can perform many of life’s daily activities from the comfort of our own home. According to Aite, in 2016 alone 36 million Americans made some form of mobile payment — paying a bill, purchasing something online, paying for fast food or making a mobile wallet purchase at a retailer. Simply put, the internet has made our lives easier. But with the good also comes the bad. While most consumers have moved to the digital world, so have fraudsters. With minimal risk and high reward at stake, e-commerce fraud attacks have increased dramatically over the last few years, with no signs of slowing down. We recently analyzed millions of transactions from the first half of 2017 to identify fraud attack rates based on billing and shipping addresses and broke down the findings into various geographic trends. Fraud attack rates represent the attempted fraudulent e-commerce transactions against the population of overall e-commerce orders. Consumers living out West and in the South have experienced more than their fair share of fraud. During the first half of 2017, the West and the South were the top two regions for both billing and shipping attacks. While both regions were at the top during the same time last year, the attacks themselves have increased substantially. Given the proximity to seaports and major international airports, this is somewhat unsurprising — particularly for shipping fraud — as many fraudsters will leverage reshippers to transport goods soon after delivery. .dataTb{margin:20px auto;width:100%}.dataTb:after{clear:both}.dataTb table{}.dataTb td,.dataTb th{border:1px solid #ddd;padding:.8em}.dataTb th{background:#F4F4F4}.tbL{float:left;width:49%}.tbR{float:right;width:49%;margin:0 0 0 2%} Shipping: Riskiest Regions Region Attack rate West 38.1 South 32.1 Northeast 27.0 North Central 20.7 Billing: Riskiest Regions Region Attack rate West 37.2 South 32.9 Northeast 27.3 North Central 24.0 At the state level, the top three shipping fraud states remained the same as 2016 — Delaware, Oregon and Florida — but the order changed. Oregon was the most targeted, with a fraud rate of 135.2 basis points, more than triple its rate at in the end of 2016. Though no longer in the top spot, Delaware saw alarming spikes as well, with shipping attack rates nearly triple last year’s rate at 128.6 basis points and billing attacks at 79.6 basis points. .dataTb{margin:20px auto;width:100%}.dataTb:after{clear:both}.dataTb table{}.dataTb td,.dataTb th{border:1px solid #ddd;padding:.8em}.dataTb th{background:#F4F4F4}.tbL{float:left;width:49%}.tbR{float:right;width:49%;margin:0 0 0 2%} Shipping: Riskiest States State Attack rate Oregon 135.2 Delaware 128.2 Florida 57.4 New York 45.0 Nevada 36.9 California 36.9 Georgia 33.5 Washington, D.C 30.8 Texas 29.6 Illinois 29.4 Billing: Riskiest States Region Attack rate Oregon 87.5 Delaware 79.6 Washington, D.C. 63.0 Florida 47.4 Nevada 38.8 California 36.9 Arkansas 36.6 New York 35.5 Vermont 34.2 Georgia 33.4 Diving a bit deeper, ZIPTM codes in Miami, Fla., make up a significant portion of the top 10 ZIP CodeTM lists for shipping and billing attacks — in fact, many of the same ZIP codes appear on both lists. The other ZIP Code that appears on both lists is South El Monte, Calif., which has a high percentage of industrial properties — common targets for fraudsters to ship packages, then reship overseas. You can download the top 100 riskiest Zip Codes in the U.S. for H1 2017. .dataTb{margin:20px auto;width:100%}.dataTb:after{clear:both}.dataTb table{}.dataTb td,.dataTb th{border:1px solid #ddd;padding:.8em}.dataTb th{background:#F4F4F4}.tbL{float:left;width:49%}.tbR{float:right;width:49%;margin:0 0 0 2%} Shipping: Top 10 riskiest ZIP™ Codes ZIP Code Attack rate 33122 [Miami, Fla.] 2409.4 91733 [South El Monte, Calif.] 1655.5 33198 [Miami, Fla.] 1295.2 33166 [Miami, Fla.] 1266.0 33195 [Miami, Fla.] 1037.3 33192 [Miami, Fla.] 893.9 97251 [Portland, Ore.] 890.6 07064 [Port Reading, NJ] 808.9 89423 [Minden, Nev.] 685.5 77072 [Houston, Tex.] 629.3 Billing: Top 10 riskiest ZIP™ Codes ZIP Code Attack rate 77060 [Houston, Tex.] 1337.6 33198 [Miami, Fla.] 1215.6 33122 [Miami, Fla.] 1106.2 33166 [Miami, Fla.] 1037.4 91733 [South El Monte, Calif.] 780.1 33195 [Miami, Fla.] 713.7 97252 [Portland, Ore.] 670.8 33191 [Miami, Fla.] 598.8 33708 [St. Petersburg, Fla.] 563.6 33792 [Miami, Fla.] 493.0 As e-commerce fraud continues to grow, businesses need to be proactive to keep themselves and their customers safe. That means incorporating multiple, layered fraud prevention strategies that work together seamlessly — for example, understanding details about users and their devices, knowing how users interact with the business and evaluating previous transaction history. This level of insight can help businesses distinguish real customers from nefarious ones without impacting the customer experience. While businesses are ultimately responsible for the safety of customers and their data, the onus doesn’t rest solely with them. Consumers should also be vigilant when it comes to protecting their digital identities and payment information. That means creating strong, unique passwords; actively monitoring online accounts; and using two-factor authentication to secure account access. At the end of the day, e-commerce fraud is a challenge that businesses and consumers will experience for the foreseeable future. But rising attack rates don’t have to spell doom and gloom for the industry. E-commerce growth is still extremely strong, as consumers interact through multiple channels (in-store, mobile and web) and expect a personalized experience. Establishing trust and verifying digital identities are key to meeting these latest expectations, which provide new opportunities for businesses and consumers to interact seamlessly and transact securely. With multiple safeguards in place, businesses have a variety of options to protect their customers and their brand reputation. Experian is a nonexclusive full-service provider licensee of the United States Postal Service®. The following trademarks are owned by the United States Postal Service®: ZIP and ZIP Code. The price for Experian’s services is not established, controlled or approved by the United States Postal Service.
