Travel

This article first appeared in Baseline Magazine Since it is possible for cyber-criminals to create a synthetic person, businesses must be able to differentiate between synthetic and true-party identities. Children often make up imaginary friends and have a way of making them come to life. They may come over to play, go on vacation with you and have sleepover parties. As a parent, you know they don’t really exist, but you play along anyway. Think of synthetic identities like imaginary friends. Unfortunately, some criminals create imaginary identities for nefarious reasons, so the innocence associated with imaginary friends is quickly lost. Fraudsters combine and manipulate real consumer data with fictitious demographic information to create a “new” or “synthetic” individual. Once the synthetic person is “born,” fraudsters create a financial life and social history that mirrors true-party behaviors. The similarities in financial activities make it difficult to detect good from bad and real from synthetic. There really is no difference in the world of automated transaction processing between you and a synthetic identity. Often the synthetic “person” is viewed as a thin or shallow file consumer— perhaps a millennial. I have a hard time remembering all of my own passwords, so how do organized “synthetic schemes” keep all the information usable and together across hundreds of accounts? Our data scientists have found that information is often shared from identity to identity and account to account. For instance, perhaps synthetic criminals are using the same or similar passwords or email addresses across products and accounts in your portfolio. Or, perhaps physical address and phone records have cross-functional similarities. The algorithms and sciences are much more complex, but this simplifies how we are able to link data, analytics, strategies and scores. Identifying the Business Impact of Synthetic-Identity Fraud Most industry professionals look at synthetic-identity fraud as a relatively new fraud threat. The real risk runs much deeper in an organization than just operational expense and fraud loss dollars. Does your fraud strategy include looking at all types of risk, compliance reporting, and how processes affect the customer experience? To identify the overall impact synthetic identities can have on your institution, you should start asking: Are you truly complying with \"Know Your Customer\" (KYC) regulations when a synthetic account exists in your active portfolio? Does your written \"Customer Identification Program\" (CIP) include or exclude synthetic identities? Should you be reporting this suspicious activity to the compliance officer (or department) and submitting a suspicious activity report (SAR)? Should you charge off synthetic accounts as credit or fraud losses? Which department should be the owner of suspected synthetic accounts: Credit Risk, Collections or Fraud? Do you have run any anti-money laundering (AML) risk when participating in money movements and transfers? Depending on your answers to the above questions, you may be incurring potential risks in the policies and procedures of synthetic identity treatment, operational readiness and training practices. Since it is possible to create a synthetic person, businesses must be able to differentiate between synthetic and true-party identities, just as parents need to differentiate between their child\'s real and imaginary friends.

Identity management traditionally has been made up of creating rigid verification processes that are applied to any access scenario. But the market is evolving and requiring an enhanced Identity Relationship Management strategy and framework. Simply knowing who a person is at one point in time is not enough. The need exists to identify risks associated with the entire identity profile, including devices, and the context in which consumers interact with businesses, as well as to manage those risks throughout the consumer journey. The reasoning for this evolution in identity management is threefold: size and scope, flexible credentialing and adaptable verification. First, deploying a heavy identity and credentialing process across all access scenarios is unnecessarily costly for an organization. While stringent verification is necessary to protect highly sensitive information, it may not be cost-effective to protect less-valuable data with the same means. A user shouldn’t have to go through an extensive and, in some cases, invasive form of identity verification just to access basic information. Second, high-friction verification processes can impede users from accessing services. Consumers do not want to consistently answer multiple, intrusive questions in order to access basic information. Similarly, asking for personal information that already may have been compromised elsewhere limits the effectiveness of the process and the perceived strength in the protection. Finally, an inflexible verification process for all users will detract from a successful customer relationship. It is imperative to evolve your security interactions as confidence and routines are built. Otherwise, you risk severing trust and making your organization appear detached from consumer needs and preferences. This can be used across all types of organizations — from government agencies and online retailers to financial institutions. Identity Relationship Management has three unique functions delivered across the Customer Life Cycle: Identity proofing Authentication Identity management Join me at Vision 2016 for a deeper analysis of Identity Relationship Management and how clients can benefit from these new capabilities to manage risk throughout the Customer Life Cycle. I look forward to seeing you there!
