What Is Phishing?
Quick Answer
Phishing is a type of scam that uses fake emails, texts, phone calls or other types of communication to trick victims into revealing sensitive information. The scammers’ goal may be to steal money, commit credit fraud or sell your personal data online.

Phishing is a type of scam that uses fraudulent texts, emails, phone calls or other types of communication to trick victims into revealing sensitive information. The ultimate goal of a phishing scam is often to steal a victim's money or commit identity theft.
Scammers make thousands of phishing attempts each day, according to the Federal Trade Commission (FTC), and they count on catching their victims off guard. Fortunately, you can defend yourself by learning about what phishing is, signs of phishing scams and how to avoid them. Here's what you need to know.
What Is Phishing?
Phishing is a type of scam that uses fake emails, texts, phone calls or other methods to steal information or money from victims. Scammers often commit phishing by impersonating a trusted business or organization, such as an online shopping platform, bank or government official. They may be attempting to defraud you or gather your personal data to steal your identity or sell it on the dark web.
How Does Phishing Happen?
Phishing often happens using social engineering tactics designed to pressure targets into acting quickly. For example, you might receive an email with a fake invoice for $400 in printing equipment. The possibility of being charged a lot of money puts you in a state of fear, which may compel you to quickly click a link to "review your order." The link may lead to a spoofed website that asks you to provide your bank account number or other sensitive personal information. Or, it may download malicious software, or malware, to your computer.
Because scammers push you to act before you've had the chance to think about their request, the best defense is to slow down before you decide whether and how to engage with a sender.
Learn more: What Is Personally Identifiable Information?
Types of Phishing Attacks
Phishing scams are an ever-evolving threat, with criminals constantly updating their approaches to take advantage of new technology. Here are some terms for different types of phishing attacks based on who the target is and the modes of communication the fraudster uses.
- Spear phishing: Spear phishing is a type of phishing that targets a specific person or group in an organization. It takes the opposite approach from phishing that blasts out mass emails or texts indiscriminately, casting a wide net in hopes that someone will take the bait. Spear phishing, instead, uses information it thinks will interest specific individuals to get them to click on an attachment or link.
- Whaling: Whaling is a phishing attack that targets high-level or high-profile business executives, such as CEOs. These victims are of high value to criminals because they may have access to vast amounts of sensitive data or money.
- Email spoofing: Email spoofing is when a scammer creates a fake email impersonating a trusted source, such as a company's CEO or a popular online shopping platform. In reality, these emails are designed to phish information from you. They may also include links or attachments containing malware.
- Smishing: A combination of "SMS" and "phishing," smishing uses text messages designed to trick you into sharing your sensitive data or into clicking on a malicious link.
- Vishing: A combination of the words "voice" and "phishing," vishing scams target victims using fraudulent phone calls, often including fake caller IDs.
- Quishing: Quishing is a relatively new form of phishing that uses QR codes that lead to harmful websites. Scammers may plant these malicious QR codes over authentic ones, such as on parking meters. Once you navigate to the site, you may be prompted to enter sensitive information, or your device may be infected with malware.
Learn more: What's the Difference Between Phishing, Smishing and Vishing?