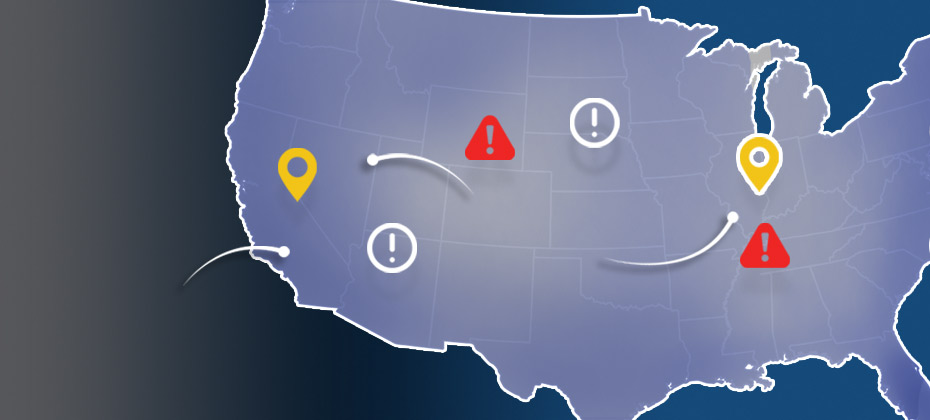
2015 data shows where billing and shipping e-commerce fraud attacks occur in the United States Experian e-commerce fraud attacks and rankings now available Does knowing where fraud takes place matter? With more than 13 million fraud victims in 2015,[1] assessing where fraud occurs is an important layer of verification when performing real-time risk assessments for e-commerce. Experian® analyzed millions of e-commerce transactions from 2015 data to identify fraud-attack rates across the United States for both shipping and billing locations. View the Experian map to see 2015 e-commerce attack rates for all states and download the top 100 ZIP CodeTMrankings. “Fraud follows the path of least resistance. With more shipping and billing options available to create a better customer experience, criminals attempt to exploit any added convenience,” said Adam Fingersh, Experian general manager and senior vice president of Fraud & Identity Solutions. “E-commerce fraud is not confined to larger cities since fraudsters can ship items anywhere. With the switch to chip enabled credit card transactions, and possible growth of card-not-present fraud, our fraud solutions help online businesses monitor their riskiest locations to prevent losses both in dollars and reputation in the near term.” For ease of interpretation, billing states are associated with fraud victims (the address of the purchaser) and shipping states are associated with fraudsters (the address where purchased goods are sent). According to the 2015 e-commerce attack rate data: Florida is the overall riskiest state for billing fraud, followed by Delaware; Washington, D.C.; Oregon and California. Delaware is the overall riskiest state for shipping fraud, followed by Oregon, Florida, California and Nevada. Eudora, Kan., has the overall riskiest billing ZIP Code (66025). The next two riskiest ZIPTM codes are located in Miami, Fla. (33178) and Boston, Mass. (02210). South El Monte, Calif., has the overall riskiest shipping ZIP Code (91733). The next four riskiest shipping ZIP codes are all located in Miami. Overall, five of the top 10 riskiest shipping ZIP codes are located in Miami. Defiance, Ohio, has the least risky shipping ZIP Code (43512). The majority of U.S. states are at or below the average attack rate threshold for both shipping and billing fraud, with only seven states — Florida, Oregon, Delaware, California, New York, Georgia and Nevada — and Puerto Rico ranking higher than average. This indicates that attackers are targeting consumers equally in the higher-risk states while leveraging addresses from both higher- and lower-risk states to ship and receive fraudulent merchandise. Many of the higher-risk states are located near a large port-of-entry city, including Miami; Portland, Ore.; and Washington, D.C., perhaps allowing criminals to move stolen goods more effectively. All three cities are ranked among the riskiest cities for both measures of fraud attacks. Neighboring proximity to higher-risk states does not appear to correlate to any additional risk — Pennsylvania and Rhode Island are ranked as two of the lower-risk states for both shipping and billing fraud. Other lower-risk states include Wyoming, South Dakota and West Virginia. Experian analyzed millions of e-commerce transactions to calculate the e-commerce attack rates using “bad transactions” in relation to the total number of transactions for the 2015 calendar year. View the Experian map to see 2015 e-commerce attack rates for all states and download the top 100 ZIP Code rankings. [1]According to the February 2016 Javelin study 2016 Identity Fraud: Fraud Hits an Inflection Point.

Loyalty fraud and the customer experience Criminals continue to amaze me. Not surprise me, but amaze me with their ingenuity. I previously wrote about fraudsters’ primary targets being those where they easily can convert credentials to cash. Since then, a large U.S. retailer’s rewards program was attacked – bilking money from the business and causing consumers confusion and extra work. This attack was a new spin on loyalty fraud. It is yet another example of the impact of not “thinking like a fraudster” when developing a program and process, which a fraudster can exploit. As it embarks on new projects, every organization should consider how it can be exploited by criminals. Too often, the focus is on the customer experience (CX) alone, and many organizations will tolerate fraud losses to improve the CX. In fact, some organization build fraud losses into their budgets and price products accordingly — effectively passing the cost of fraud onto the consumers. Let’s look into how this type of loyalty fraud works. The criminal obtains your login credentials (either through breach, malware, phishing, brute force, etc.) and uses the existing customer profile to purchase goods using the payment method on file for the account. In this type of attack, the motivation isn’t to receive physical goods; instead, it’s to accumulate rewards points — which can then be used or sold. The points (or any other form of digital currency) are instant — on demand, if you will — and much easier to fence. Once the points are credited to the account, the criminal cashes them out either by selling them online to unsuspecting buyers or by walking into a store, purchasing goods and walking right out after paying with the digital currency. A quick check of some underground forums validates the theory that fraudsters are selling retailer points online for a reduced rate — up to 70 percent off. Please don’t be tempted to buy these! The money you spend will no doubt end up doing harm, one way or another. Now, back to the customer experience. Does having lax controls really represent a good customer experience? Is building fraud losses into the cost of your products fair to your customers? The people whose accounts have been hacked most likely are some of your best customers. They now have to deal with returning merchandise they didn’t purchase, making calls to rectify the situation, having their personally identifiable information further compromised and having to pay for the loss. All in all, not a great customer experience. All businesses have a fiduciary responsibility to protect customer data with which they have been entrusted — even if the consumer is a victim of malware, phishing or password reuse. What are you doing to protect your customers? Simple authentication technologies, while nice for the CX, easily can fail if the criminal has access to the login credentials. And fraud is not a single event. There are patterns and surveillance activities that can help to detect fraud at every phase of your loyalty program — from new account opening to account logins and updates to transactions that involve the purchase of goods or the movement of currency. As fraudsters continue to evolve and look for the least-protected targets, loyalty programs have come to the forefront of the battleground. Take the time to understand your vulnerability and how you can be attacked. Then take the necessary steps to protect your most profitable customers — your loyalty program members. If you want to learn more, join us MRC Vegas 16 for our session “Loyalty Fraud; It’s Brand Protection, Not Just Loss Prevention” and hear our industry experts discuss loyalty fraud, why it’s lucrative, and what organizations can do to protect their brand from this grey-area type of fraud.

What is blockchain? Blockchain is beginning to get a lot of attention, so I thought it might be time to figure out what it is and what it means. Basically, a blockchain is a permissionless, distributed database that maintains a growing list of records (transactions) in a linear, chronological (and time-stamped) ledger. At a high level, this is how it works. Each computer connected to the network gets a copy of the entire blockchain and performs the task of validating and relaying transactions for the whole chain. The batches of valid transactions added to the record are called “blocks.” A block is the “current” part of a blockchain that records some or all of the recent transactions and once completed goes into the blockchain as a permanent database. Each time a block gets completed, a new block is created, with every block containing a hash of the previous block. There are countless numbers of blocks in the blockchain. To use a conventional banking analogy, the blocks would be a full history of every banking transaction for every person, and the blockchain would be a complete banking history. The entire blockchain is sent to everyone who has access, and every user validates the information in the block. It’s like if Tom, Bob and Harry were standing on the street corner and saw a cyclist hit by a car. Individually, all three men will be asked if the cyclist was struck by the car, and all three will respond “yes.” The cyclist being hit by the car becomes part of the blockchain, and that fact cannot be altered. Blockchain generally is used in the context of bitcoin, where similar uses of the structure are called altchains. Why should I care or, at the very least, pay attention to this movement? Because the idea of it is inching toward the tipping point of mainstream. I recently read an article that identified some blockchain trends that could shape the industry in coming months. The ones I found most interesting were: Blockchain apps will be released Interest in use cases outside payments will pick up Consortia will prove to be important Venture capital money will flow to blockchain start-ups While it’s true that much of the hype around blockchain is coming from people with a vested interest, it is beginning to generate more generalized market buzz as its proponents emphasize how it can reduce risk, improve efficiency and ultimately provide better customer service. Let’s face it, the ability to maintain secure, fast and accurate calculations could revolutionize the banking and investment industries, as well as ecommerce. In fact, 11 major banks recently completed a private blockchain test, exchanging multiple tokens among offices in North America, Europe and Asia over five days. (You can read The Wall Street Journal article here.) As more transactions and data are stored in blockchain or altchain, greater possibilities open up. It’s these possibilities that have several tech companies, like IBM, as well as financial institutions creating what has become known as an open ledger initiative to use the blockchain model in the development of new technologies that will enable a wider array of services. There is no doubt that the concept is intriguing — so much so that even the SEC has approved a plan to issue stock via blockchain. (You can read the Wired article here.) The potential is enough to make many folks giddy. The idea that risk could become a thing of the past because of the blockchain’s immutable historical record — wow. It’s good to be aware and keep an eye on the open ledger initiative, but let’s not forget history, which has taught us that (in the wise words of Craig Newmark), “Crooks are early adopters.” Since blockchain’s original and primary usage has been with bitcoin, I don’t think it is unfair to say that there will be some perceptions to overcome — like the association of bitcoin to activities on the Dark Web such as money laundering, drug-related transactions and funding illegal activities. Until we start to see the application across mainstream use cases, we won’t know how secure blockchain is or how open business and consumers will be to embracing it. In the meantime, remind me again, how long has it taken to get to a point of practical application and more widespread use of biometrics? To learn more, click here to read the original article.