Common Signs of Phishing
Here are some common red flags that could tip you off to a phishing attempt:
- Language that urges you to act quickly to avoid something, like account deletion or an expired home warranty
- Offers that seem too good to be true, like a free trip to Bora Bora
- Requests for sensitive information, account login credentials or money
- Spelling errors and unusual grammar
- Sender email addresses or phone numbers that seem unprofessional or unusual
- Suspicious or unusual email attachments and links
Learn more: The Latest Scams You Need to Be Aware Of
Example of a Phishing Attempt
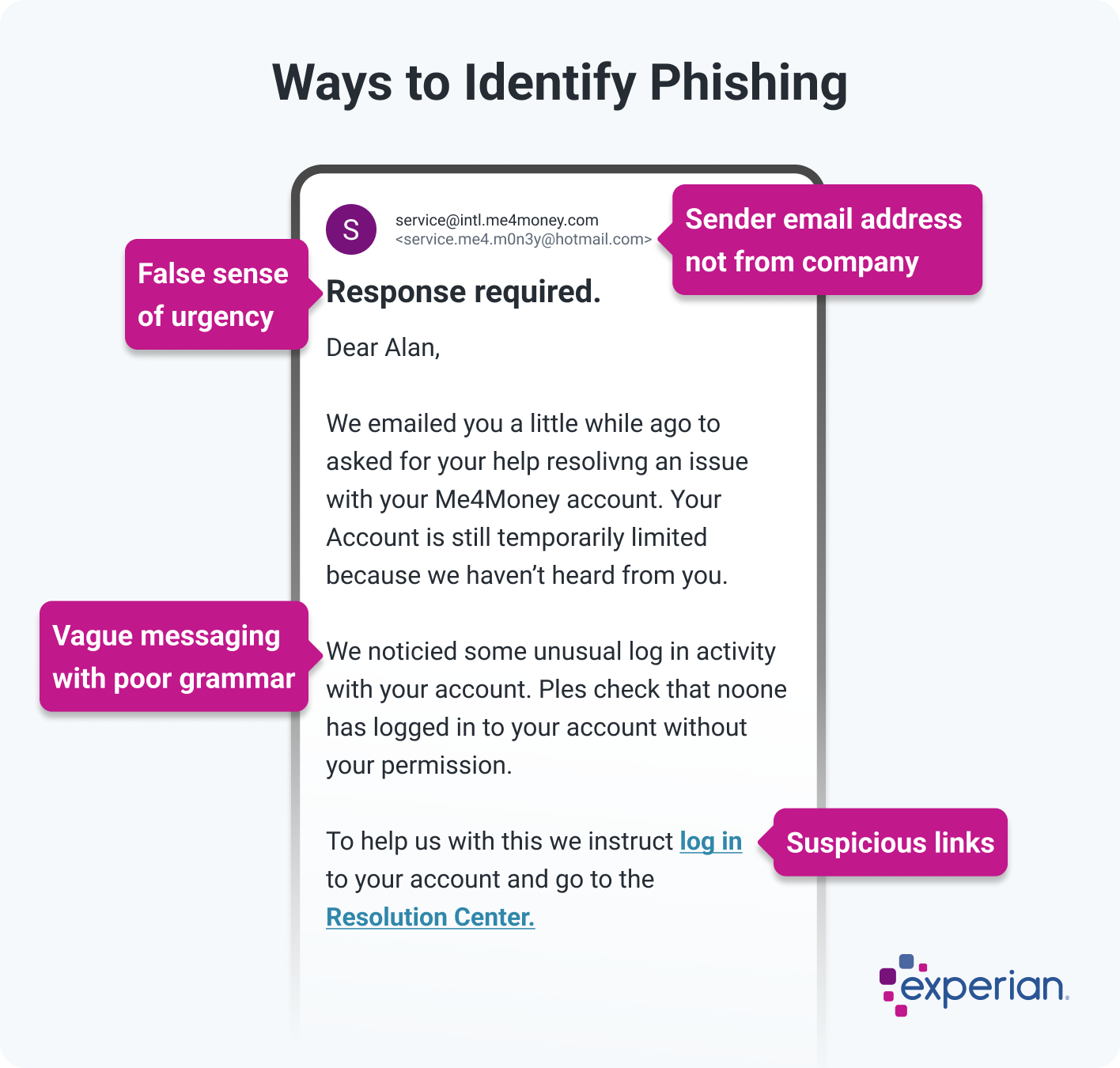
This scam email claims to be from a financial institution. In reality, it's a phishing attempt. Signs that this is a scam include:
- The sender's email address is a Hotmail domain, not a company domain.