Ensure you’re protecting consumer data privacy Data Privacy Day is a good reminder for consumers to take steps to protect their privacy online — and an ideal time for organizations to ensure that they are remaining vigilant in their fight against fraud. According to a new study from Experian Consumer Services, 93 percent of survey respondents feel identity theft is a growing problem, while 91 percent believe that people should be more concerned about the issue. Online activities that generate the most concern include making an online purchase (73 percent), using public Wi-Fi (69 percent) and accessing online accounts (69 percent). Consumers are vigilant while online Most respondents are concerned they will fall victim to identity theft in the future (71 percent), resulting in a generally proactive approach to protecting personal information. In fact, almost 50 percent of respondents say they are taking more precautions compared with last year. Ninety-one percent take steps to secure physical information, such as shredding documents, while also securing digital information (using passwords and antivirus software). Many consumers also make sure to check their credit report (33 percent) and bank account statements (76 percent) at least once per month. There’s still room for consumers to be safer Though many consumers are practicing good security habits, some aren’t: More than 50 percent do not check to see if a Website is secure Fifty percent do not have all their Web-enabled devices password-protected because it is a hassle to enter a password (30 percent) or they do not feel it is necessary (25 percent) Fifty-five percent do not close the Web browser when they are finished using an online account Additionally, 15 percent keep a written record of passwords and PINs in their purse or wallet or on a mobile device or computer Businesses need to be responsible when it comes data privacy Customer-facing businesses must continue efforts to educate consumers about their role in breach and fraud prevention. They also need to be responsible and apply comprehensive, data-driven intelligence that helps thwart both breaches and the malicious use of breached information and protect all parties’ interests. Nearly 70 percent of those polled in a 2015 Experian–Ponemon Institute study said that the increased visibility and media reporting of breaches, including payment-related incidents, have caused their organizations to step up data security efforts. Experian Fraud & ID is uniquely positioned to provide true customer intelligence by combining identity authentication with device assessment and monitoring from a single integrated provider. This combination provides the only true holistic view of the customer and allows organizations to both know and recognize customers and to provide them with the best possible experience. By associating the identities and the devices used to access services, the true identity can be seen across the customer journey. This unique and integrated view of identity and device delivers proven superior performance in authentication, fraud risk segmentation and decisioning. For more insights into how businesses are responding to breach activities, download our recent white paper, Data confidence realized: Leveraging customer intelligence in the age of mass data compromise. For more findings from the study, view the results here.

Looking at true fraud rate I’ve talked with many companies over the years about their fraud problems. Most have a genuine desire to operate under the fraud prevention model and eliminate all possible fraud from their systems. The impact on profit is often the primary motivation for implementing solutions, but in reality most companies employ a fraud management schema, offsetting the cost of fraud with the cost of managing it. There are numerous write-ups and studies on the true cost of fraud. What most people don’t realize is that, for each item lost to fraud, a business operating on 10 percent net profit margins will need to sell 10 times the amount of product in order to recover the expense associated with the loss. These hard costs don’t include the soft dollar costs, such as increased call center expenses to handle customer calls. Recently, some organizations have started to add reputational risk into their cost-of-fraud equation. With the proliferation of social media, a few unhappy customers who have been victims of fraud easily can impact an organization’s reputation. This is an emerging fuzzy cost that eventually can be tied back to lost revenue or a drop in share price. Most companies say with pride that their acceptable fraud rate is zero. But when it comes time to choose a partner in fraud detection, it almost always comes down to return on investment. How much fraud can be stopped — and at what price? More informed organizations take all operational expenses and metrics into consideration, but many look at vendor price as the only cost. It’s at this point that they start to increase their acceptable fraud rate. In other words, if — hypothetically — Vendor A can stop only 80 percent of the fraud compared with Vendor B, but Vendor A costs less than 80 percent of what Vendor B costs, they’ll choose Vendor A. All of a sudden, their acceptable fraud rate is no longer zero. This method of decision making is like saying we’ll turn off the security cameras for 20 percent of the day because we can save money on electricity. On the surface, I understand. You have to be accountable to the shareholders. You have to spend and invest responsibly. Everyone is under pressure to perform financially. How many executives, however, take the time to see where those lost dollars end up? If they knew where the money went, would they change their view? We must be vigilant and keep our acceptable fraud rate at zero.

Leveraging customer intelligence in the age of mass data compromise Hardly a week goes by without the media reporting a large-scale hack of sensitive personal or account information. Increasingly, the public seems resigned to believe that such compromises are the new normal, producing a kind of breach fatigue that may be lowering the expectations consumers have for identity and online security. Still, businesses must be vigilant and continue to apply comprehensive, data-driven intelligence that helps to thwart both breaches and the malicious use of breached information and to protect all parties’ interests. We recently released a new white paper, Data confidence realized: Leveraging customer intelligence in the age of mass data compromise, to help businesses understand how data and technology are needed to strengthen fraud risk strategies through comprehensive customer intelligence. At its core, reliable customer intelligence is based on high-quality contextual identity and device attributes and other authentication performance data. Customer intelligence provides a holistic, bound-together view of devices and identities that equips companies and agencies with the tools to balance cost and risk without increasing transactional friction and affecting the customer experience. In the age of mass data compromise, however, obtaining dependable information continues to challenge many companies, usually because consumer-provided identities aren’t always unique enough to produce fully confident decisioning. For more information, and to get a better sense of what steps you need to take now, download the full white paper.

Profile of an online fraudster I recently read a study about the profile of a cybercriminal. While I appreciate the study itself, one thing it lacks perspective on is an understanding of how identity data is being used to perpetrate fraud in the online channel. One may jump to conclusions about what is a good indicator for catching fraudsters. These very broad-brush observations may result in an overwhelming number of false positives without digging in deeper. Purchase value A single approach for understanding the correlation between purchase value and fraud does not work to best protect all businesses. Back in 2005, we saw that orders under $5 were great indicators of subsequent large-ticket fraud. For merchants that sell large-ticket items, such as electronics, those same rules may not be effective. To simply believe that the low dollar amount is the extent of the crime and not just a precursor to the real, bigger crime indicates a lack of understanding of how fraudsters work to manipulate a system. For some merchants, where fraudsters know they can go to do card testing against their business, low-dollar-amount rules may apply. However, for other businesses a different set of rules must be put into place. Time of day We have been tracking fraud time of day as a rule since 2004, but the critical point is a clear definition of which time of day. For the merchant, 3 a.m. is very different than 3 a.m. for a fraudster who is in Asia or Eastern Europe, where 3 a.m. merchant time is actually the middle of the online fraudster’s day. FraudNet is designed to identify the time from the user’s device and runs its rules from the user’s time. We find that every individual business will have a very specific threat profile. Businesses need to build their individual fraud strategy around their overall attack rate taking into account the strength of the defense and the ability to be flexible to accommodate the nuances for individual consumers. A general approach to fraud mitigation inevitably results in a system that begins to chase broad averages, which leads to excessive false positives and mediocre detection. That’s what drives us to do the job better. The proof of every fraud solution should lie in its ability to catch the most fraud without negatively impacting good customers.

What the EMV Shift means for you I recently facilitated a Webinar looking at myths and truths in the market regarding the EMV liability shift and what it means for both merchants and issuers. I found it to be a very beneficial discussion and wanted to take some time to share some highlights from our panel with all of you. Of course, if you prefer to hear it firsthand, you can download the archive recording here. Myth #1: Oct. 1 will change everything Similar to the hype we heard prior to Y2K, Oct. 1, 2015, came and went without too much fanfare. The date was only the first step in our long and gradual path to EMV adoption. This complex, fragmented U.S. migration includes: More than 1 billion payment cards More than 12 million POS terminals Four credit card networks Eighteen debit networks More than 12,000 financial institutions Unlike the shift in the United Kingdom, the U.S. migration does not have government backing and support. This causes additional fragmentation and complexity that we, as the payments industry, are forced to navigate ourselves. Aite Group predicts that by the end of 2015, 70 percent of U.S. credit cards will have EMV capabilities and 40 percent of debit cards will be upgraded. So while Oct. 1 may not have changed everything, it was the start of a long and gradual migration. Myth #2: Subscription revenues will plummet due to reissuances According to Aite, EMV reissuance is less impactful to merchant revenues than database breaches, since many EMV cards are being reissued with the same pan. The impact of EMV on reoccurring transactions is exaggerated in the market, especially when you look at the Update Issuer provided by the transaction networks. There