- The subject line creates a false sense of urgency to get you to act.
- The body of the email includes vague messaging, which could be interpreted to actually reference your account but is just a way to get you to respond.
- It includes suspicious links, such as one that claims to send you to your account's login page.
- The email is rife with spelling and grammar errors, including "noticied" and "Ples," signs it did not come from an official company's email account.
How to Avoid Phishing Attacks
Scammers are constantly devising new phishing schemes in an effort to make it past their victims' defenses, so staying safe requires a multipronged approach. Applying these tips can help you up your guard and avoid phishing scams.
- Be skeptical. When in doubt, don't engage with texts, emails, phone calls or other communication from someone you can't confirm is who they say they are. Never give your Social Security number or financial information to someone who contacts you to ask for it.
- Contact organizations directly. If you get a phone call or message from someone claiming to be a trusted organization (such as your doctor or your bank), you don't have to interact with them. Instead, hang up and contact the organization using a number that you've looked up on your own or have on your account statements.
- Increase your accounts' security. Avoid reusing passwords: If a scammer gets access to one password, they could use it to get into other accounts that share it. A password manager can help you set and keep track of multiple hard-to-guess passwords. Also, enroll in multifactor authentication for an added layer of security.
- Don't click on suspicious links or attachments. Treat links and attachments with suspicion, and don't click any links or attachments in emails or texts from unknown senders. Deceptive links can lead to spoof websites designed to phish your information, or they could install malware to your device.
- Don't give in to pressure. Phishing attacks use psychological tactics meant to make you feel rushed into a decision, such as explicit or implied threats, or promises of prizes if you act now. Protect yourself by doing the opposite.
What to Do if You're the Victim of Phishing
Whether you've clicked a link that you believe could have infected your device with malware, or if you believe you may have exposed sensitive personal or financial information to a scammer, taking action right away is key to minimizing harm. Here are some next steps to consider.
- Notify affected companies or organizations. If your financial account information (such as your credit card or bank account number) is compromised, reach out to affected institutions right away. If your work devices or accounts were targeted in a phishing attack, follow your company's protocol for reporting the incident.
- Run an antivirus software scan. If you've clicked a suspicious link or attachment, run an antivirus scan to find and remove any harmful software. It's also a good idea to run these scans periodically as a defensive measure.
- Monitor your credit. Keep a close eye on your credit report, checking for any signs of credit fraud. You have the right to dispute items in your credit report that you don't recognize, such as new inquiries or accounts. Sign up for free credit monitoring through Experian to keep ongoing tabs on your credit.
- Place a fraud alert on your credit report. A fraud alert notifies lenders that you may be the target of scammers and requests that they take additional measures to verify your identity. You have the right to request a fraud alert as well as a security freeze, a more restrictive measure, for your credit reports with the three national credit bureaus (Experian, TransUnion and Equifax). When you place a fraud alert with one of the credit bureaus, the other two are notified automatically and a fraud alert is placed on those reports as well. To place a security freeze on your credit file, you'll need to contact each bureau separately.
- Report phishing attempts. Regardless of whether a scammer has successfully phished information from you or not, consider reporting the incident to the FTC at ReportFraud.ftc.gov.
Frequently Asked Questions
The Bottom Line
Phishing can have painful and lasting impacts, including financial loss, credit damage and the psychological toll of having your sense of security violated. The best preventive measure is awareness. Up your vigilance by staying informed on the latest scams. Beyond that, learning about cybersecurity best practices and other ways to avoid fraud can help you lower vulnerability to phishing.
Monitor your credit for free
Credit monitoring can help you detect possible identity fraud, and can prevent surprises when you apply for credit. Get daily notifications when changes are detected.
Get free monitoringAbout the author
Evelyn Waugh is a personal finance writer covering credit, budgeting, saving and debt at Experian. She has reported on finance, real estate and consumer trends for a range of online and print publications.
Read more from Evelyn