still will be an impact on merchants, coming right at the start of the holiday shopping season. The need for consumer education will fall primarily on merchants, given longer lines at checkout and unfamiliar processes for consumers. Merchants should be prepared for charge-back amounts on their statements, which they aren’t used to seeing. Lastly, with a disparate credit and debit user experience, training is needed not just for consumers, but also for frontline cashiers. We do expect to see some merchants decide to wait until after the first of the year to avoid impacting the customer experience during the critical holiday shopping season, preferring to absorb the fraud in the interest of maximizing consumer throughout. Myth #3: Card fraud will decline dramatically We can look to countries that already have migrated to see that card fraud will not, as a whole, decline dramatically. While EMV is very effective at bringing down counterfeit card fraud, organized crime rings will not sit idly by while their $3 billion business disappears. With the Canadian shift, we saw a decrease in counterfeit card loss but a substantial increase in Card Not Present (CNP) fraud. In Canada and Australia, we also saw a dramatic, threefold increase in fraudulent applications. When criminals can no longer get counterfeit cards, they use synthetic and stolen identities to gain access to new, legitimate cards. In the United States, we should plan for increased account-takeover attacks, i.e., criminals using compromised credentials for fraudulent CNP purchases. For merchants that don’t require CVV2, compromised data from recent breaches can be used easily in an online environment. According to Aite, issuers already are reporting an increase in CNP fraud. Fraudsters did not wait until the Oct. 1 shift to adjust their practices. Myth #4: All liability moves to the issuer EMV won’t help online merchants at all. Fraud will shift to the CNP channel, and merchants will be completely responsible for the fraud that occurs there. We put together a matrix to illustrate where actual liability shifts and where it does not. Payments liability matrix Note: Because of the cost and complexity of replacing POS machines, gas stations are not liable until October 2017. For more information, or if you’d like to hear the full discussion, click here to view the archive recording, which includes a great panel question-and-answer session.
While walking through a toy store in search of the perfect gift for a nephew, I noticed the board game Risk, which touts itself as “The Game of Global Domination.” For those who are unaware, the game usually is won by players who focus on four key themes: Strategy — Before you begin the game, you need a strategy to attack new territories while defending your own Attack — While you have the option to sit back and defend your territory, it’s better to attack a weakened opponent Fortify — When you are finished attacking, it’s often best to fortify your position Alliances — While not an official part of the game, creating partnerships is necessary in order to win These themes also are relevant to the world of real-life fraud risk prevention. The difference is that the stakes are real and much higher. Let’s look at how these themes play out in real-life fraud risk prevention: Strategy — Like in the game, you need a strategy for fraud risk detection and prevention. That strategy must be flexible and adaptable since fraudsters (your enemies) also continuously adapt to changing environments, usually at a much quicker, less bureaucratic pace. For example, your competitors (other countries) may improve their defenses, so fraudsters will mount a more focused attack on you. Fraudsters also may build alliances to attack you from different vectors or channels, resulting in a more sophisticated, comprehensive strike. Attack — As the game begins, all players have access to all competitors (countries). This means that fraudsters might have the upper hand in a certain area of the business. You can sit back and try to defend the territory you already “own,” where fraudsters have no traction, but it’s best to be aggressive and attack fraudsters by expanding your coverage across all channels. For example, you might have plenty of controls in place to manage your Web orders (occupied territory), but your call center operations (opponents’ territory) aren’t protected, i.e., the fraudsters “own” this space. You need to attack that channel to drive fraudsters out. Fortify — In the game, you can fortify your position after a successful move — that is, move more troops to your newly conquered territories. In real life, you always have the option to fortify your position, and you should constantly look for ways to improve your controls. You can’t afford to maintain on your current position, because fraudsters constantly are looking for weaknesses. Alliances — In business, we often are hesitant to share information with our competitors. Fraudsters use this to their advantage. Just as fraudsters act in a coordinated fashion, so must we. Use all available resources and partners to shore up your defenses Leverage the power of consortium data Learn new methods from traditional competitors Always team up with internal and external partners to defend your territory If you apply these themes, you will be positioned for global domination in the fight against fraud risk. You can read more about fraud-prevention strategies in our recent ebook, Protecting the Customer Experience. As a side note, I’m always ready for a game of Risk, so contact me if you’re interested. But be forewarned — I’m competitive.

What will the EMV shift really mean for consumers and businesses here in the U.S.? Businesses and consumers across the U.S. are still adjusting to their new EMV credit cards. The new credit cards are outfitted with computer chips in addition to the magnetic strips to help prevent point-of-sale (POS) fraud. The new system, called EMV (which stands for Europay, MasterCard and Visa), requires signatures for all transactions. EMV is a global standard for credit cards. In the wake of the rising flood of large-scale data breaches at major retailers – and higher rates of counterfeit credit card fraud – chip-and-signature, as it is also called, is designed to better authenticate credit card transactions. Chip-and-signature itself is not new. It has been protecting consumers and businesses in Europe for several years and now the U.S. is finally catching up. But what will the EMV system really mean for consumers and businesses here in the U.S.? There is the potential for businesses that sell both offline and online, to see an increase in fraud that takes place online called Card Not Present (CNP) fraud. Will credit card fraud ever really be wiped out? Can we all stop worrying that large-scale point-of-sale breaches will happen again? Will the EMV shift affect holiday shopping and should retailers be concerned? Join us as we explore these questions and more on an upcoming Webinar, Chipping Away at EMV Myths. Our panel of experts includes: David Britton, Vice President, Industry Solutions, Experian Julie Conroy, Research Director, Aite Group Mike Klumpp, Director of Fraud Prevention, Citibank Moderated by: Keir Breitenfeld, Vice President, Product Management, Experian

Understanding and managing first party fraud Background/Definitions Wherever merchants, lenders, service providers, government agencies or other organizations offer goods, services or anything of value to the public, they incur risk. These risks include: Credit risk — Loosely defined, credit risk arises when an individual receives goods/services in exchange for a promise of future repayment. If the individual’s circumstances change in a way that prevents him or her from paying as agreed, the provider may not receive full payment and will incur a loss. Fraud risk — Fraud risk arises when the recipient uses deception to obtain goods/services. The type of deception can involve a wide range of tactics. Many involve receiving the goods/services while attributing the responsibility for repayment to someone else. The biggest difference between credit risk and fraud risk is intent. Credit risk usually involves customers who received the goods/services with intent to repay but simply lack the resources to meet their obligation. Fraud risk starts with the intent to receive the goods/services without the intent to repay. Between credit risk and fraud risk lies a hybrid type of risk we refer to as first-party fraud risk. We call this a hybrid form of risk because it includes elements of both credit and fraud risk. Specifically, first party fraud involves an individual who makes a promise of future repayment in exchange for goods/services without the intent to repay. Challenges of first party fraud First party fraud is particularly troublesome for both administrative and operational reasons. It is important for organizations to separate these two sets of challenges and address them independently. The most common administrative challenge is to align first-party fraud within the organization. This can be harder than it sounds. Depending on the type of organization, fraud and credit risk may be subject to different accounting rules, limitations that govern the data used to address risk, different rules for rejecting a customer or a transaction, and a host of other differences. A critical first step for any organization confronting first-party fraud is to understand the options that govern fraud management versus credit risk management within the business. Once the administrative options are understood, an organization can turn its attention to the operational challenges of first-party fraud. There are two common choices for the operational handling of first-party fraud, and both can be problematic. First party fraud is included with credit risk. Credit risk management tends to emphasize a binary decision where a recipient is either qualified or not qualified to receive the goods/services. This type of decision overlooks the recipient’s intent. Some recipients of goods/services will be qualified with the intent to pay. Qualified individuals with bad intentions will be attracted to the offers extended by these providers. Losses will accelerate, and to make matters worse it will be difficult to later isolate, analyze and manage the first party fraud cases if the only decision criteria captured pertained to credit risk decisions. The end result is high credit losses compounded by the additional first party fraud that is indistinguishable from credit risk. First party fraud is included with other fraud types. Just as it’s not advisable to include first party fraud with credit risk, it’s also not a good idea to include it with other types of fraud. Other types of fraud typically are analyzed, detected and investigated based on the identification of a fraud victim. Finding a person whose identity or credentials were misused is central to managing these other types of fraud. The types of investigation used to detect other fraud types simply don’t work for first-party fraud. First party fraudsters always will provide complete and accurate information, and, upon contact, they’ll confirm that the transaction/purchase is legitimate. The result for the organization will be a distorted view of their fraud losses and misconceptions about the effectiveness of their investigative process. Evaluating the operational challenges within the context of the administrative challenges will help organizations better plan to handle first party fraud. Recommendations Best practices for data and analytics suggest that more granular data and details are better. The same holds true with respect to managing first party fraud. First party fraud is best handled (operationally) by a dedicated team that can be laser-focused on this particular issue and the development of best practices to address it. This approach allows organizations to develop their own (administrative) framework with clear rules to govern the management of the risk and its prevention. This approach also brings more transparency to reporting and management functions. Most important, it helps insulate good customers from the impact of the fraud review process. First-party fraudsters are most successful when they are able to blend in with good customers and perpetrate long-running scams undetected. Separating this risk from existing credit risk and fraud processes is critical. Organizations have to understand that even when credit risk is low, there’s an element of intent that can mean the difference between good customers and severe losses. Read here for more around managing first party fraud risk.

Imagine the following scenario: an attacker acquires consumers’ login credentials through a data breach. They use these credentials to test account access and observe account activity to understand the ebbs and flows of normal cash movement – peering into private financial records – verifying the optimal time to strike for the most financial gain. Surveillance and fraud staging are the seemingly benign and often-transparent account activities that fraudsters undertake after an account has been compromised but before that compromise has been detected or money is moved. Activities include viewing balances, changing settings to more effectively cover tracks, and setting up account linkages to stage eventual fraudulent transfers. The unfortunate thing is that the actual theft is often the final event in a series of several fraudulent surveillance and staging activities that were not detected in time. It is the activity that occurs before theft that can severely undermine consumer trust and can devastate a brand’s reputation. Read more about surveillance, staging and the fraud lifecycle in this complimentary whitepaper.

Cont. Understanding Gift Card Fraud By: Angie Montoya In part one, we spoke about what an amazing deal gift cards (GCs) are, and why they are incredibly popular among consumers. Today we are going to dive deeper and see why fraudsters love gift cards and how they are taking advantage of them. We previously mentioned that it’s unlikely a fraudster is the actual person that redeems a gift card for merchandise. Although it is true that some fraudsters may occasionally enjoy a latte or new pair of shoes on us, it is much more lucrative for them to turn these forms of currency into cold hard cash. Doing this also shifts the risk onto an unsuspecting victim and off of the fraudster. For the record, it’s also incredibly easy to do. All of the innovation that was used to help streamline the customer experience has also helped to streamline the fraudster experience. The websites that are used to trade unredeemed cards for other cards or cash are the same websites used by fraudsters. Although there are some protections for the customer on the trading sites, the website host is usually left holding the bag when they have paid out for a GC that has been revoked because it was purchased with stolen credit card information. Others sites, like Craigslist and social media yard sale groups, do not offer any sort of consumer protection, so there is no recourse for the purchaser. What seems like a great deal— buying a GC at a discounted rate— could turn out to be a devalued Gift card with no balance, because the merchant caught on to the original scheme. There are ten states in the US that have passed laws surrounding the cashing out of gift cards. * These laws enable consumers to go to a physical store location and receive, in cash, the remaining balance of a gift card. Most states impose a limit of $5, but California has decided to be a little more generous and extend that limit to $10. As a consumer, it’s a great benefit to be able to receive the small remaining balance in cash, a balance that you will likely forget about and might never use, and the laws were passed with this in mind. Unfortunately, fraudsters have zeroed in on this benefit and are fully taking advantage of it. We have seen a host of merchants experiencing a problem with fraudulently obtained GCs being cashed out in California locations, specifically because they have a higher threshold. While five dollars here and ten dollars there does not seem like it is very much, it adds up when you realize that this could be someone’s full time job. Cashing out three ten dollar cards would take on average 15 minutes. Over the course of a 40-hour workweek it can turn into a six-figure salary. At this point, you might be asking yourself how fraudsters obtain these GCs in the first place. That part is also fairly easy. User credentials and account information is widely available for purchase in underground forums, due in part to the recent increase in large-scale data breaches. Once these credentials have been obtained, they can do one of several things: Put card data onto a dummy card and use it in a physical store Use credit card data to purchase on any website Use existing credentials to log in to a site and purchase with stored payment information Use existing credentials to log in to an app and trigger auto-reloading of accounts, then transfer to a GC With all of these daunting threats, what can a merchant do to protect their business? First, you want to make sure your online business is screening for both the purchase and redemption of gift cards, both electronic and physical. When you screen for the purchase of GCs, you want to look for things like the quantity of cards purchased, the velocity of orders going to a specific shipping address or email, and velocity of devices being used to place multiple orders. You also want to monitor the redemption of loyalty rewards, and any traffic that goes into these accounts. Loyalty fraud is a newer type of fraud that has exploded because these channels are not normally monitored for fraud— there is no actual financial loss, so priority has been placed elsewhere in the business. However, loyalty points can be redeemed for gift cards, or sold on the black market, and the downstream affect is that it can inconvenience your customer and harm your brand’s image. Additionally, if you offer physical GCs, you want to have a scratch off PIN on the back of the card. If a GC is offered with no PIN, fraudsters can walk into a store, take a picture of the different card numbers, and then redeem online once the cards have been activated. Fraudsters will also tumble card numbers once they have figured out the numerical sequence of the cards. Using a PIN prevents both of these problems. The use of GCs is going to continue to increase in the coming years— this is no surprise. Mobile will continue to be incorporated with these offerings, and answering security challenges will be paramount to their success. Although we are in the age of the data breach, there is no reason that the experience of purchasing or redeeming a gift card should be hampered by overly cautious fraud checks. It’s possible to strike the right balance— grow your business securely by implementing a fraud solution that is fraud minded AND customer centric. *The use of GC/eGC is used interchangeably
